SIEM Integration Overview: Azure Sentinel TI Feed
Install From Sentinel Content Hub
Navigate to the instance of Sentinel where the Pack will be installed, then browse to the Content Hub and Search for GreyNoise.
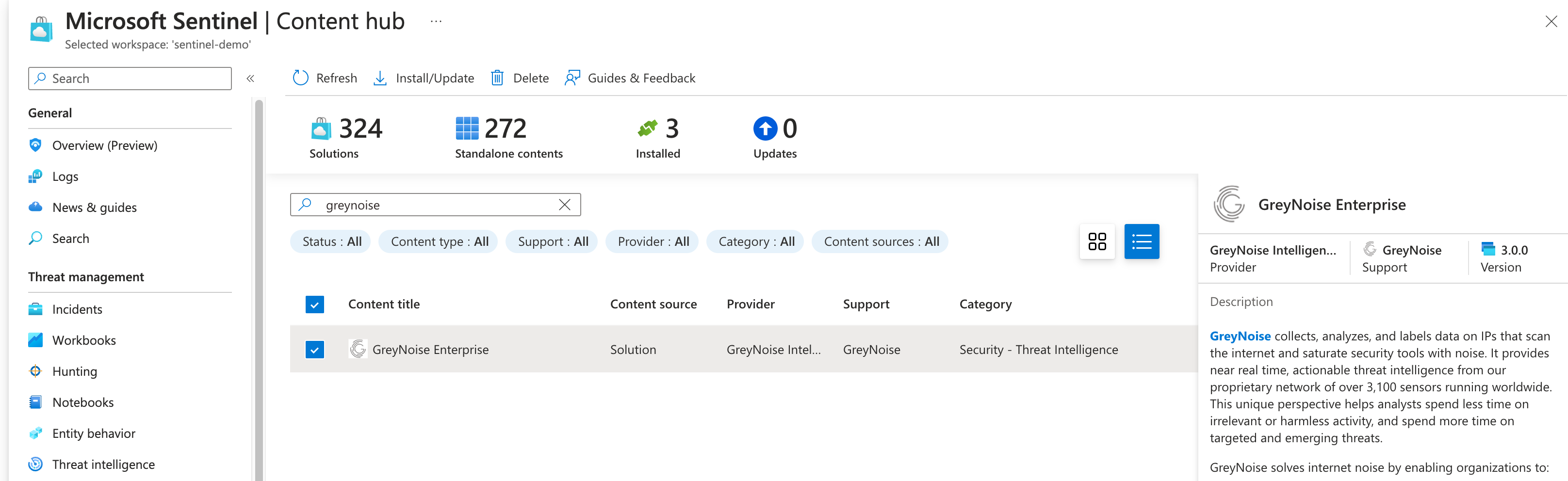
GreyNoise Pack on Sentinel Content Hub
Click the Install button from the Content Hub information to begin the process.
Once the installation is completed, the button will update to say Manage. Click the Manage button to continue with the setup process.
Deploy the Azure Function App
Note that currently the function app will run every night at midnight, and deploys to a Linux P2v2 App Service Plan. The function execution time will be configurable in a future version.
Select the Data Connector Entry on the list of items included with the pack, then click the Open Connector Page button.
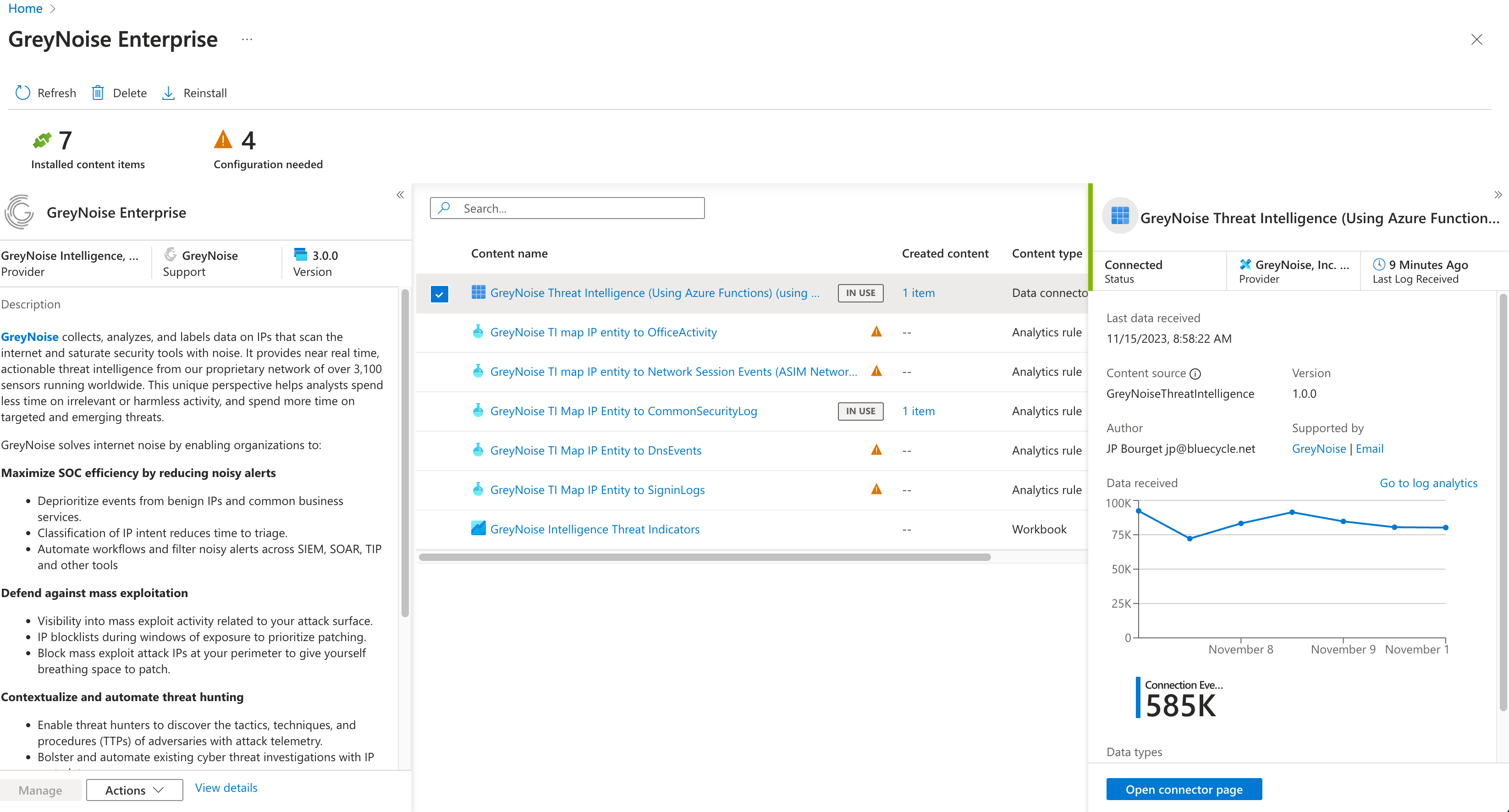
Follow the instructions as listed on the Data Connector page to finish all of the required configuration items, including:
- Retrieve your API Key from the GreyNoise Portal.
