Query-Based Blocklists
Overview
Query-Based Blocklists allow GreyNoise customers to automatically generate and deploy IP blocklists based on real-world internet scanning and exploitation data. Using GNQL (GreyNoise Query Language) queries, users can fully customize these blocklists to match their organization’s security policies and enforcement needs.
Who Can Access Blocklists
- Available to: Standard, Advanced, and Elite platform customers
- Access is based on your data module entitlements
- Available in: GreyNoise Visualizer
How to Get Started
Access the Blocklist Menu
- Log in to the GreyNoise Visualizer.
- Open the Account menu in the top-right corner.
- Click on Blocklists.
Creating a Blocklist
You can create a Blocklist in two ways:
Start from the Blocklist tab
- Click Create Blocklist.
- This will take you to the search bar, where you can enter your GNQL query.
Start from a GNQL Search
- Enter any GNQL query into the search bar.
- Review the returned results.
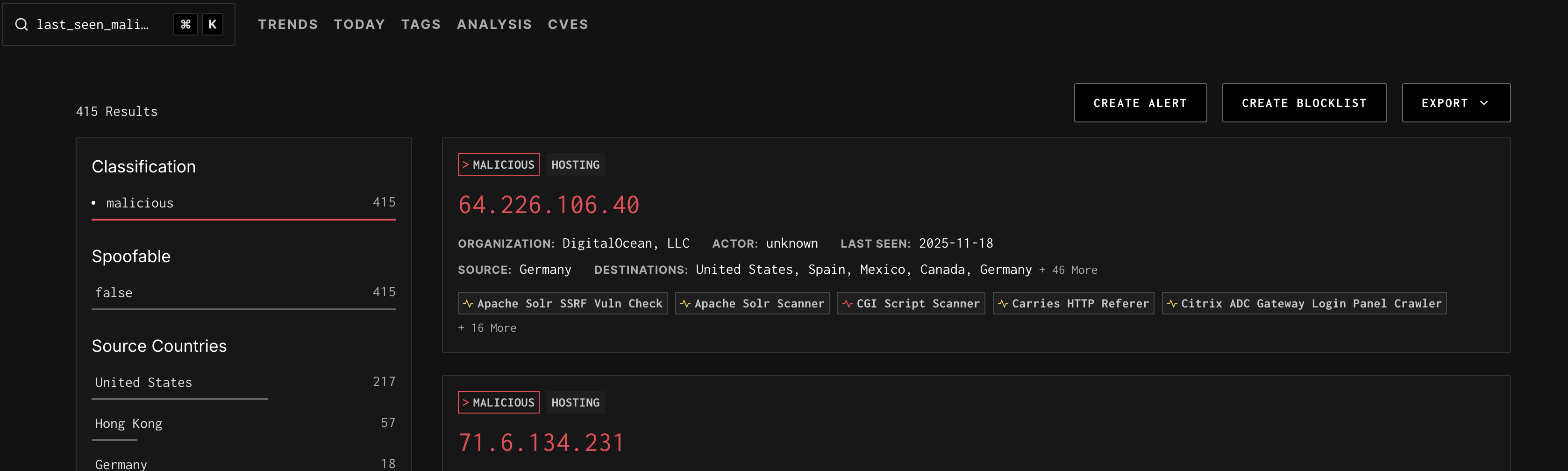
- If the results meet your needs, click 'Create Blocklist'.
