TIP Integration Overview: Anomali ThreatStream
Malicious IP Feed
Install from App Store
From the ThreatStream App Store, search for the GreyNoise Premium Feed and Click Get Access.

GreyNoise Premium Feed card in App Store
Click "I have Credentials" on the configuration screen, enter your GreyNoise API key, and then click activate.
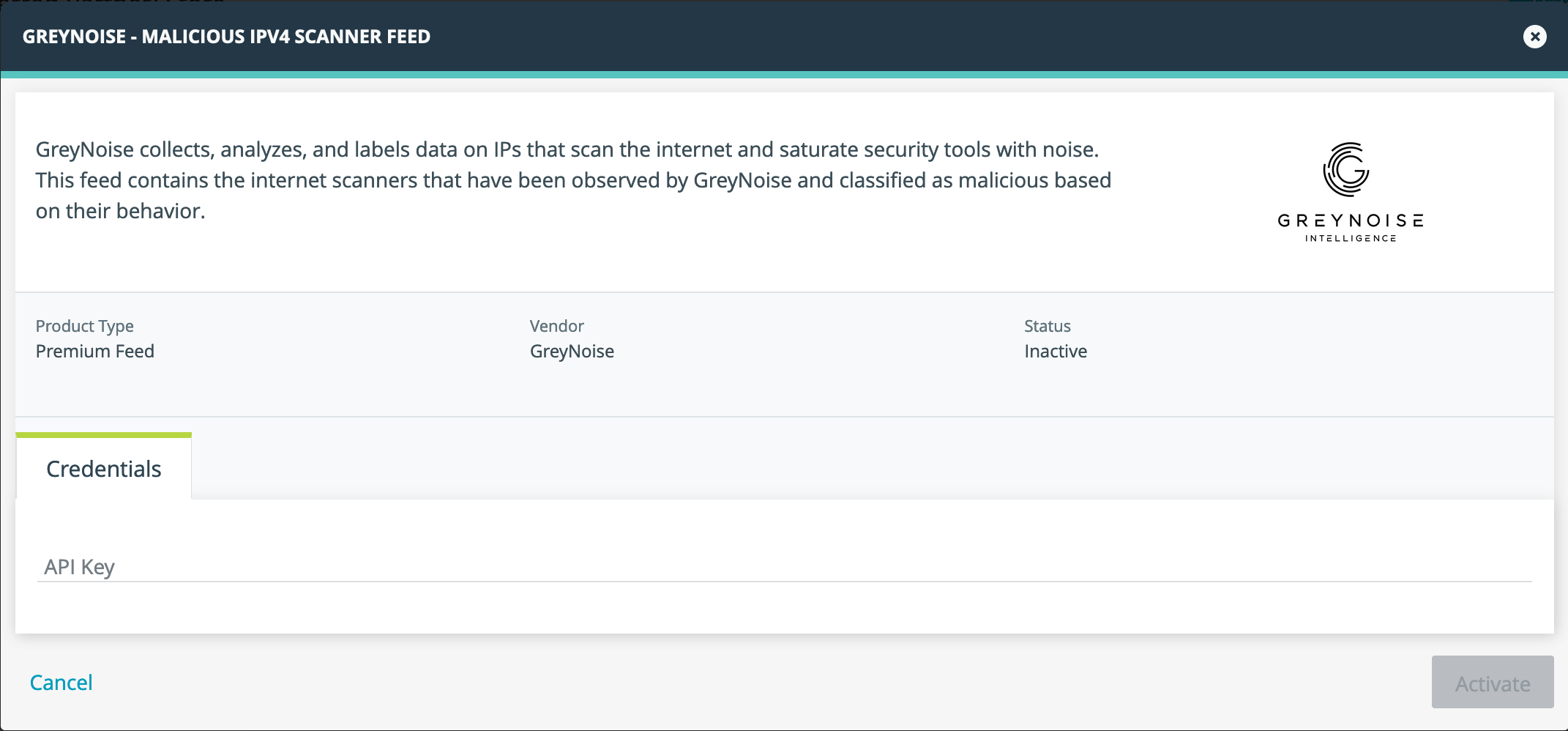
GreyNoise Feed credential configuration dialog
This Feed updates once per day.
The Feed requires an active GreyNoise subscription with Feed access. A 14-Day Free trial is available for existing customers and for new customers that start a GreyNoise Trial.
Sample Observable
The following shows a sample of an observable that was created by the Feed. It includes the classification information, source country, and CVE information provided by GreyNoise as tags.
