SOAR Integration Overview: FortiNET FortiSOAR
Install From Connector Store
From the Automation -> Connector view, click the tab for the Connector Store. Use the magnifying glass icon to search for "greynoise" to find the connector. Click on the "GreyNoise" connector then click the "Install" button from the connector details display.
Add a Connector Configuration
From the Connector Details, on the Configurations tab, add a new connector configuration.
Settings:
- Configuration Name = Enter a name for this configuration
- Mark a Default = Select this checkbox if you want this to be your default configuration for this connector
- API Key Type = Select either "enterprise" or "community" based on your API Key type. If you have a paid subscription, use "enterprise". If you are using a free community account, select "community"
- API Key = Press the Set API Key button and enter your GreyNoise API Key
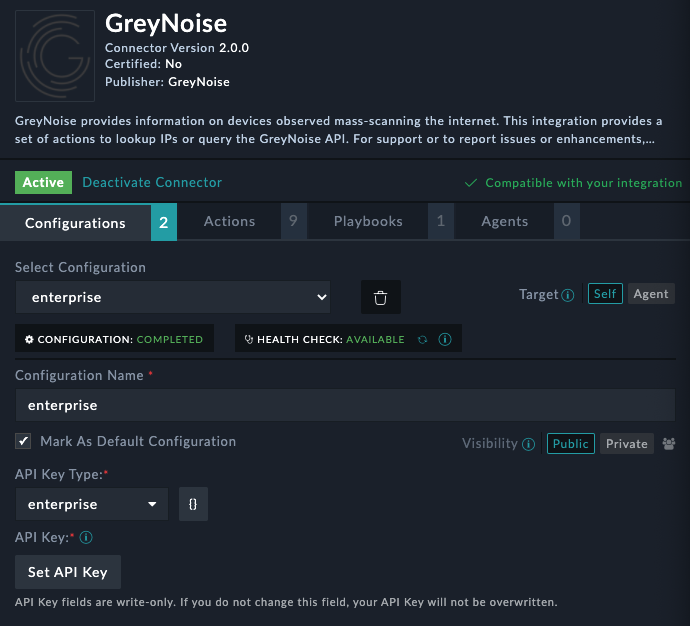
Successful Health CheckIf the configuration is valid and the API has validated the Health Check and Configuration boxes under Select Configuration will show "completed" and "available"
Performing an On-Demand Action
The GreyNoise connector provides a variety of On-Demand Actions that can be executed from the context of an Alert or an Incident and can be added to Playbooks as needed.
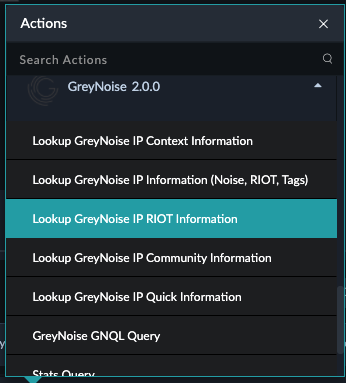
Community API (Free) UsersFor those users with Community (Free) API access only, the only action available will be the Lookup GreyNoise IP Community Information. All other actions will fail with an access denied error.
Playbooks
The Sample - GreyNoise - 2.0.0 playbook collection includes a sample playbook GreyNoise IP Full Lookup which can be used directly or modified to fit use case needs. This playbook takes in a defined IP address field based on the context it is used and performs a Full GreyNoise IP lookup, which queries Noise, RIOT, and Metadata endpoints to include all data GreyNoise has on an IP.
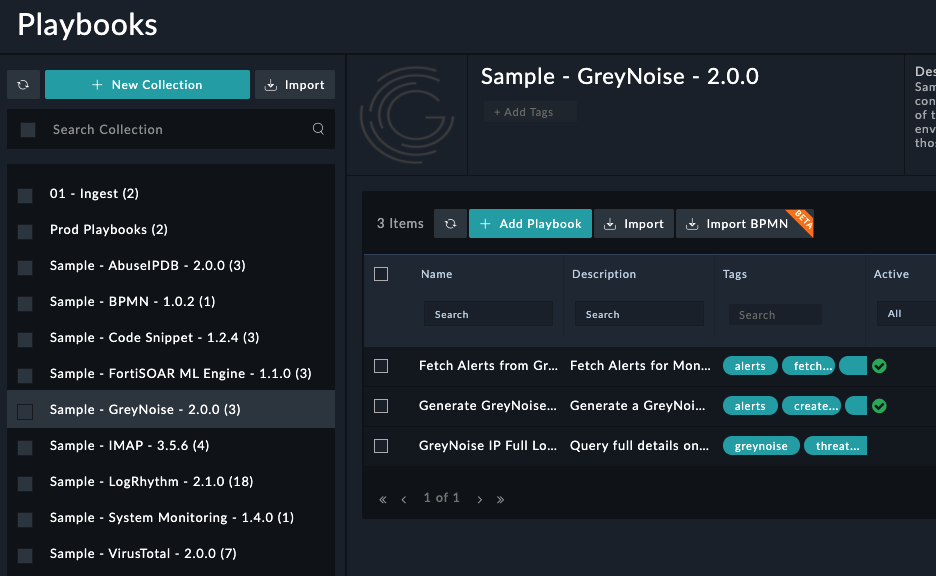
Accessing the GreyNoise sample enrichment workflow
To use this playbook, copy the template, then update the "IP Address" field in the GreyNoise Full IP Lookup action to pull the IP to be queried from the appropriate context.