- Create an Azure Active Directory (AAD) application and acquire Tenant ID, Client ID
- Assign the AAD application the Microsoft Sentinel Contributor Role.
- Specify the AAD MS Graph permissions to enable MS Graph API access to the upload-indicators API. (ThreatIndicators.ReadWrite.OwnedBy)
- Deploy the Threat Intelligence (Preview) Solution, which includes the Threat Intelligence Upload Indicators API (Preview)
- Deploy the Azure Function
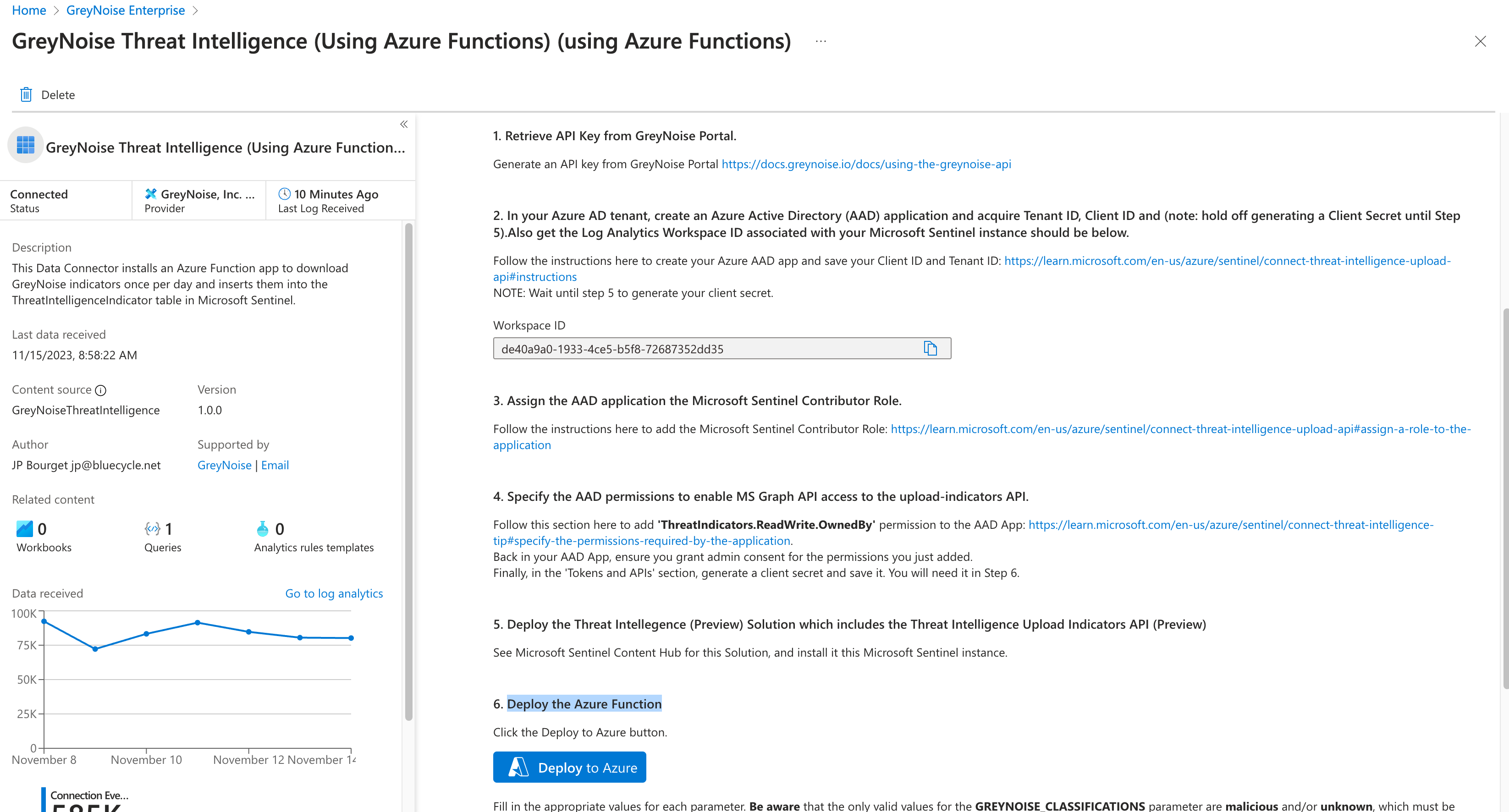
Clicking the Deploy to Azure button will open a Custom Deployment window where you will enter the information needed to configure the Function App.