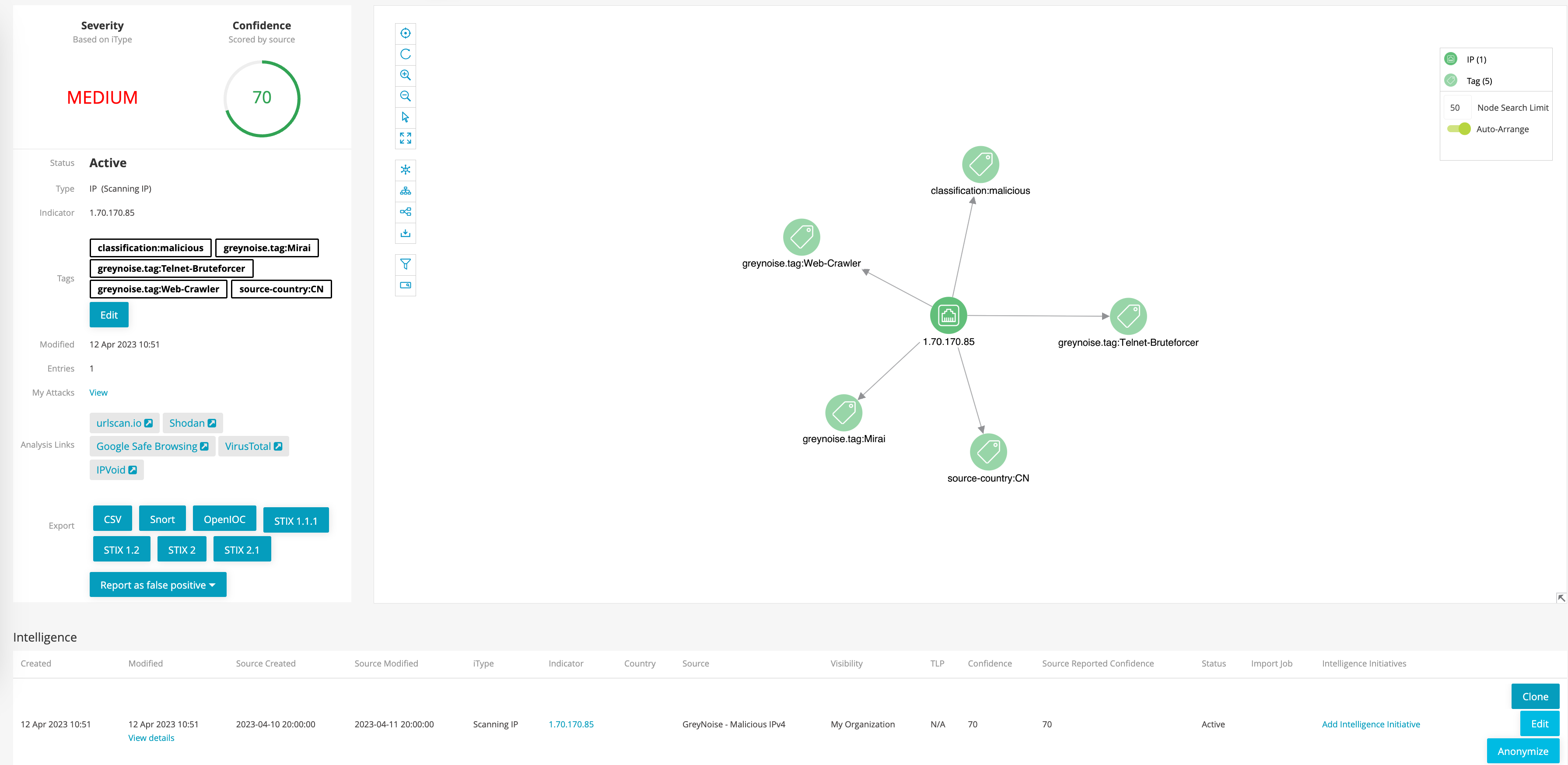
Sample of observable provided by GreyNoise Feed
Enrichment
Install From AppStore
Current Version: 3.0.0
From the ThreatStream Interface, go to the App Store. Search for GreyNoise and select the Get Access option.

GreyNoise Premium Enrichment card in App Store
Configure Credentials
Click "I have credentials" to configure the enrichment.

Enter a GreyNoise API Key, then press the Activate button.
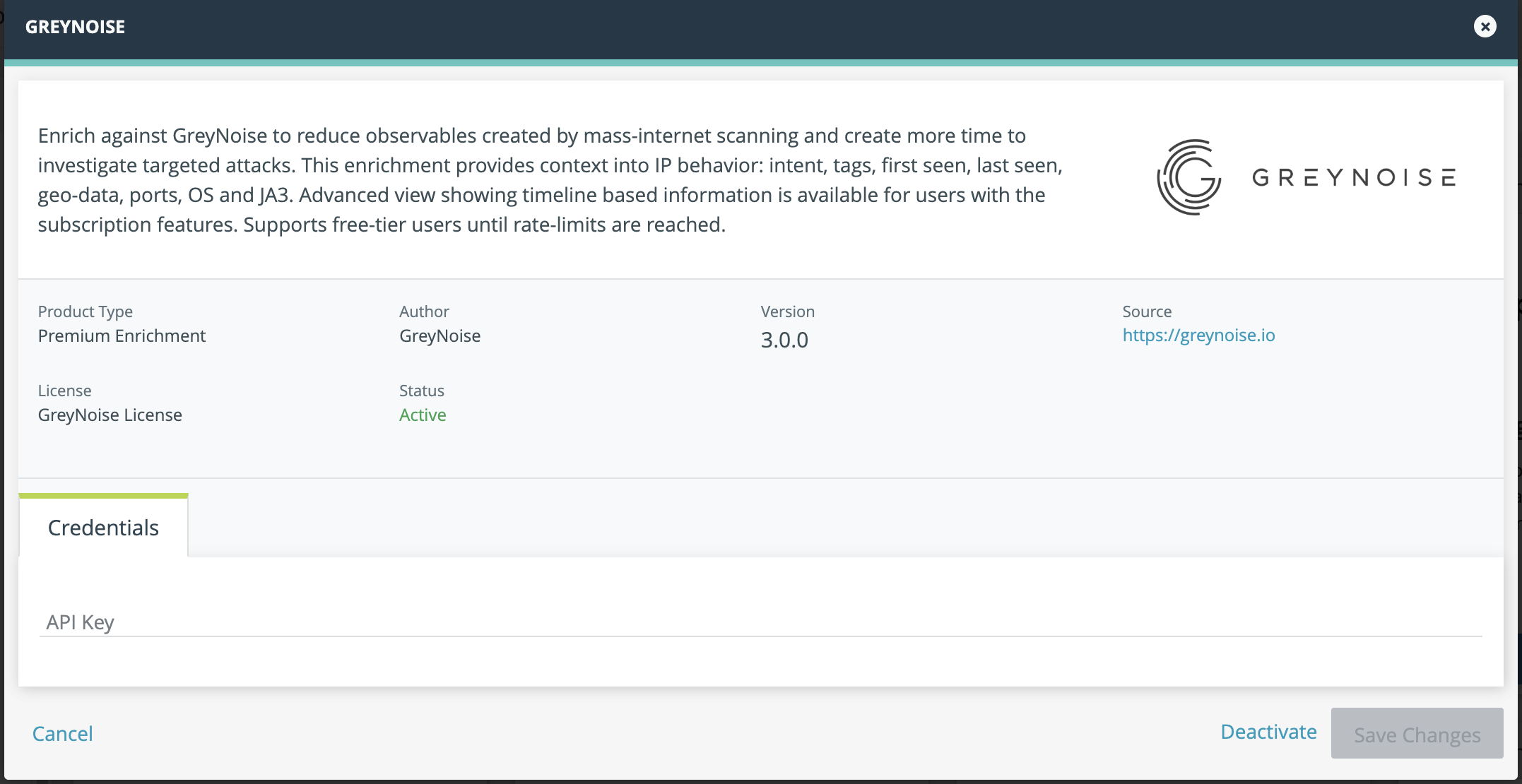
If the activation is successful, ThreatStream will display a Green success notification. If there are any issues, please contact [email protected]
Free Tier API KeysFor those users with a Free / Commuity Tier API key, enter the key as above, and the enrichment for IPs will work within the restrictions and rate-limits on your account.
