Firewall Blocking with GreyNoise Trends
Dynamic IP Blocking with GreyNoise Trends
The GreyNoise Trends feature includes the ability to generate a dynamic list of IPs that can be used in the Dynamic Block List feature in many of today's firewall products.
The blocklist URL is tied to a specific GreyNoise tag, providing a dynamically updated list of IPs that have been observed scanning for the specific tag activity in the last 24 hours.
To obtain the blocklist URL for a tag, navigate to the GreyNoise Trends page for the tag you want to dynamically block.
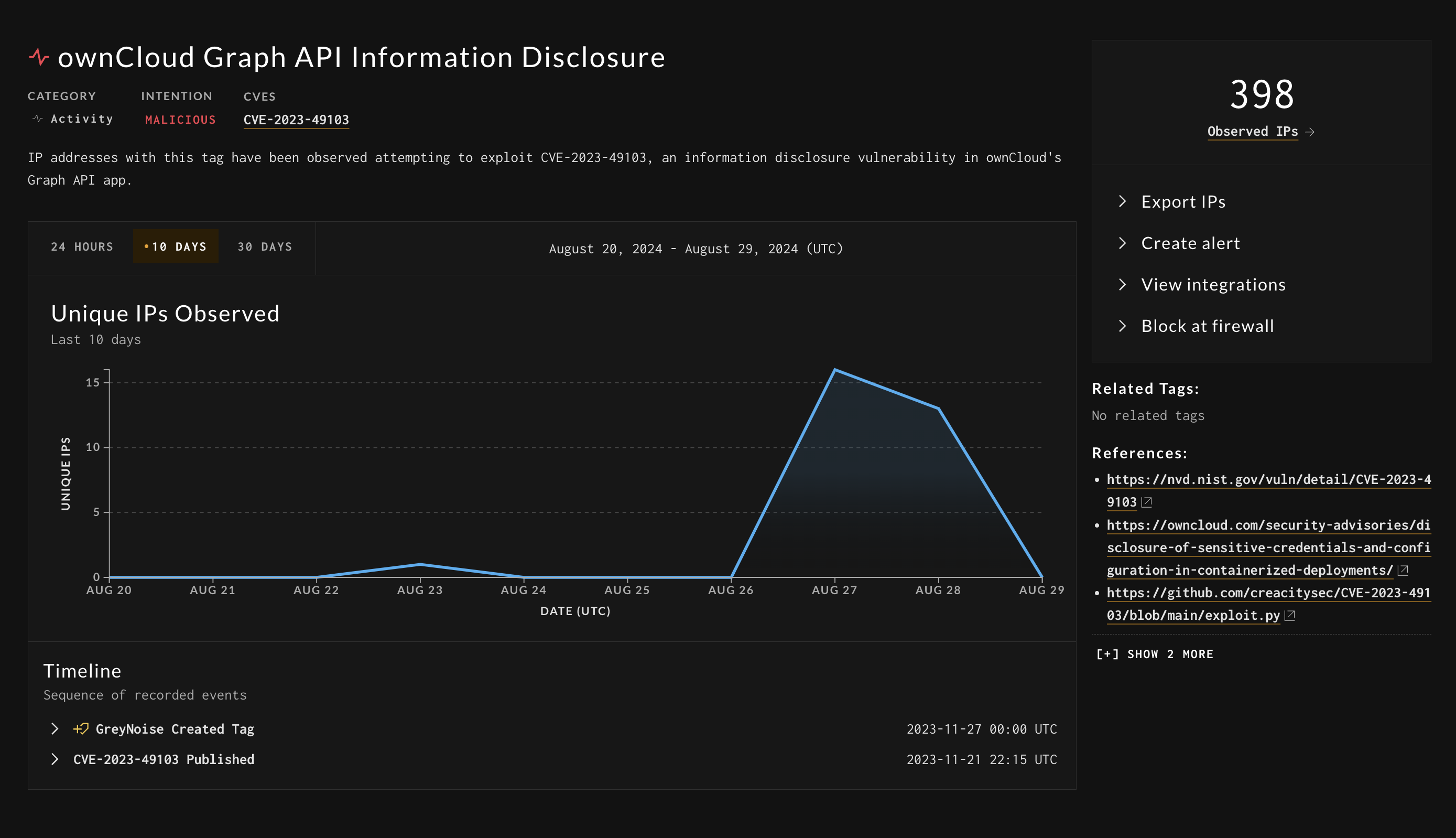
GreyNoise Trends Page
On the right-hand column, expand the Block at firewall menu:
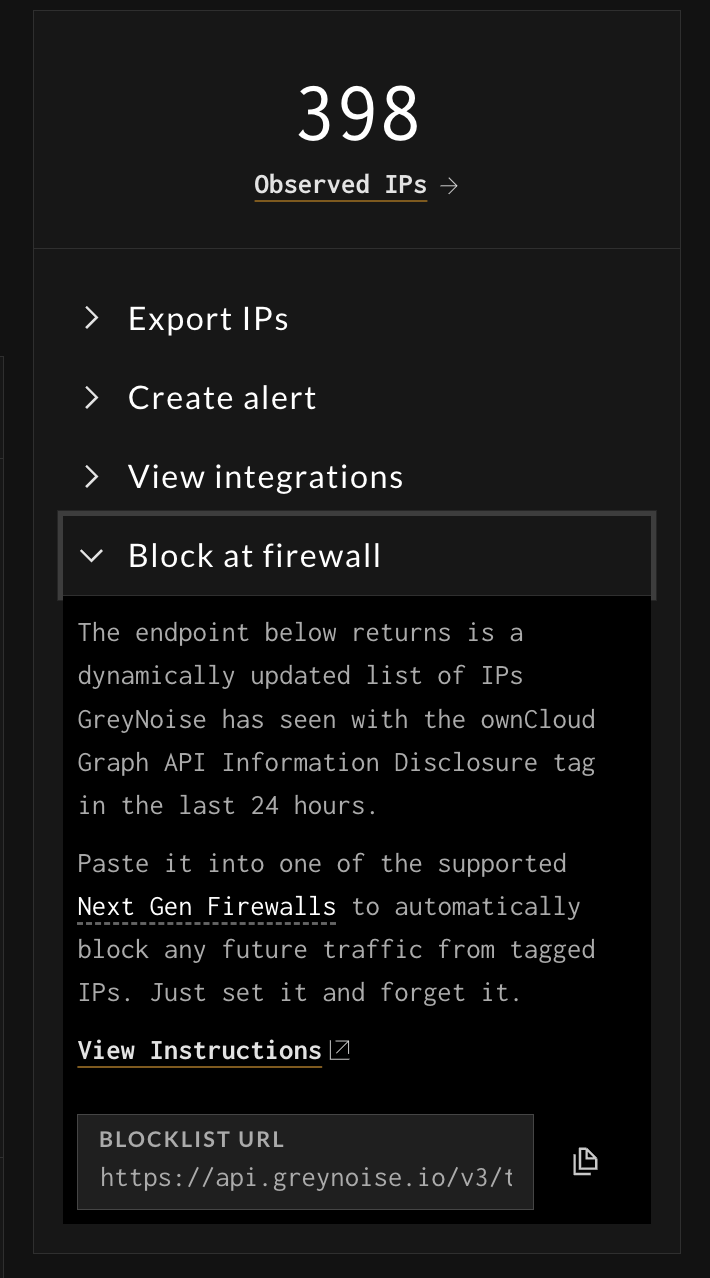
Actions Section of GreyNoise Trends
At the bottom of the screen, select the Copy button to capture the URL to use for the Dynamic Block List.