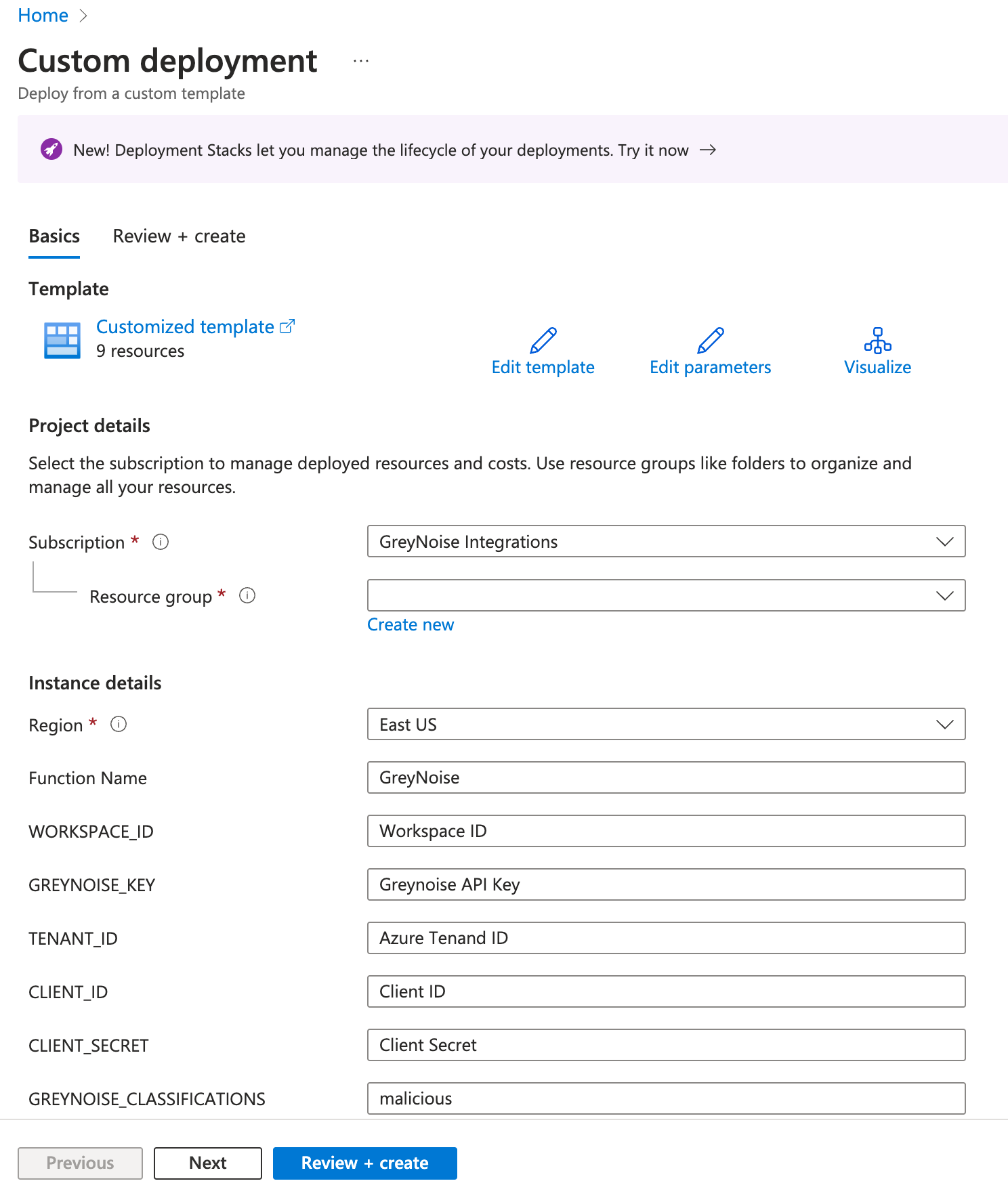
In the Custom Deployment window, enter:
- Region - this should be the default Region for your Azure Sentinel Instance and should populate by default
- Function Name - a helper name for the function app, you can use the default or give it another name
- Workspace ID - the value should be populated on the Data Connector instruction page after completing Step 2. This Workspace ID can also be found on the main page for your Sentinel Instance
- GreyNoise Key - this is your GreyNoise API key found on the GreyNoise Visualizer
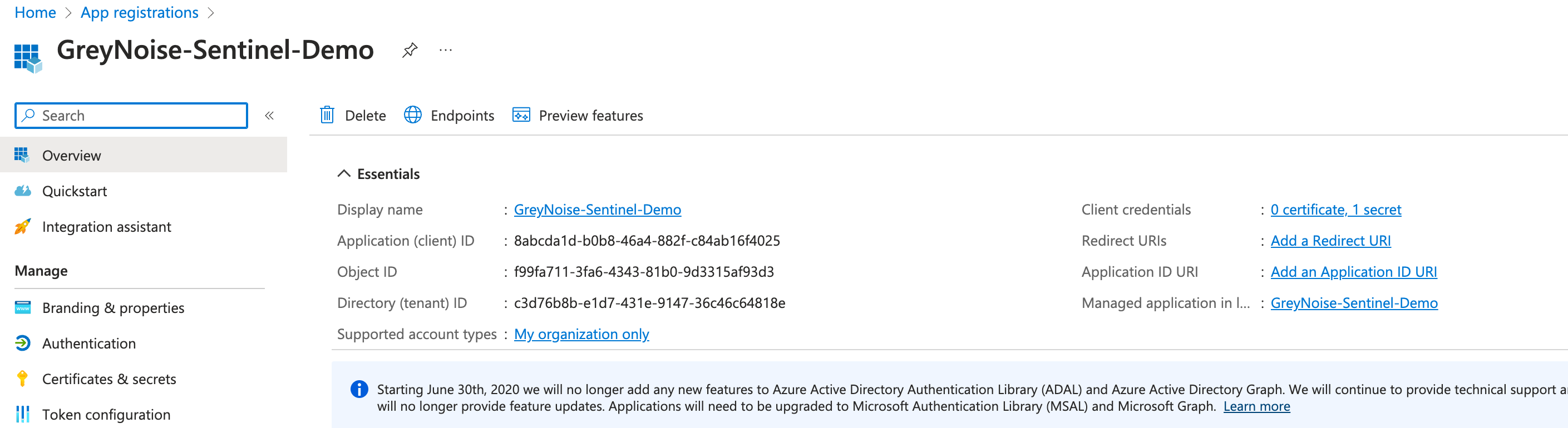