Enriching an IP Observerable
Once the GreyNoise enrichment is enabled, ThreatStream will automatically query the GreyNoise IP API and provide results for all public IPv4 observables. If the IP address is part of the GreyNoise dataset, the details will be displayed on the IP Details tab:
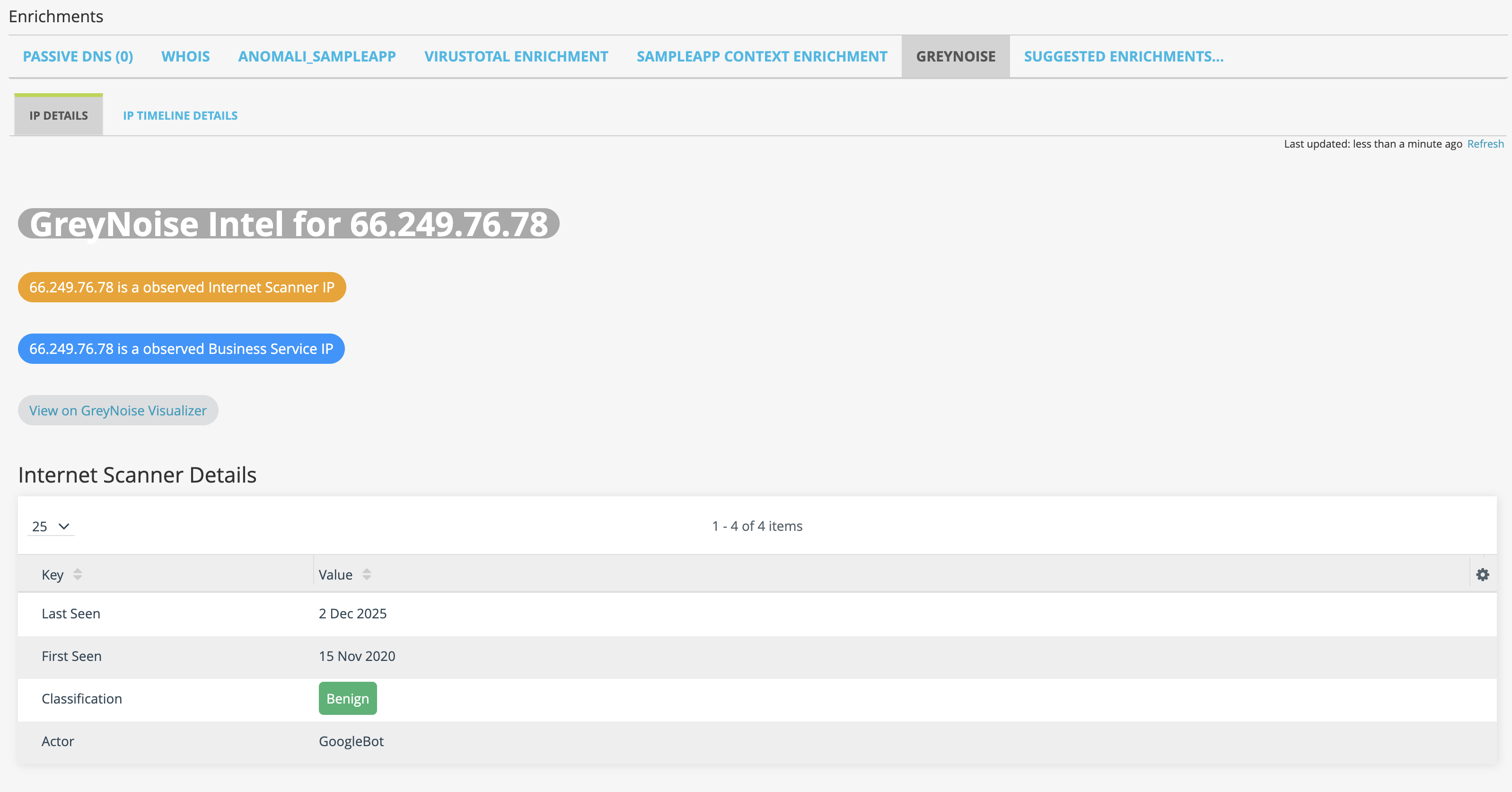
