Vulnerability Prioritization Overview
What is Vulnerability Prioritization?
GreyNoise Vulnerability Prioritization is intended to help customers get current, reliable, and actionable information about active exploitation of vulnerabilities on assets exposed to the Internet. Customers can use this information to prioritize mitigation and remediation of vulnerabilities that are truly urgent today.
Why Did We Build a Vulnerability Prioritization Product?
GreyNoise is uniquely positioned to offer timely and complete information about the active exploitation of a vulnerability in the wild. Most vulnerability management vendors get exploitation information from 3rd party sources that may be incomplete and can rapidly become out-of-date. GreyNoise shows exactly what attacks are happening on the Internet right now.
What data is included?
The full data dictionary for this endpoint can be found here
What should I do with this data?
The data provided for each CVE provides the unique insight that GreyNoise has to offer. This data can be used to
- Make prioritization decisions around patching known vulnerabilities
- Take a proactive stance around blocking IPs associated with these vulnerabilities at your perimeter
Blocking at the Perimeter
The CVE details page includes links to any GreyNoise Blockists associated with these CVEs.
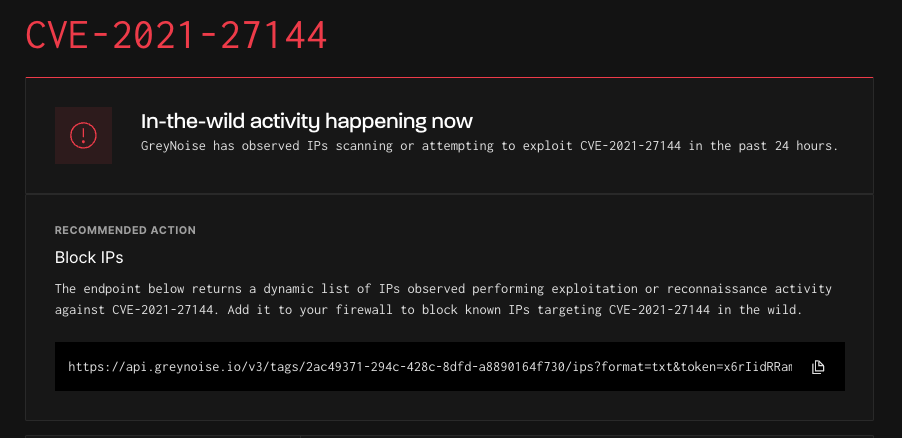
The Blocklist URLs provided can be configured into Firewall External Dynamic Lists (EDLs) to proactively block all IPs associated with this CVE.
For more details on using GreyNoise Blocklists in Firewall Blocking, please see Firewall Blocking with GreyNoise Trends
Access Methods
Visualizer Access
To access the Vulnerability Prioritization feature, you can perform the following actions in the Visualizer:
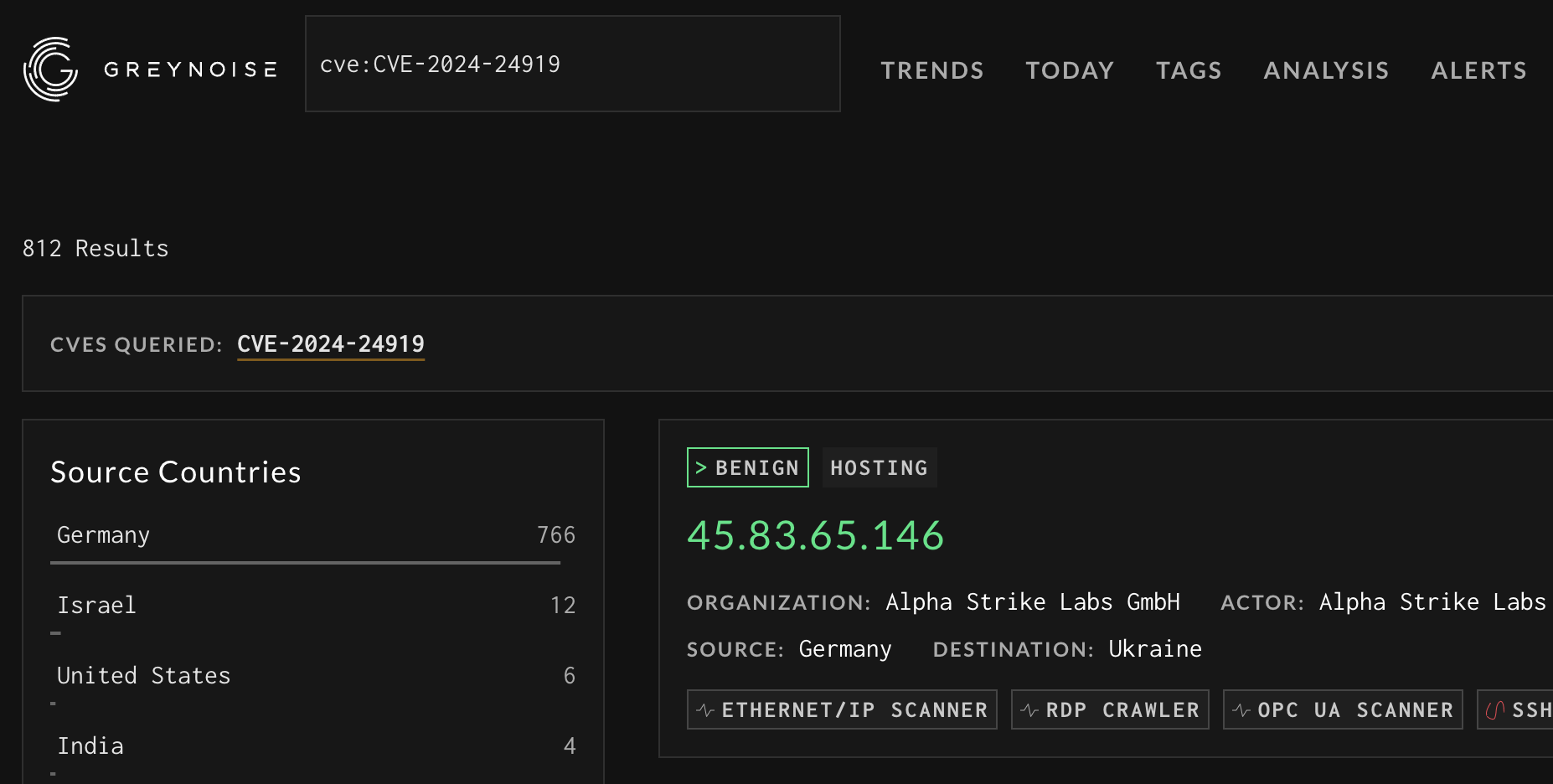