- Tenant ID - Can be retrieved from the App Registration window
- Client ID - Can be retrieved from the App Registration window
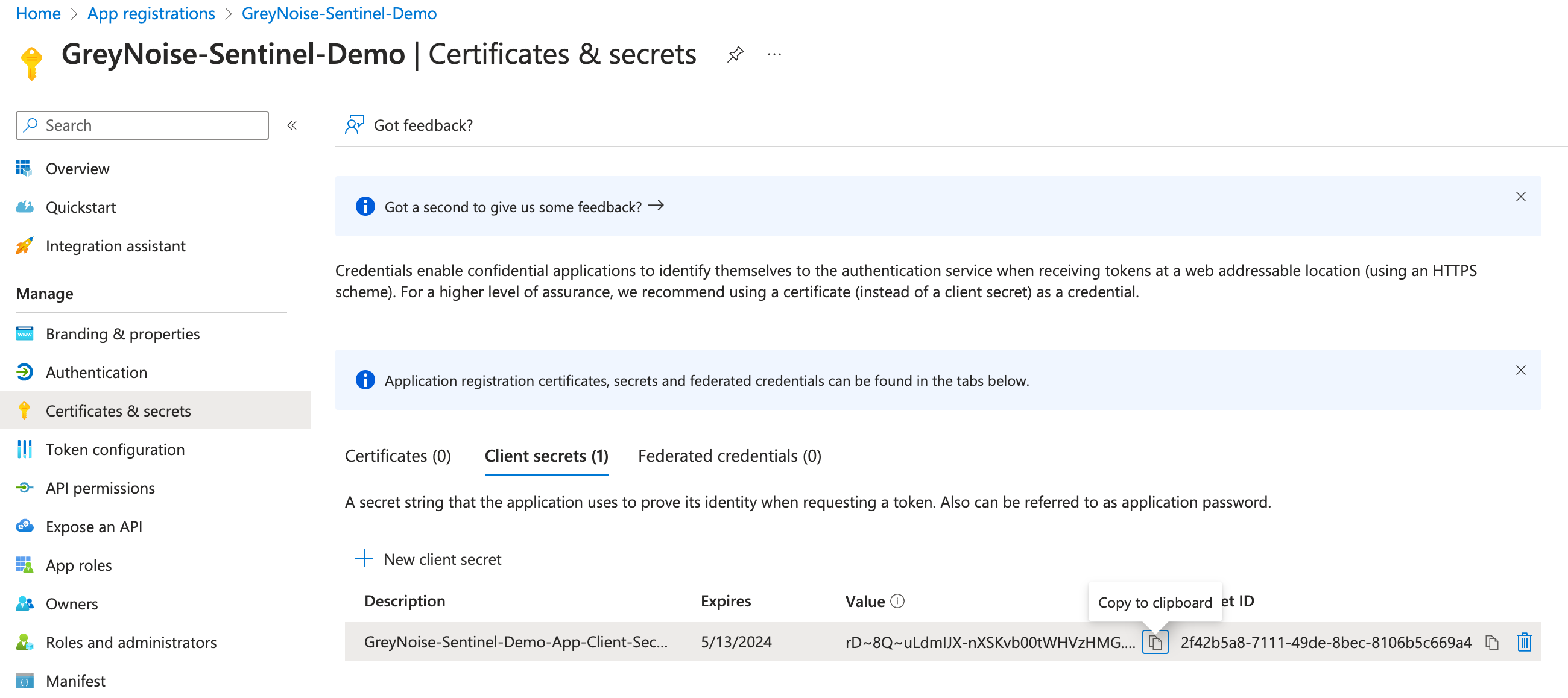
- Client Secret - Should be generated via the App Registration window, and the Value Entered here
- GreyNoise Classification - defaults to malicious but can be a comma-separated list containing malicious, unknown, and/or benign
Once all of the values are entered, click the Review button
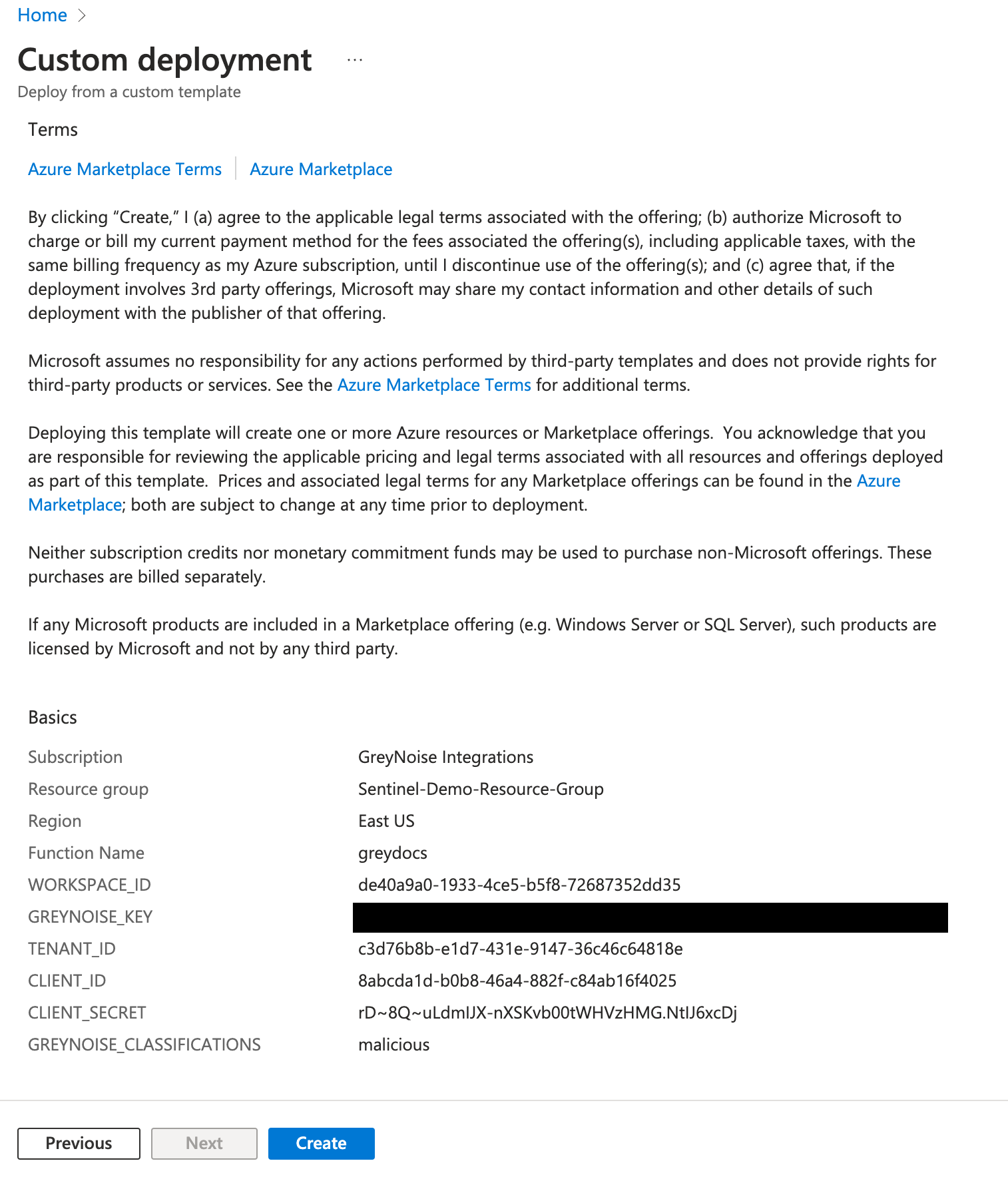
After a review of all the values, click Create to finish the process.
A "Deployment Completed" message will display once the resources have all been deployed.