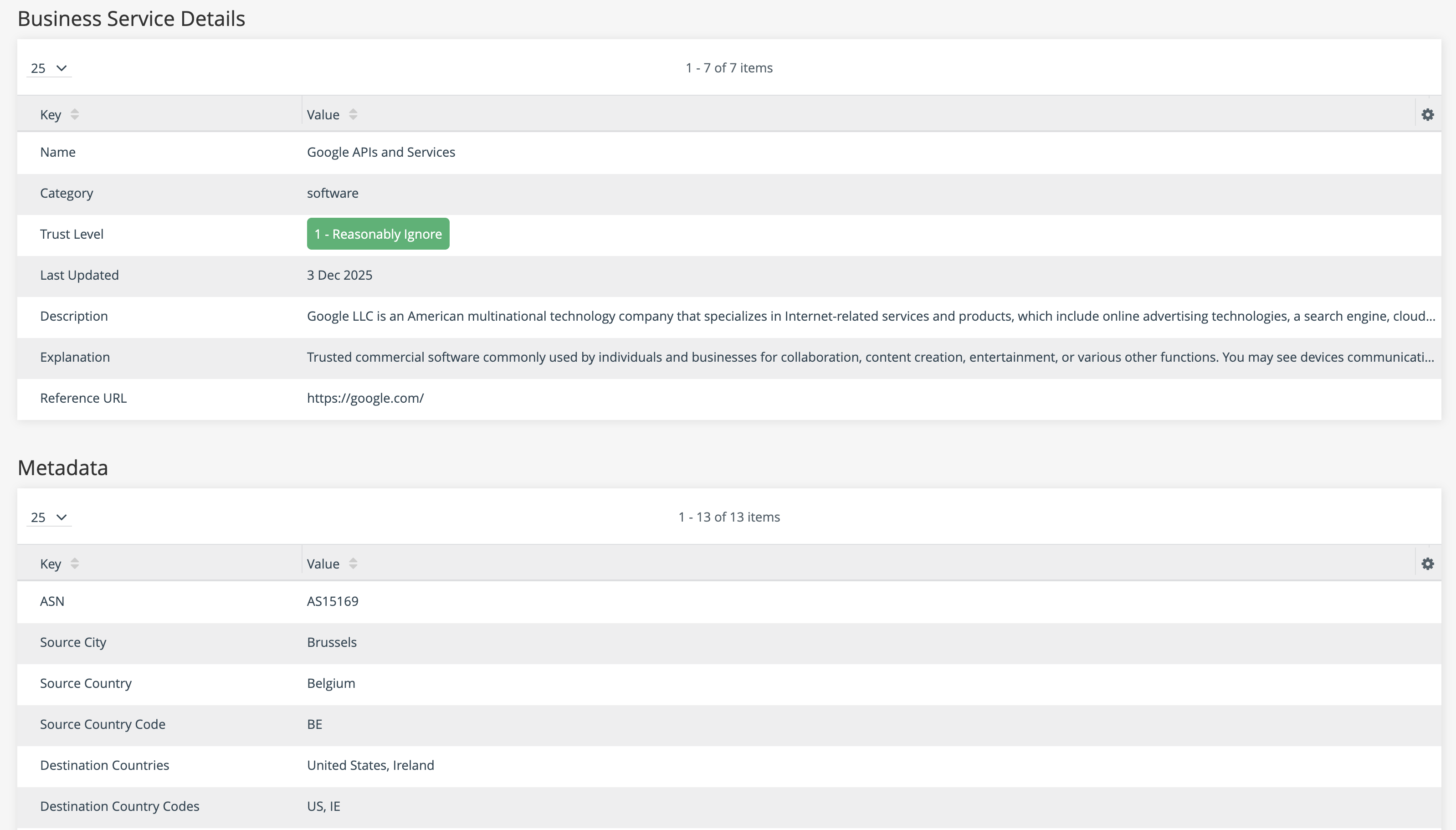
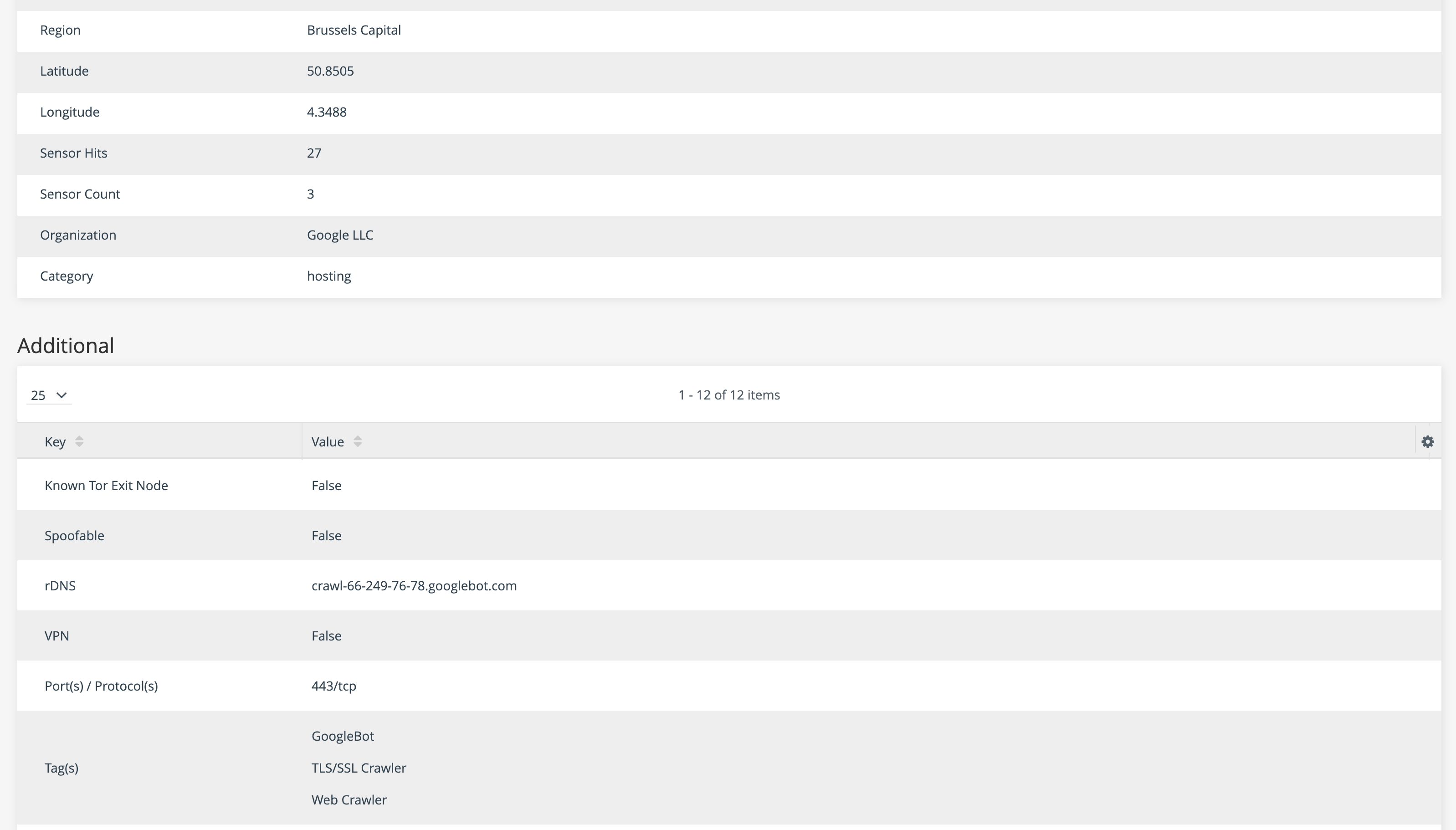

IPs that are Not Noise
If an IP is not found in the GreyNoise data set, ThreatStream will provide an indicator that this is the case:
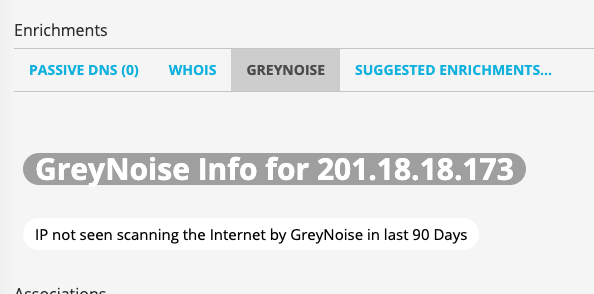
IP Timeline Information