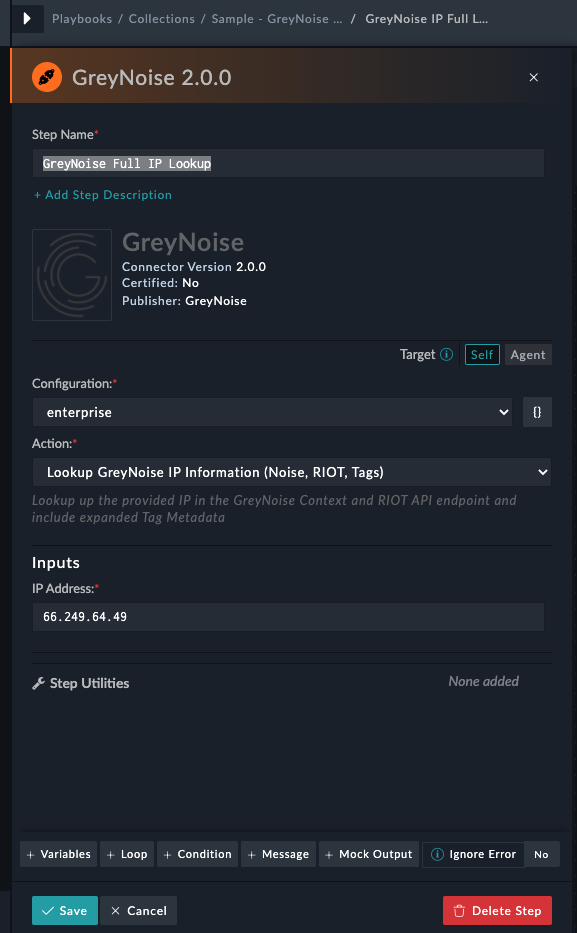
Updating the IP Address field from the sample value.
Setting up Alerting for Monitored CIDR Block
Alerting for a monitoring CIDR block can be set up by using two of the included Playbooks and setting them to execute on a Schedule in FortiSOAR. Start by copying the Fetch Alerts from GreyNoise and Generate GreyNoise Record playbooks from the Sample - GreyNoise - 2.0.0 playbook collection.
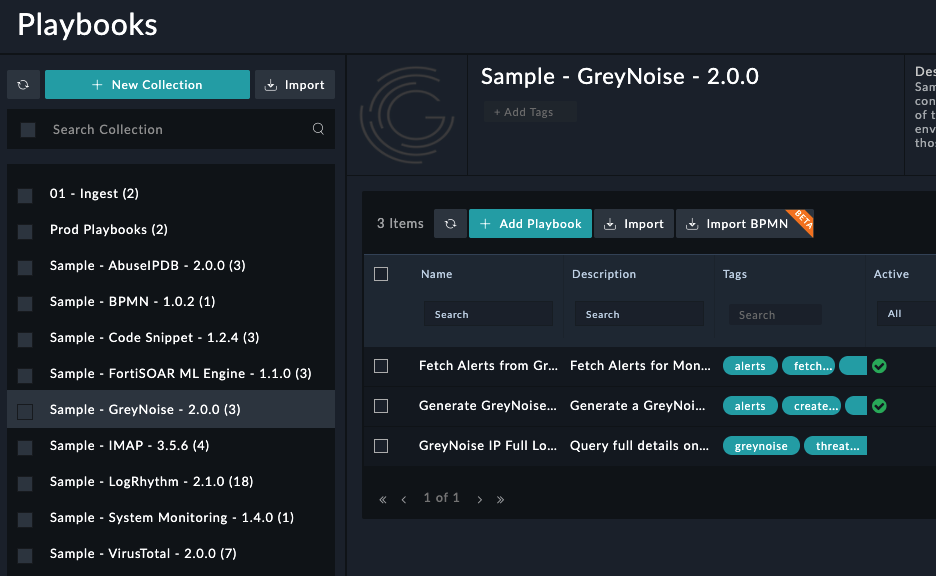
Accessing the GreyNoise Alerting playbook templates
Within the copied version of the Fetch Alerts from GreyNoise playbook, modify the Run Query for Monitored CIDR Block action and update the Query Input to include the Alert query to run. Generally, this will follow the format 171.7.221.0/16 spoofable:false last_seen:1d where the CIDR block is updated to the desired to be monitored. Additionally, the CIDR block can be replaced with exact IP addresses using the format (1.2.3.4 OR 5.6.7.8 OR 9.10.11.12) spoofable:false last_seen:1d).