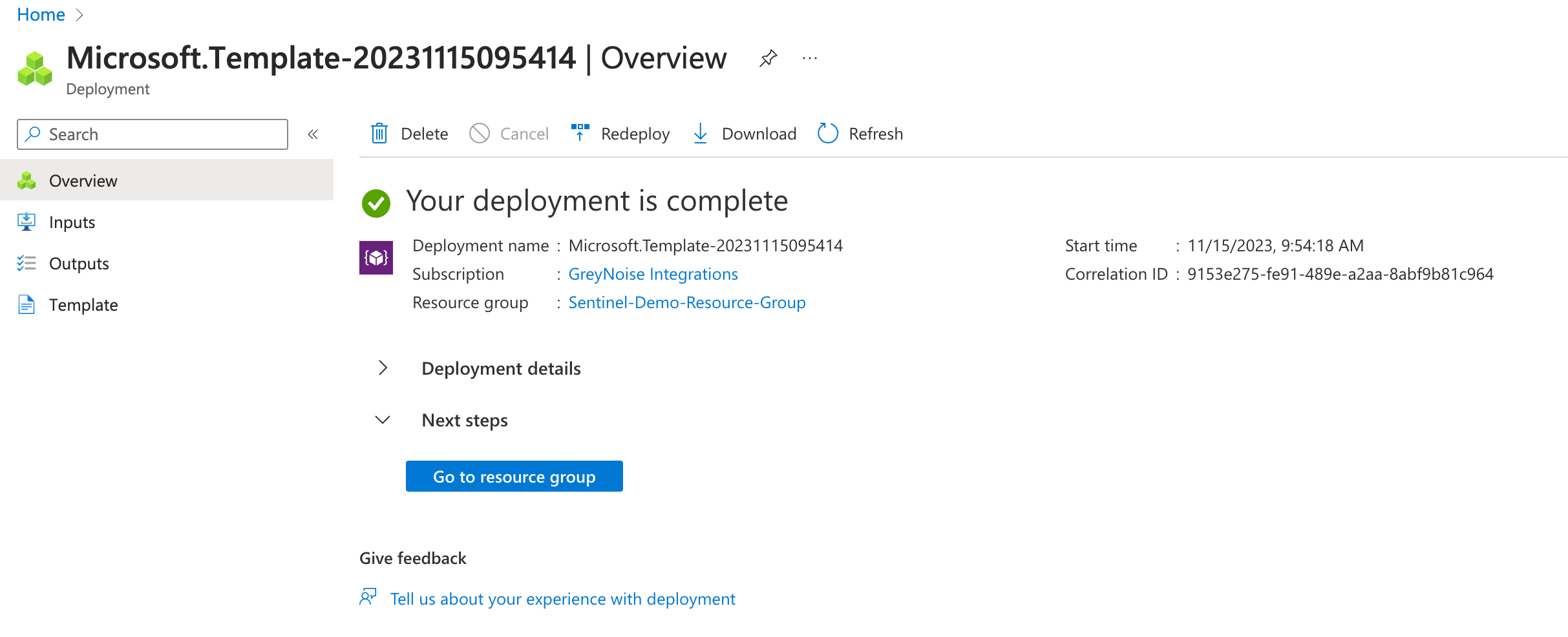
Manually testing the Function App
Since the Function App only runs on a set schedule, there may be a case to be able to run the app manually to confirm if everything is working as expected.
By default, the option to "Run" is disabled, and a cryptic message is shown:
Running your function in portal requires the app to explicitly accept requests from https://portal.azure.com. This is known as cross-origin resource sharing (CORS). Click here to add https://portal.azure.com to the allowed origin configuration
To grant the ability to run the app manually, follow these steps:
- Go to the Function App in the Azure Portal.
- Open API and then click CORS.
- Add https://portal.azure.com as an allowed origin and click Save
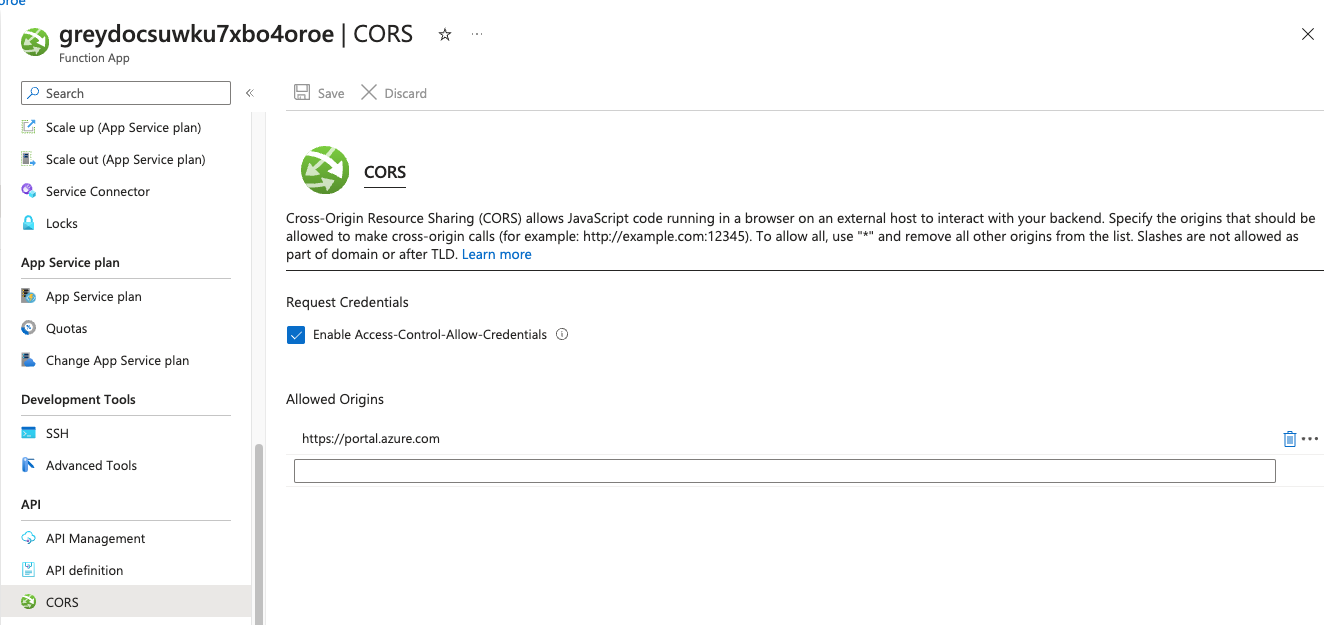
Once enabled, this now allows for the manual run of the function app.
Review the Indicators in Sentinel Threat Intelligence
When reviewing the indicators imported by the Function App, go to the Sentinel Threat Intelligence section and look for indicators that include the GreyNoise source.