Search for a CVE via the Search bar using thecve:CVE-2024-24919 format
cve:CVE-2024-24919 formatClick on the CVE link at the top of the search page:
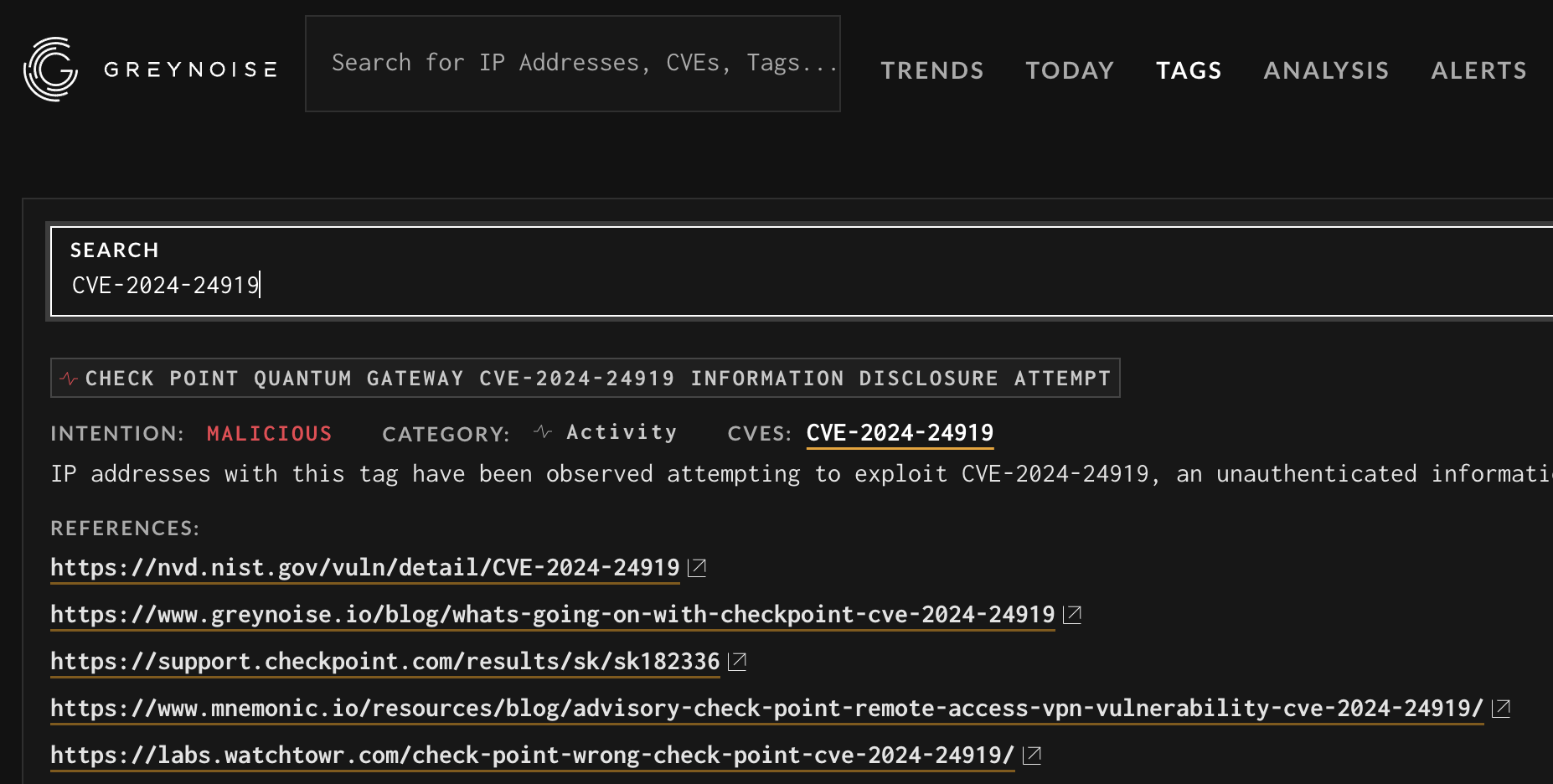
Search for a CVE in the tag library and click the CVE link:
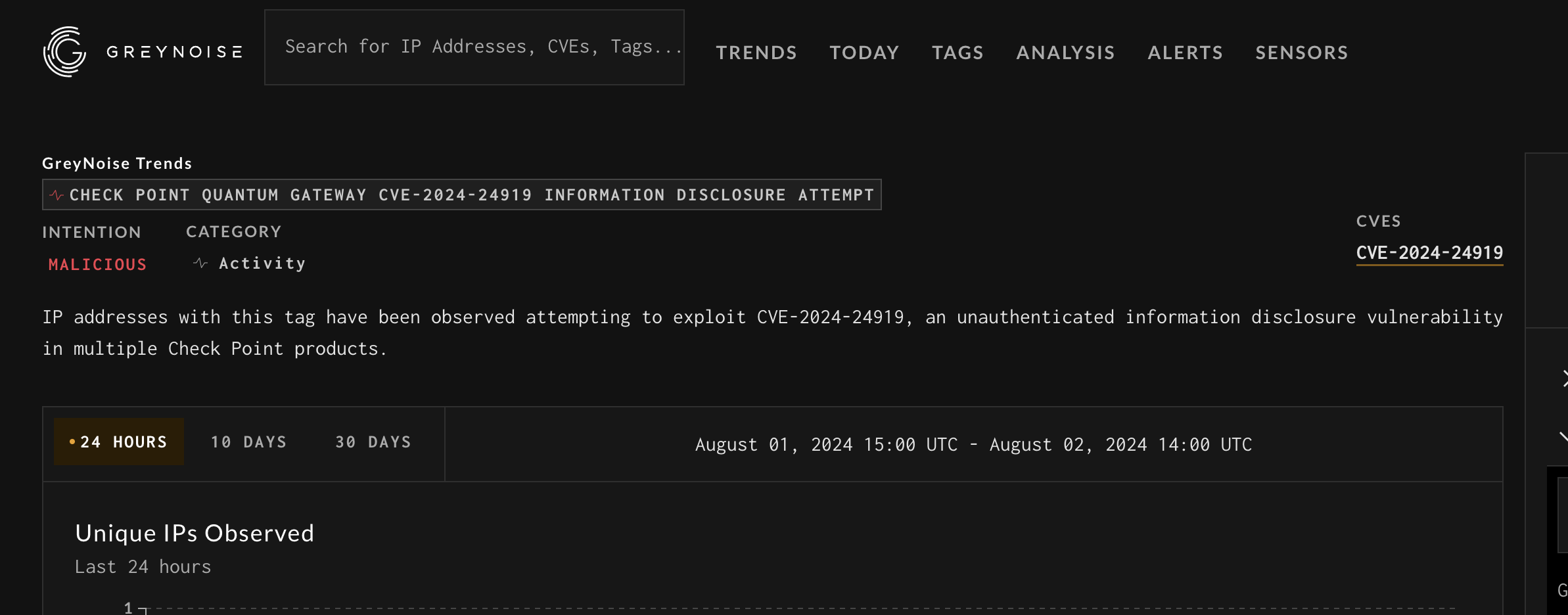
Navigate to a Tag Details page and click on the CVE link:
Vulnerability Prioritization Details Page
Unauthenticated User Experience
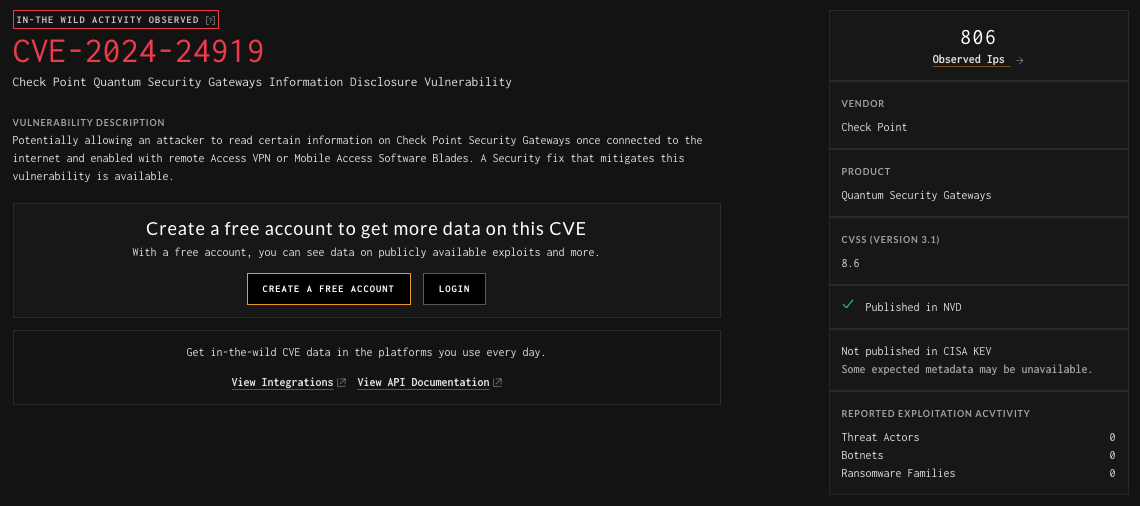
Standard User Experience
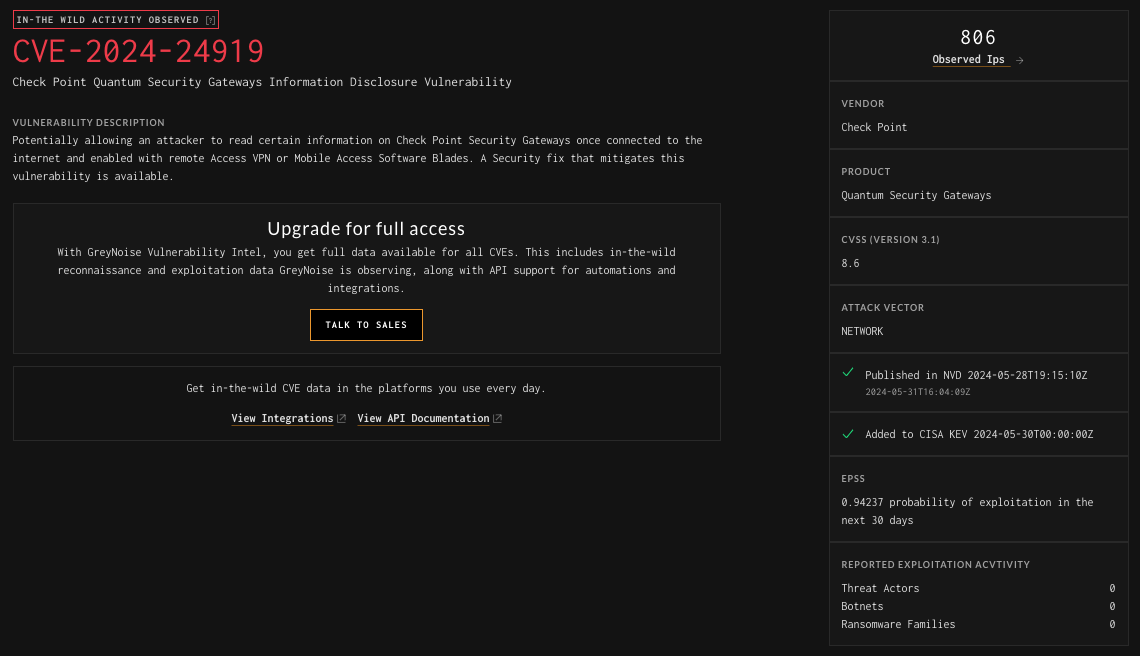
Paid Subscription (with Vulnerability Prioritization SKU) User Experience
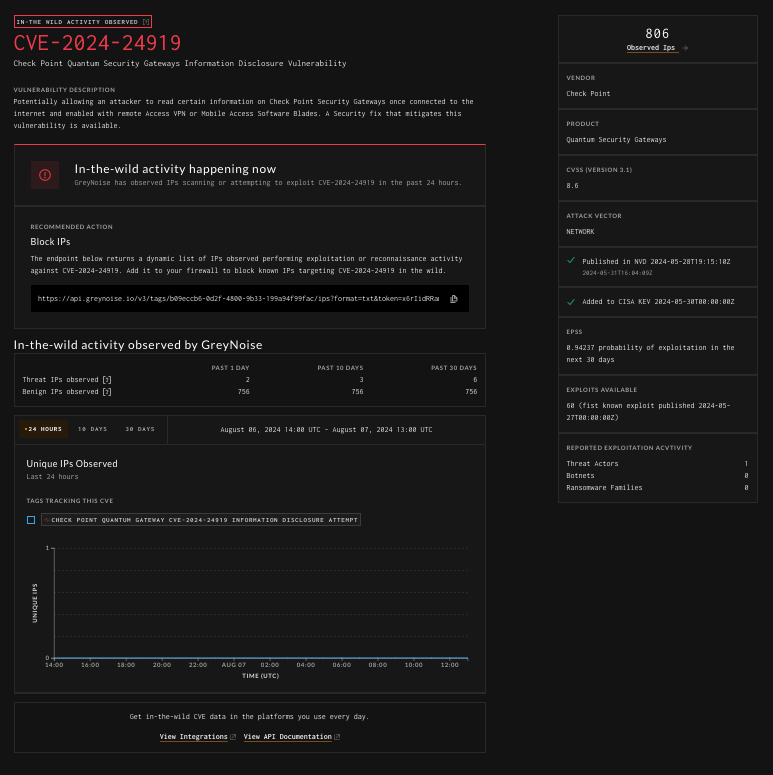
Vulnerability Prioritization API
Details on the API for the Vulnerability Prioritization Feature can be found here
Unauthenticated User Experience
{
"id": "CVE-2024-24919",
"details": {
"vulnerability_name": "Check Point Quantum Security Gateways Information Disclosure Vulnerability",