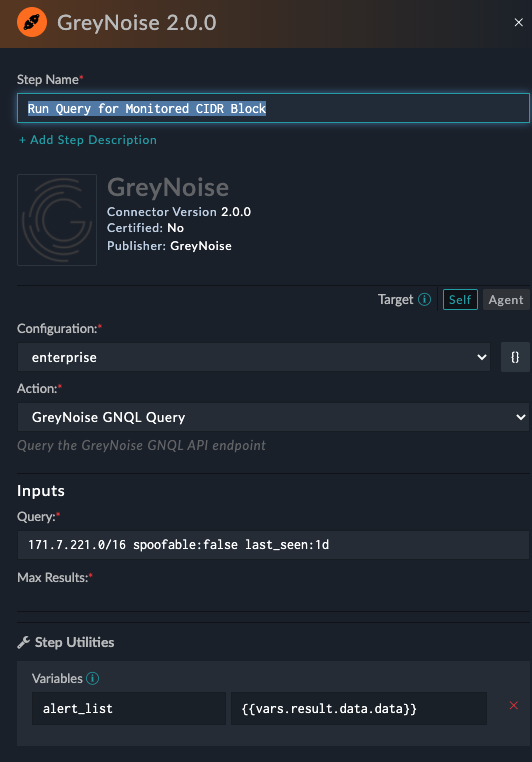
Updating the Monitored IP Query to run daily
Now Modify the Generate GreyNoise Record playbook to update the record details in the Create GreyNoise Alert action to match your desired Alert details.
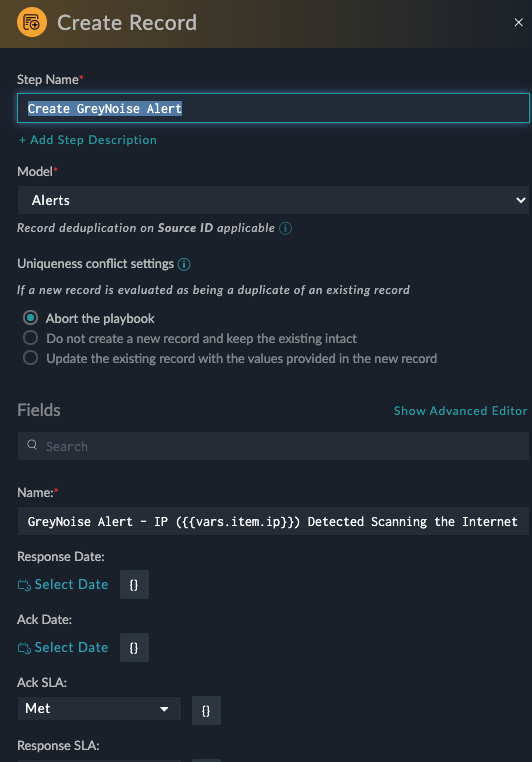
Modifying the GreyNoise Alert record template
With both playbooks modified, navigate to the Automations -> Schedules view and click Create New Schedule. Provide a name for the schedule, and select your copied Fetch Alerts from GreyNoise playbook, then set the Frequency to once per day at a time of your choosing.