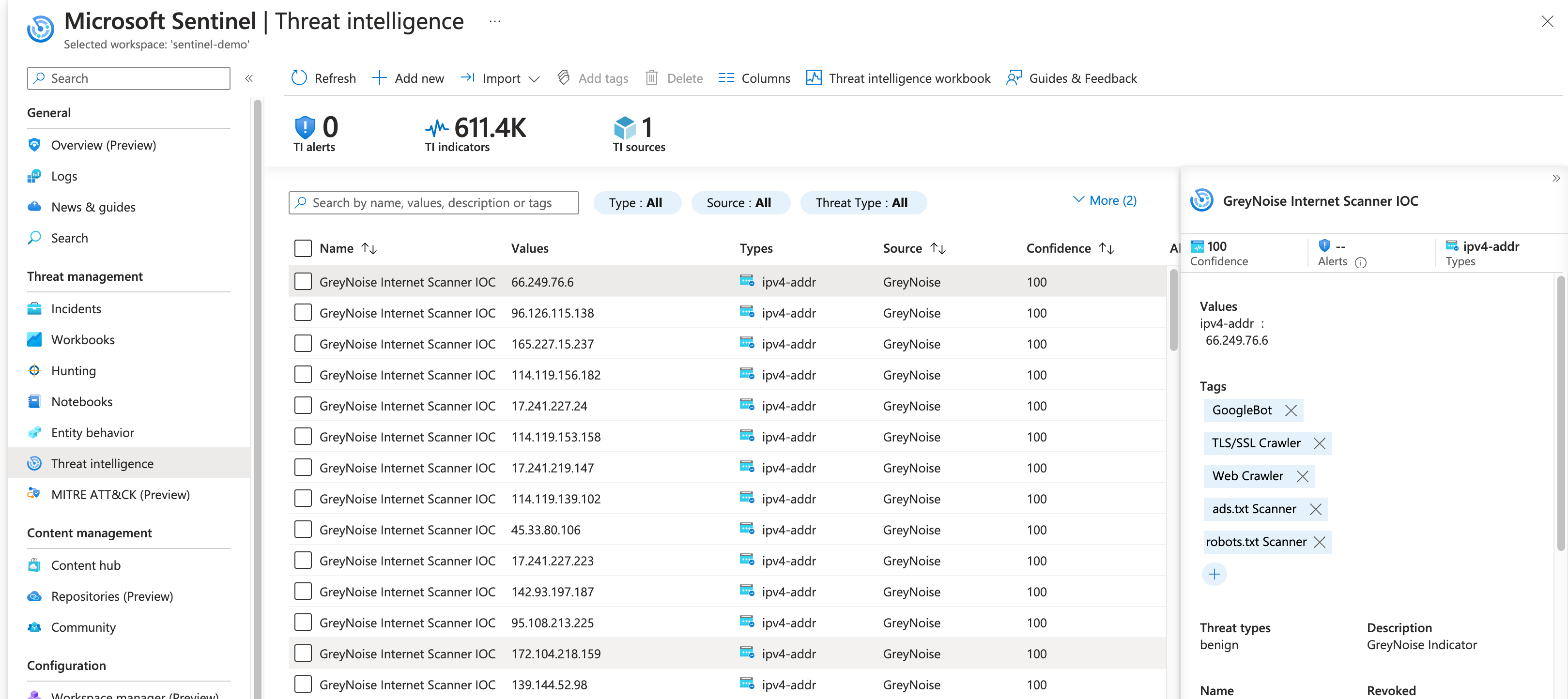
Some notes about these indicators:
- The Threat types value will contain the indicator classification
- The Tags will include all GreyNoise tags associated with the indicator
- The indicator will be "valid" for 24h after ingest
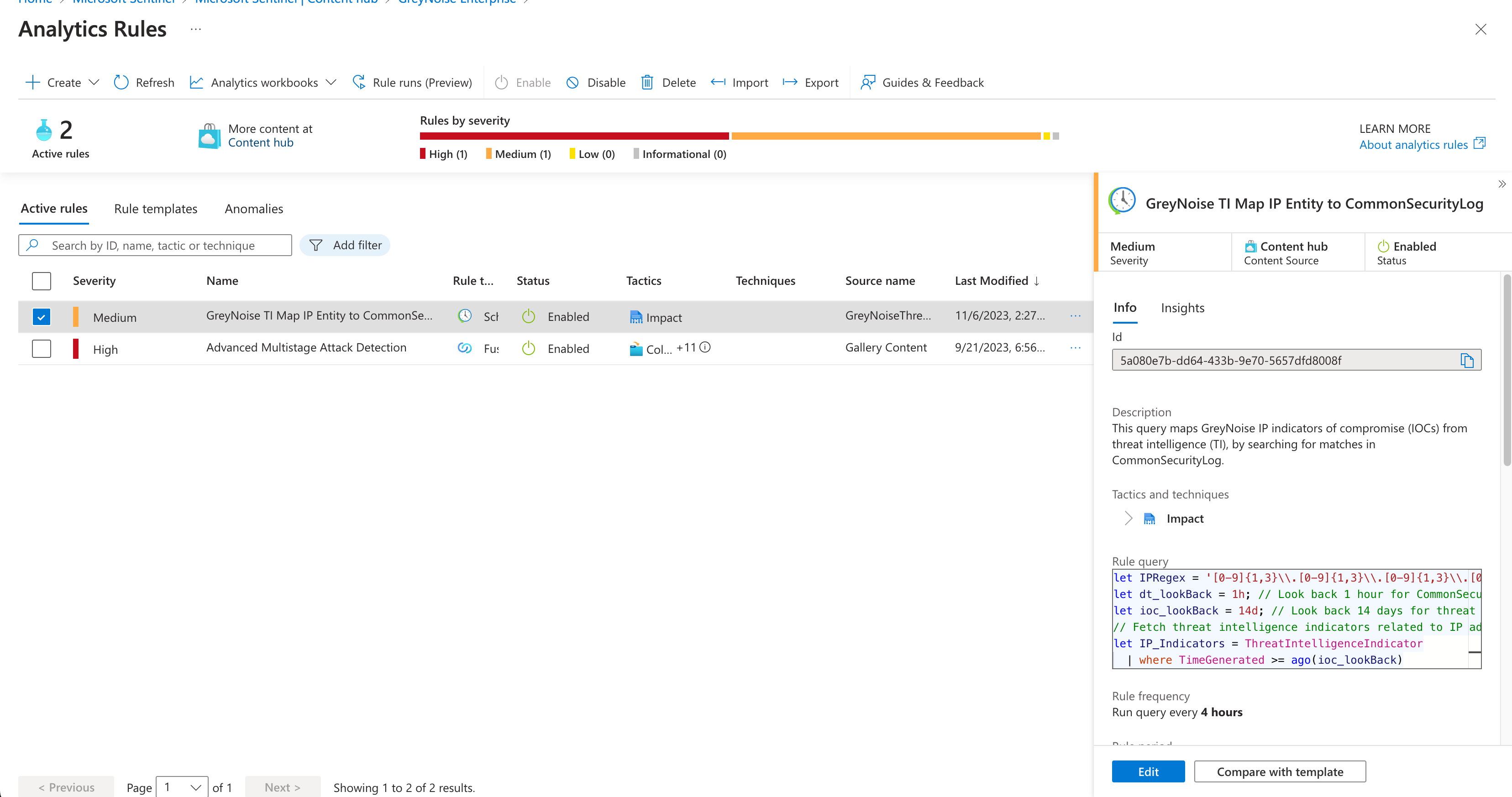
Analytics Rules
The Pack includes several analytics rules that can be used to match input sources to GreyNoise indicators.