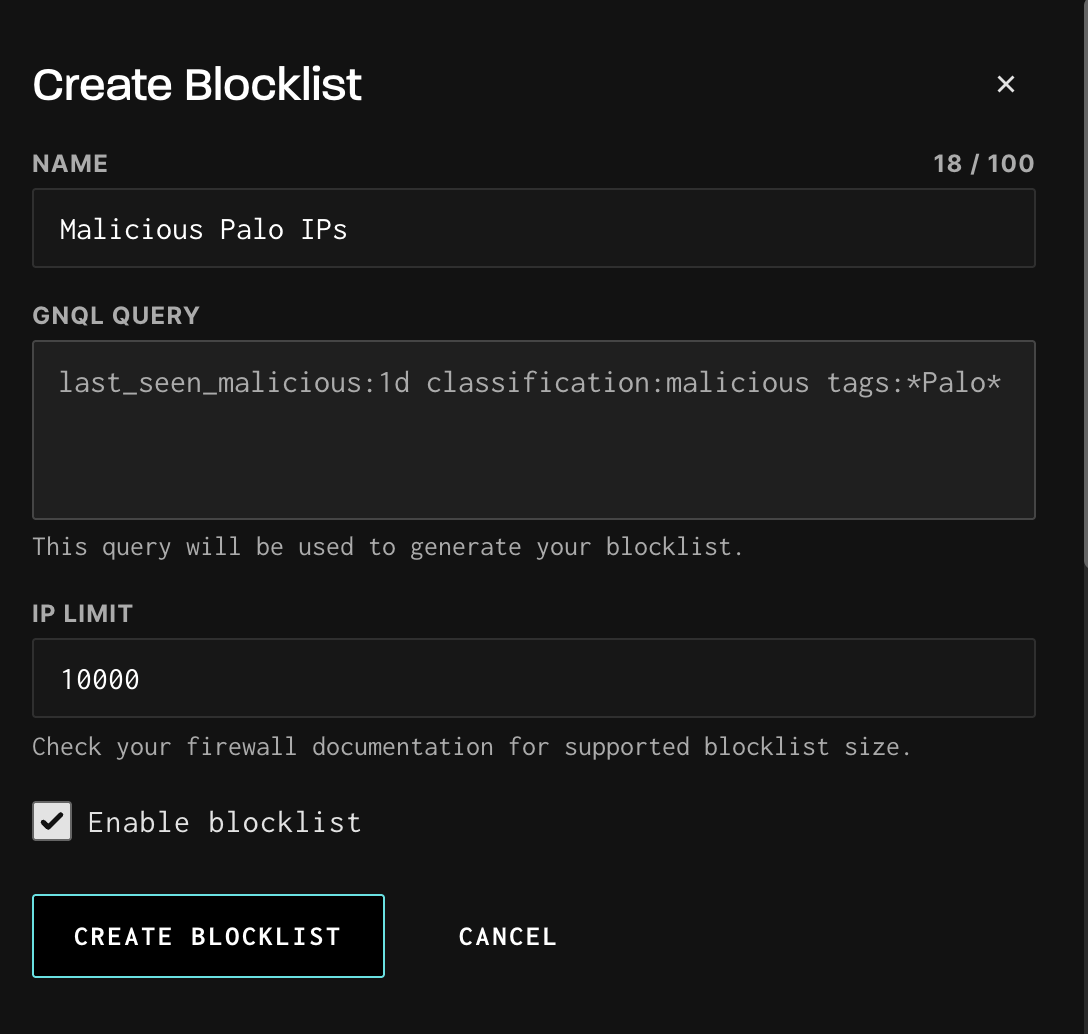
Click on “Create Blocklist”
- Name your blocklist clearly and descriptively.
- Confirm your GNQL query is correct and returns the expected IPs.
- Set an IP limit.
- Different firewalls support different maximum list sizes.
- Check your firewall vendor’s documentation and adjust accordingly.
- Click Create Blocklist to finalize.
Provisioning
- After creation, the blocklist enters a Provisioning state.
- Provisioning usually completes within 20–30 minutes.
- When ready, the blocklist status changes to Enabled.
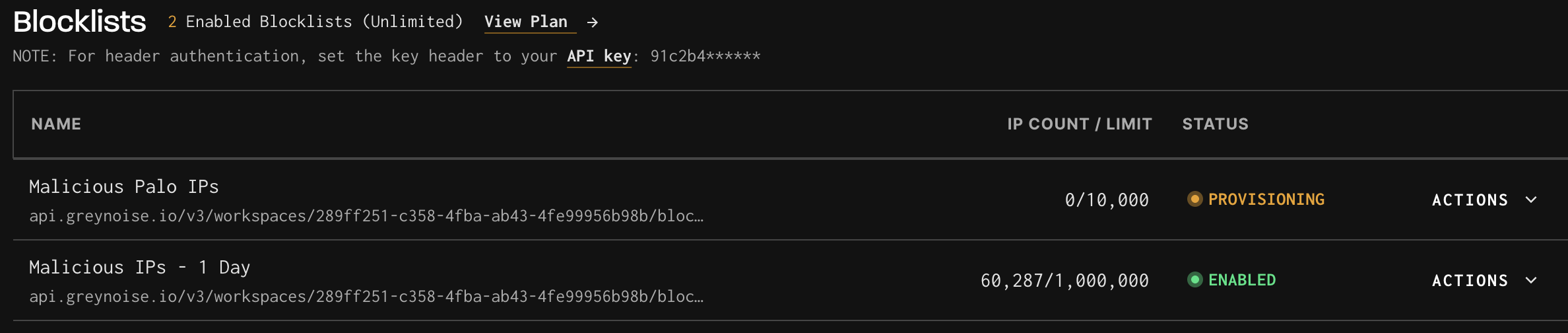
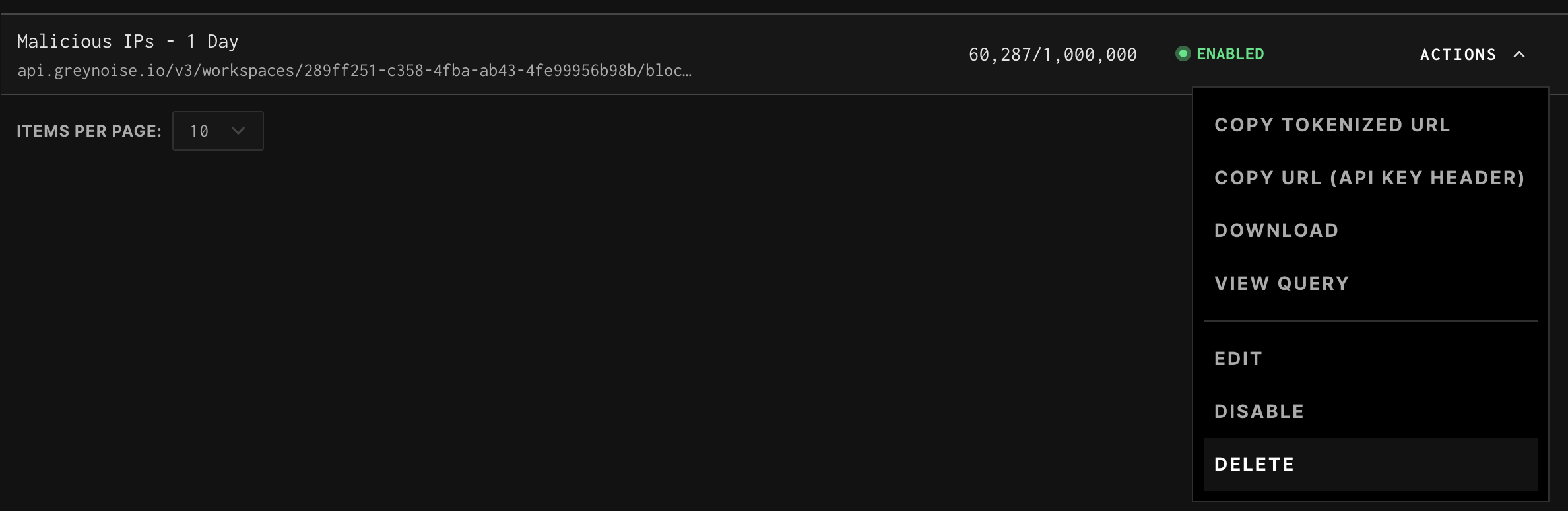
Actions
- Each blocklist includes the following actions:
- Copy Tokenized URL: A ready-to-use URL with embedded authentication token.
- Copy URL (API KEY HEADER): A URL requiring your API key to be passed as a header.
- Download: Downloads the current set of IPs in the blocklist.
- View Query: Opens the GNQL query and provides full IP and metadata visibility.
- Edit: Modify the GNQL query to update the blocklist’s logic.
- Disable: Temporarily stops dynamic updates while keeping the blocklist in your dashboard.
- Delete: Permanently removes the blocklist. (You’ll need to recreate it if you want it again later.)
Authentication
When adding blocklists to your firewalls or other tools, each blocklist requires you to use one of the following authentication methods:
- Use the tokenized URL that contains your credentials directly in the URL. This supports configurations where authentication options are unavailable or limited, and no header-based authentication is possible.
- Use header-based authentication, which requires you to include a key:API_KEY header with each request to the blocklist, as shown in the following example:
curl "BLOCKLIST_URL" -H "key:GREYNOISE_API_KEY"Blocklist Examples
Below are example GNQL queries that you can use to create common blocklists:
Recent Malicious or Suspicious Activity
last_seen_malicious:1d AND spoofable:false AND ((classification:suspicious) OR (classification:malicious))Recent Malicious Activity:
last_seen_malicious:1d AND spoofable:false AND classification:maliciousRecent Cisco-Tagged Activity:
last_seen_malicious:1d AND spoofable:false AND classification:malicious AND tags:_Cisco_Recent Palo Alto Tagged Activity:
last_seen_malicious:1d AND spoofable:false AND classification:malicious AND tags:_Palo\ Alto_Source Country Russia or China:
last_seen:1d AND spoofable:false AND (source_country:russia OR source_country:china)Updated 2 months ago