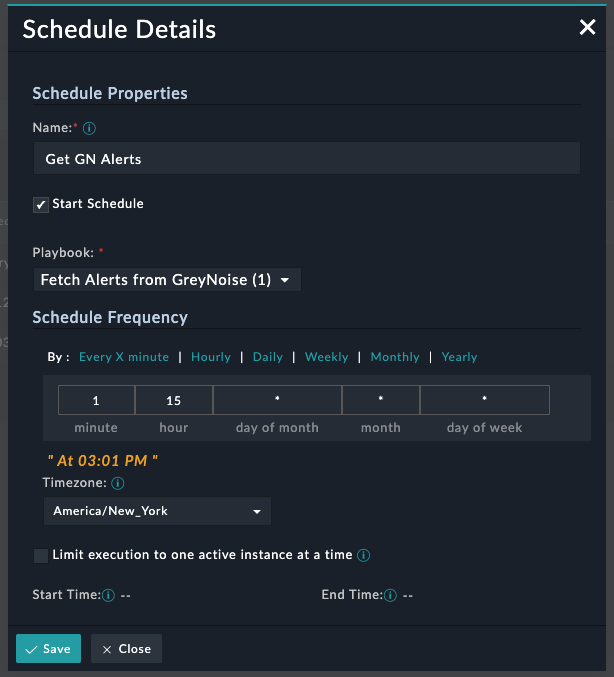
GreyNoise schedule for Monitored IP Alerts
This set of actions will then generate an Alert for any IP discovered scanning the internet in the monitored configuration.
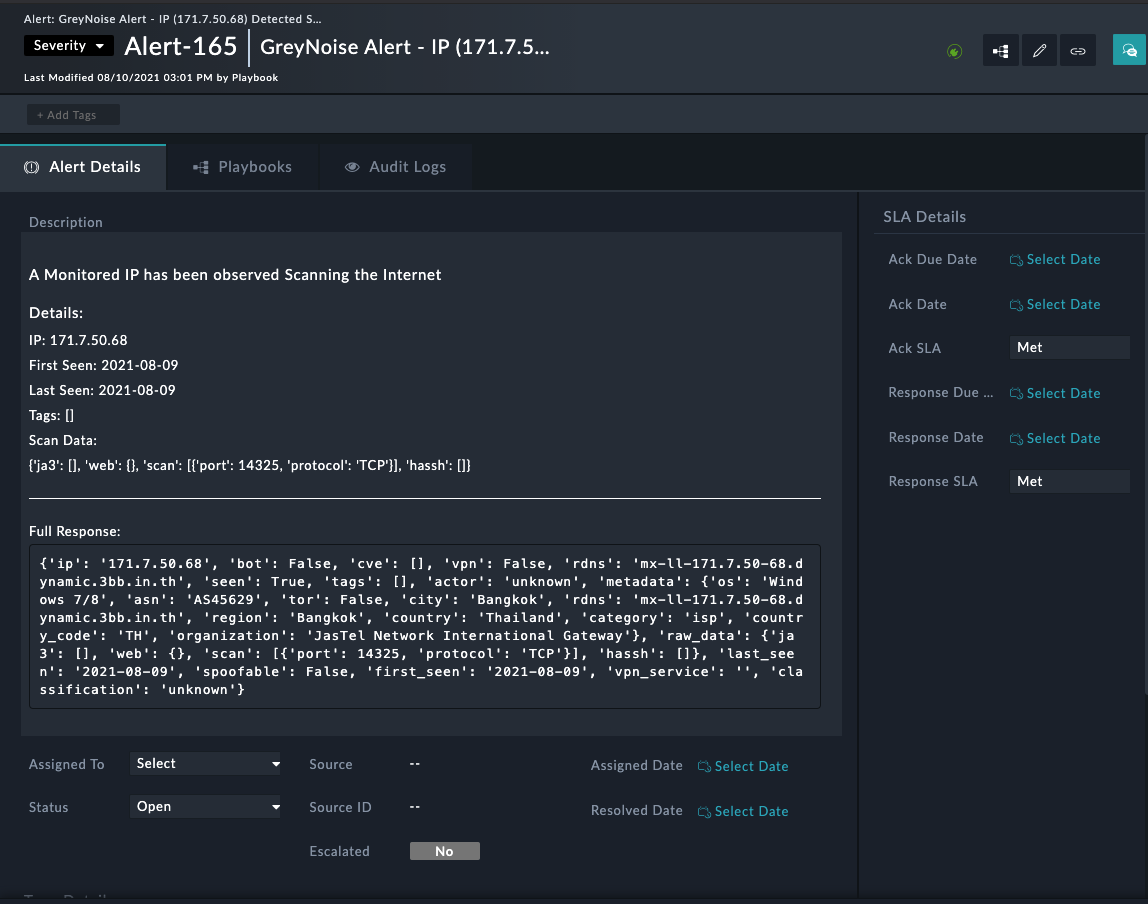
GreyNoise Alert for Monitored IP
Updated about 1 year ago