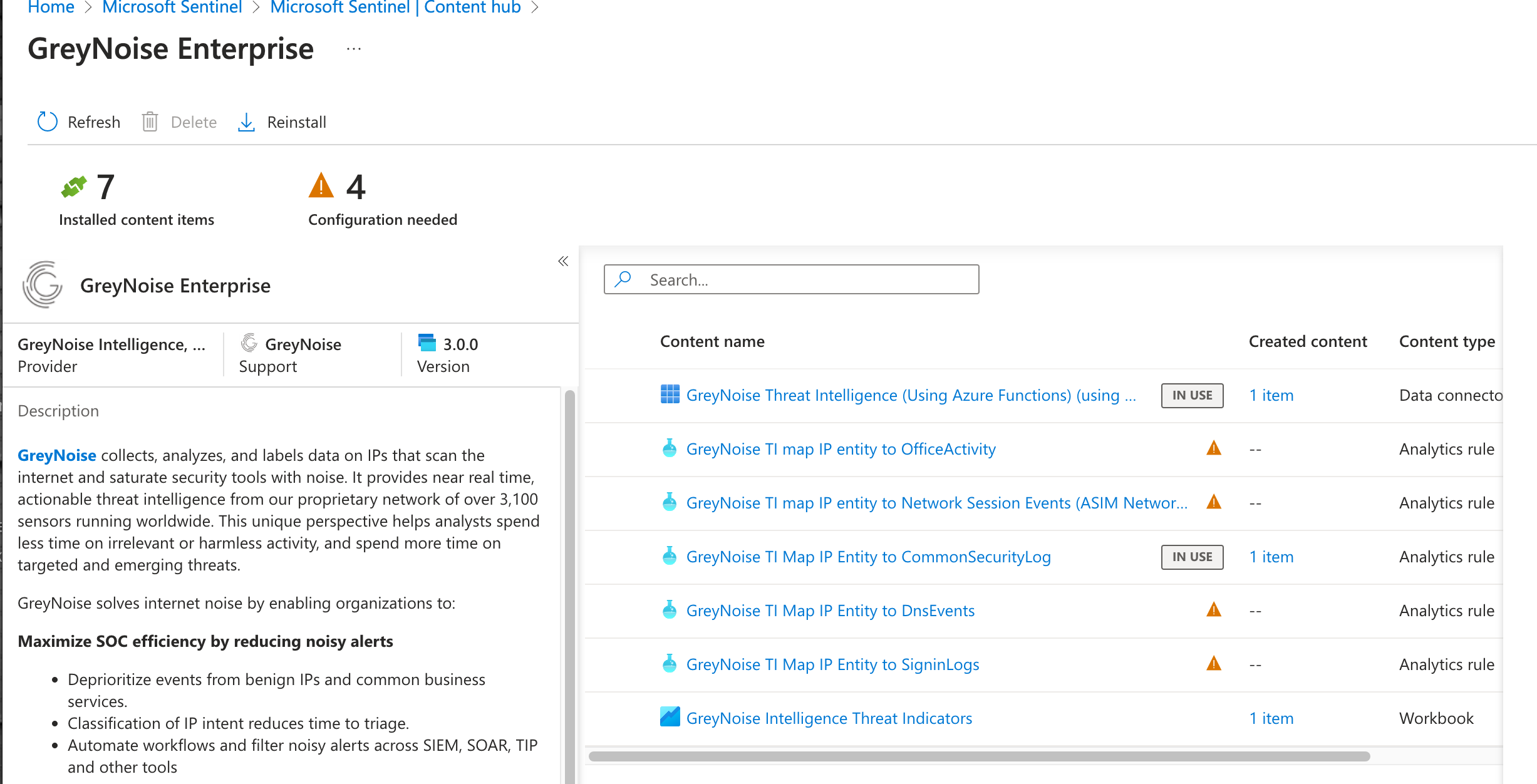
These can be installed as is or used as a template to create custom analytics rules.