This URL can now be used to populate Dynamic Block Lists on most major firewalls. Here are some links to additional vendor-specific documentation that shows how to apply this URL to a blocklist.
Palo Alto Networks
Cisco ASA
Fortinet Fortigate
Sophos Firewall
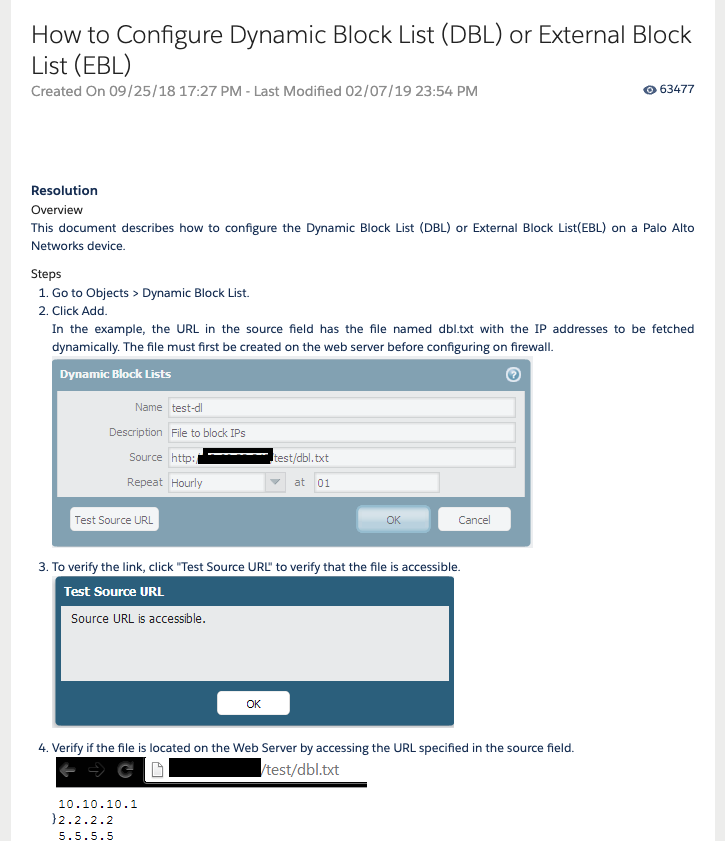
Vendor Configuration Sample - Palo Alto
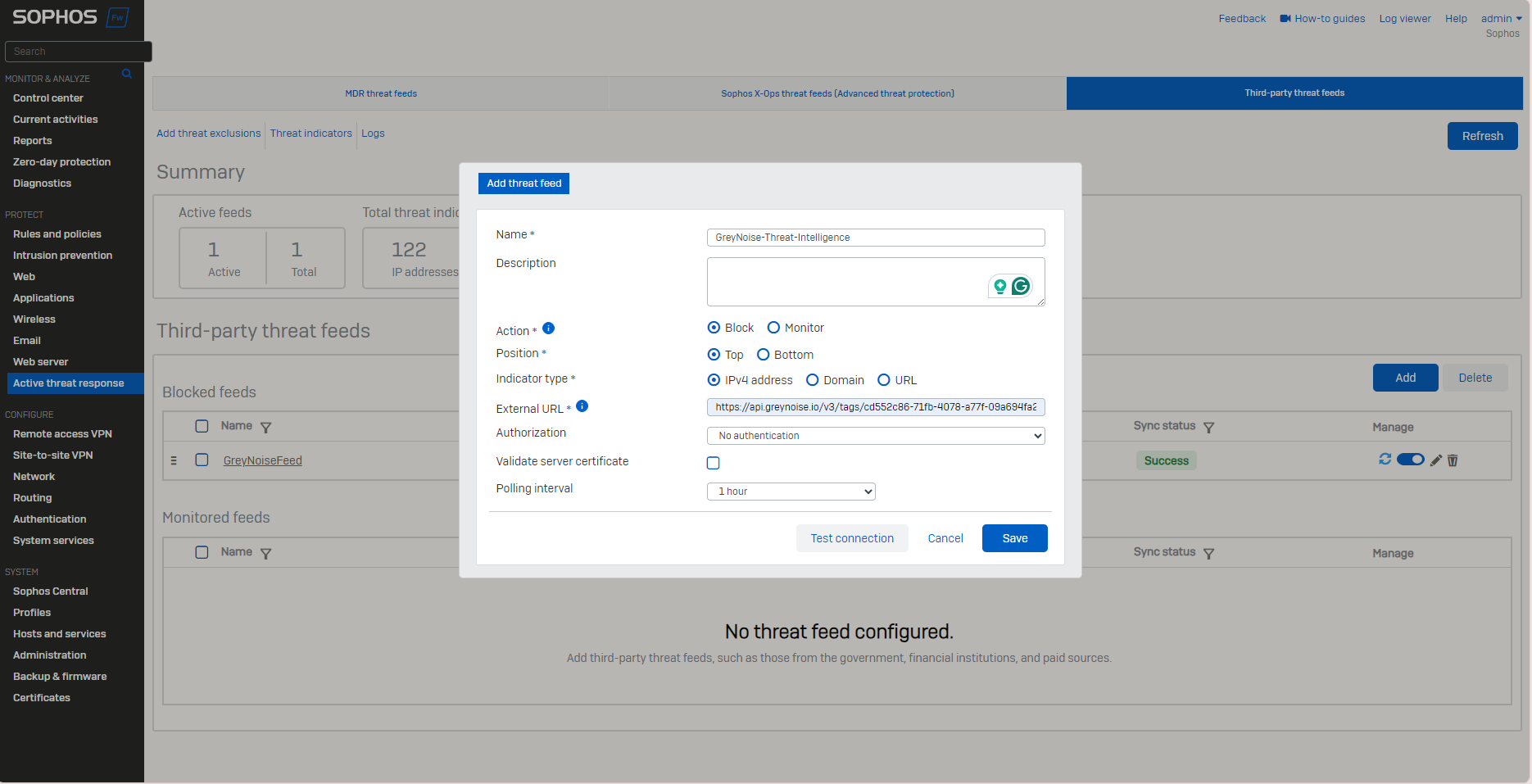
Vendor Configuration Sample - Sophos
Updated 10 months ago