Click on the IP Timeline Details tab to view a daily view of scanning activity.
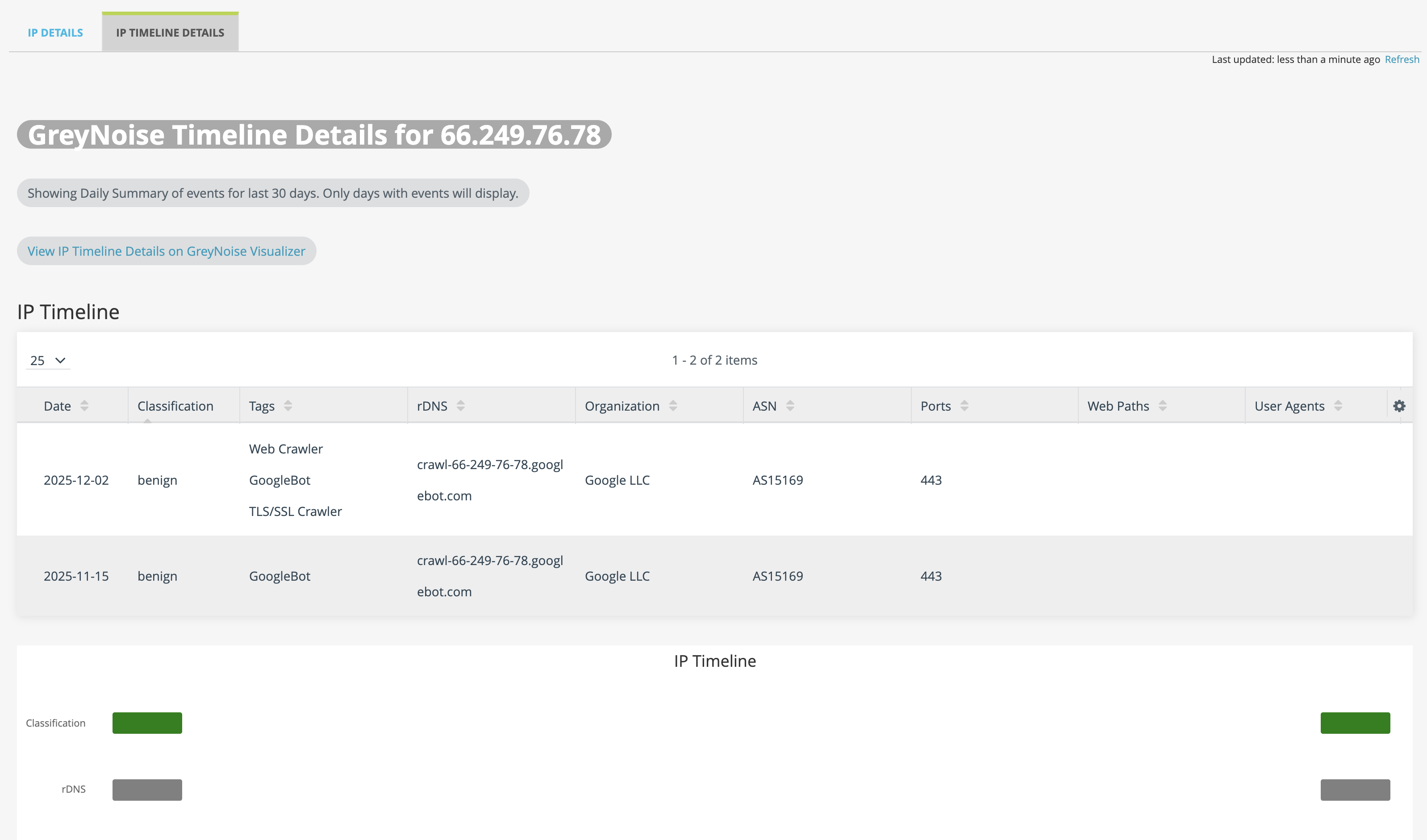
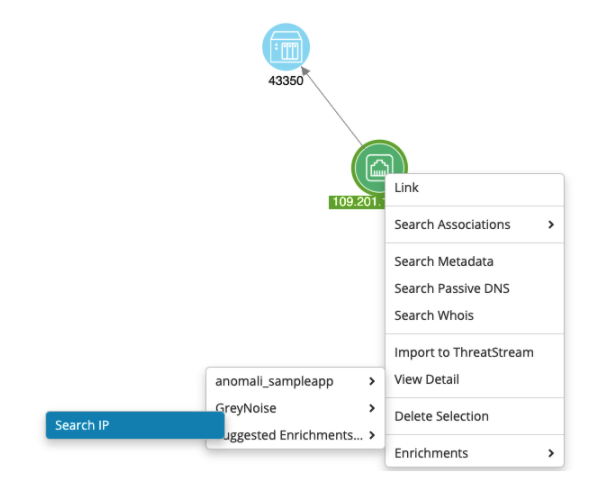
Performing a Pivot-Based (right-click) Lookup
To query an IP in GreyNoise from the canvas, right-click on an IPv4 address, then select the "Search IP" action from the GreyNoise enrichments menu:
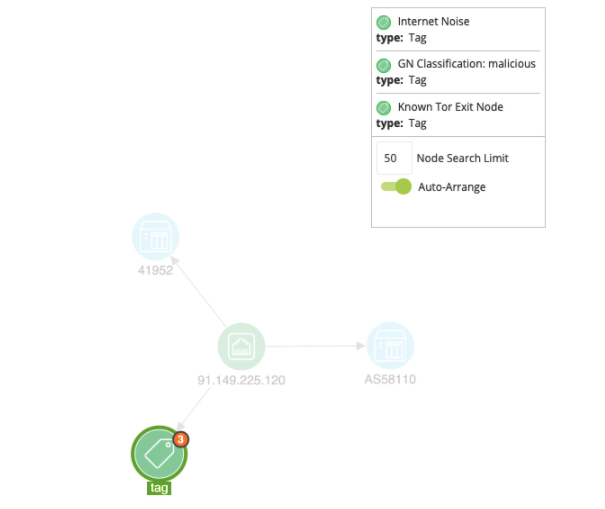
The enrichment will add additional tags and other information to the canvas, based on the response from GreyNoise and if the Enterprise or Community API is being used:
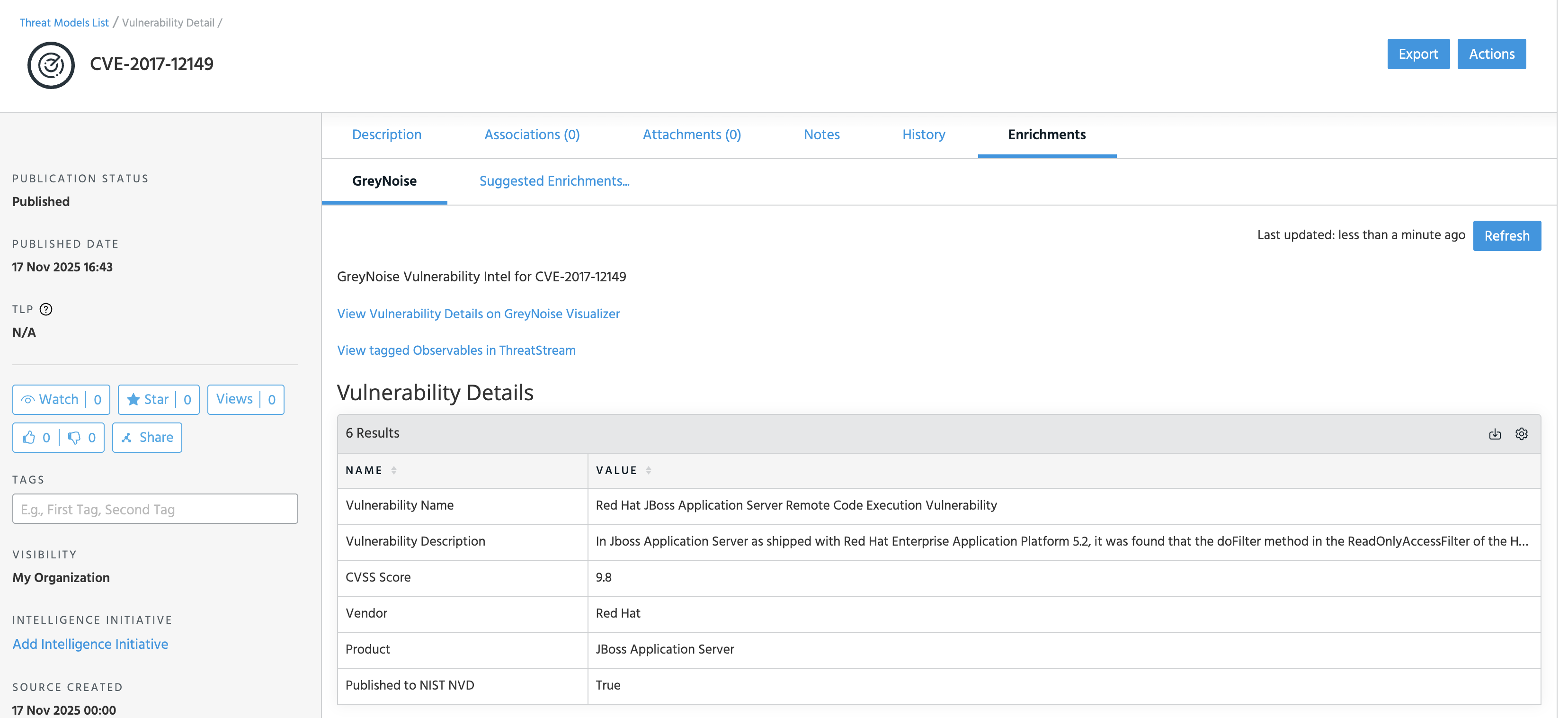
Enriching a Vulnerability