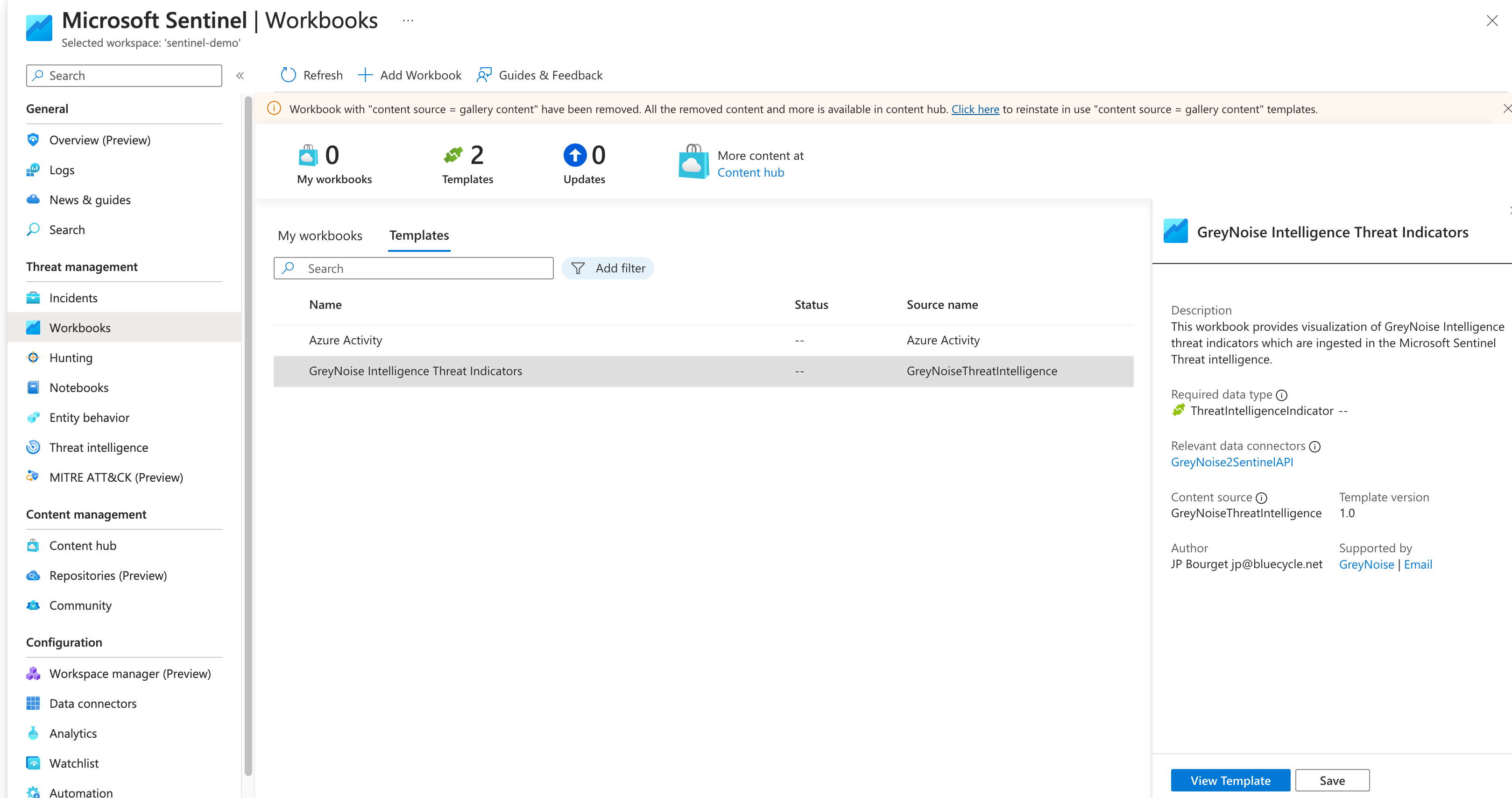
Workbooks
The Pack includes a Workbook that can be added to Sentinel. Under Workbook templates, find and install the GreyNoise Intelligence Threat Indicators Workbook.
Once installed, viewing the Workbook will provide some insight into the indicators ingested by the Feed:
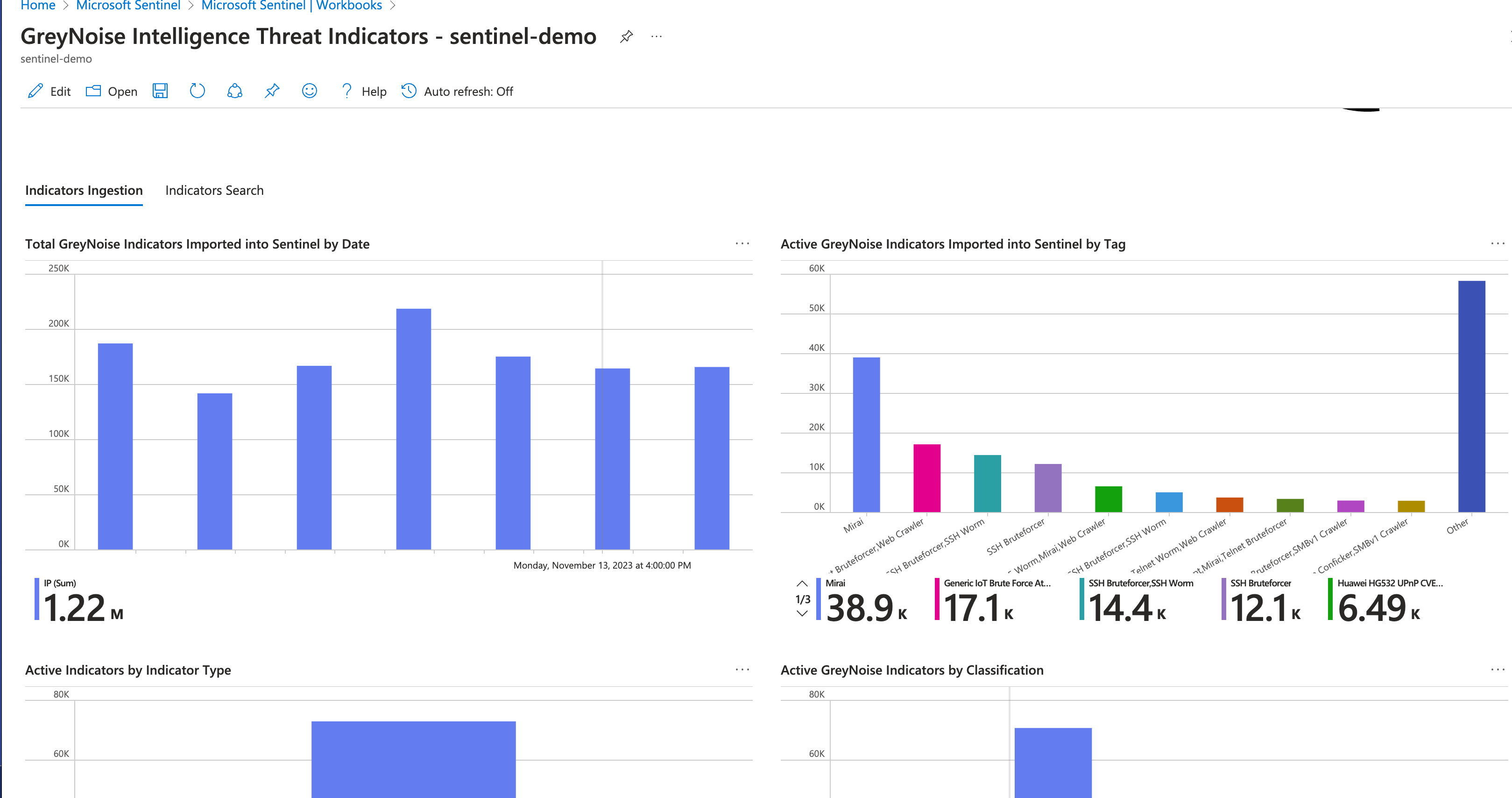
Note that there are two tabs: Indicators Ingestion and Indicators Search.
Updated about 1 year ago