"vulnerability_description": "Potentially allowing an attacker to read certain information on Check Point Security Gateways once connected to the internet and enabled with remote Access VPN or Mobile Access Software Blades. A Security fix that mitigates this vulnerability is available.",
"cve_cvss_score": 8.6,
"product": "Quantum Security Gateways",
"vendor": "Check Point",
"published_to_nist_nvd": true
}
}Standard API Key User Experience
{
"id": "CVE-2024-24919",
"details": {
"vulnerability_name": "Check Point Quantum Security Gateways Information Disclosure Vulnerability",
"vulnerability_description": "Potentially allowing an attacker to read certain information on Check Point Security Gateways once connected to the internet and enabled with remote Access VPN or Mobile Access Software Blades. A Security fix that mitigates this vulnerability is available.",
"cve_cvss_score": 8.6,
"product": "Quantum Security Gateways",
"vendor": "Check Point",
"published_to_nist_nvd": true
},
"timeline": {
"cve_published_date": "2024-05-28T19:15:10Z",
"cve_last_updated_date": "2024-05-31T16:04:09Z",
"first_known_published_date": "2024-05-27T00:00:00Z",
"cisa_kev_date_added": "2024-05-30T00:00:00Z"
},
"exploitation_details": {
"attack_vector": "NETWORK",
"exploit_found": true,
"exploitation_registered_in_kev": true,
"epss_score": 0.94237
}
}Paid Subscription (with Vulnerability Prioritization SKU) User Experience
{
"id": "CVE-2024-24919",
"details": {
"vulnerability_name": "Check Point Quantum Security Gateways Information Disclosure Vulnerability",
"vulnerability_description": "Potentially allowing an attacker to read certain information on Check Point Security Gateways once connected to the internet and enabled with remote Access VPN or Mobile Access Software Blades. A Security fix that mitigates this vulnerability is available.",
"cve_cvss_score": 8.6,
"product": "Quantum Security Gateways",
"vendor": "Check Point",
"published_to_nist_nvd": true
},
"timeline": {
"cve_published_date": "2024-05-28T19:15:10Z",
"cve_last_updated_date": "2024-05-31T16:04:09Z",
"first_known_published_date": "2024-05-27T00:00:00Z",
"cisa_kev_date_added": "2024-05-30T00:00:00Z"
},
"exploitation_details": {
"attack_vector": "NETWORK",
"exploit_found": true,
"exploitation_registered_in_kev": true,
"epss_score": 0.94237
},
"exploitation_stats": {
"number_of_available_exploits": 60,
"number_of_threat_actors_exploiting_vulnerability": 1,
"number_of_botnets_exploiting_vulnerability": 0
},
"exploitation_activity": {
"activity_seen": true,
"benign_ip_count_1d": 756,
"benign_ip_count_10d": 756,
"benign_ip_count_30d": 756,
"threat_ip_count_1d": 2,
"threat_ip_count_10d": 3,
"threat_ip_count_30d": 6
}
}Updated about 1 year ago