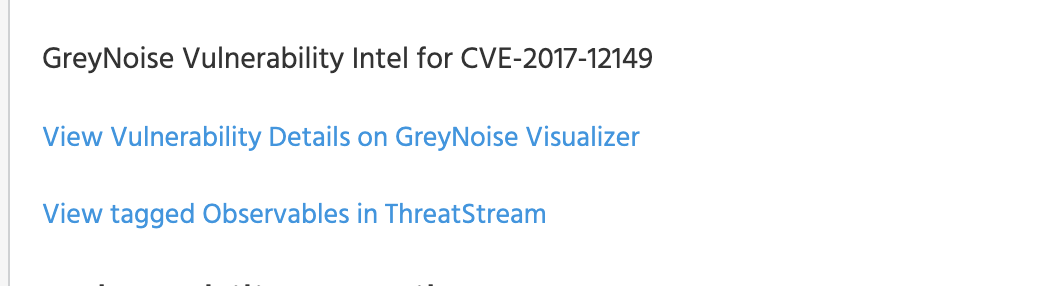
Once the GreyNoise enrichment is enabled, ThreatStream will automatically query the GreyNoise CVE API and provide results for all CVEs within the dataset:
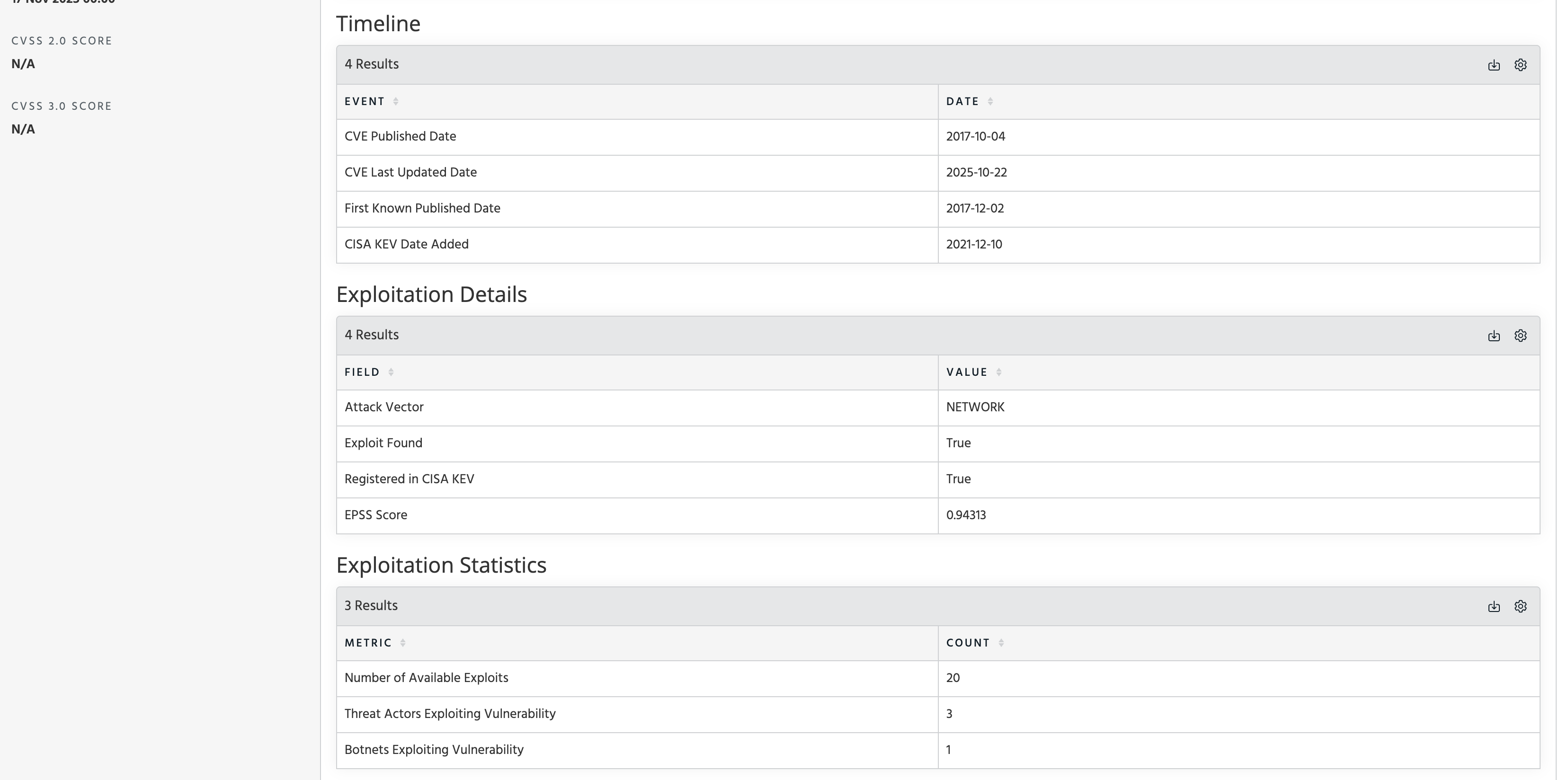
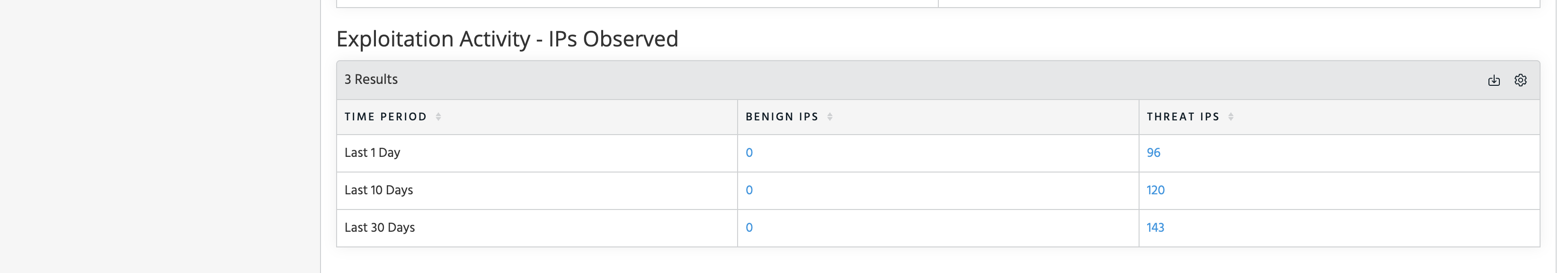
Pivot to Observables with Vulnerability Tag
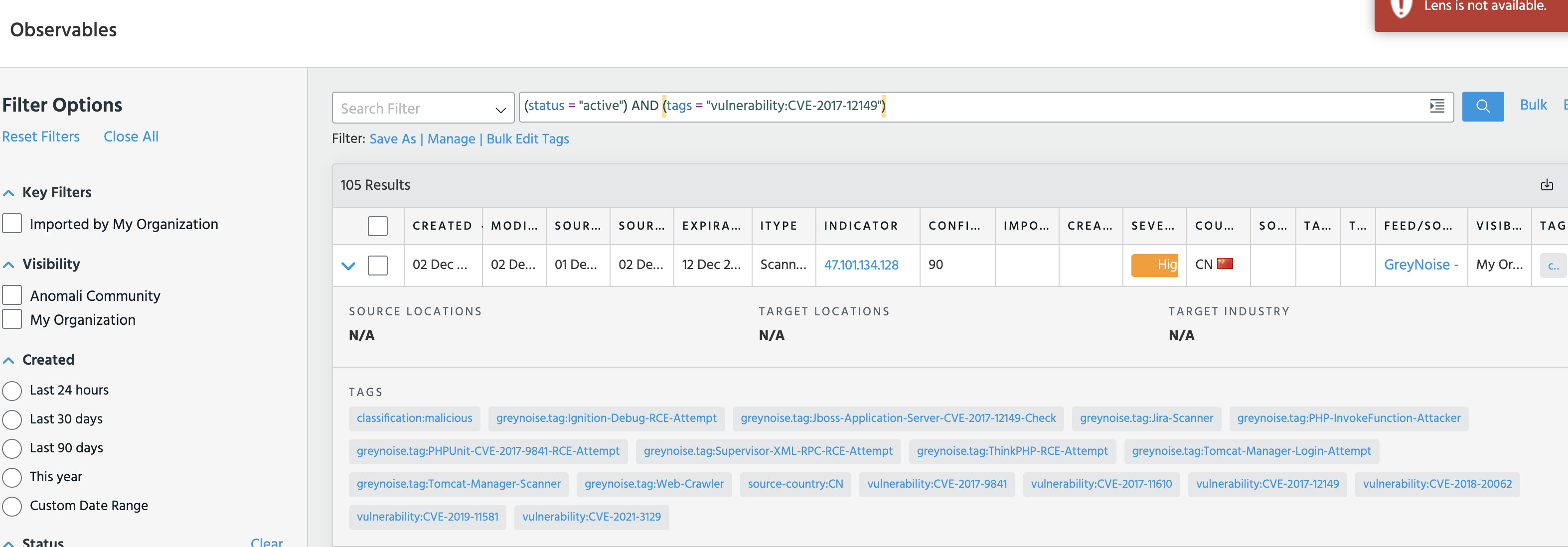
For those users with one or more GreyNoise Indicator feeds enabled, the Vulnerability enrichment includes a link to Pivot to the Observables tab and search for all active indicators ingested within a GreyNoise feed that are tagged with the indicated Vulnerability:
Updated 3 months ago
