Firewall Blocking with GreyNoise Trends - old
Dynamic IP Blocking with GreyNoise Trends
GreyNoise Trends includes the ability to access a dynamic list of IPs that can be used in the Dynamic Block List feature in many of today's firewall products.
The blocklist URL is tied to a specific GreyNoise tag, providing a dynamically updated list of IPs that have been observed scanning for the specific tag activity in the last 24 hours.
To obtain the blocklist URL for a tag, navigate to the GreyNoise Trends page for the tag you want to dynamically block.
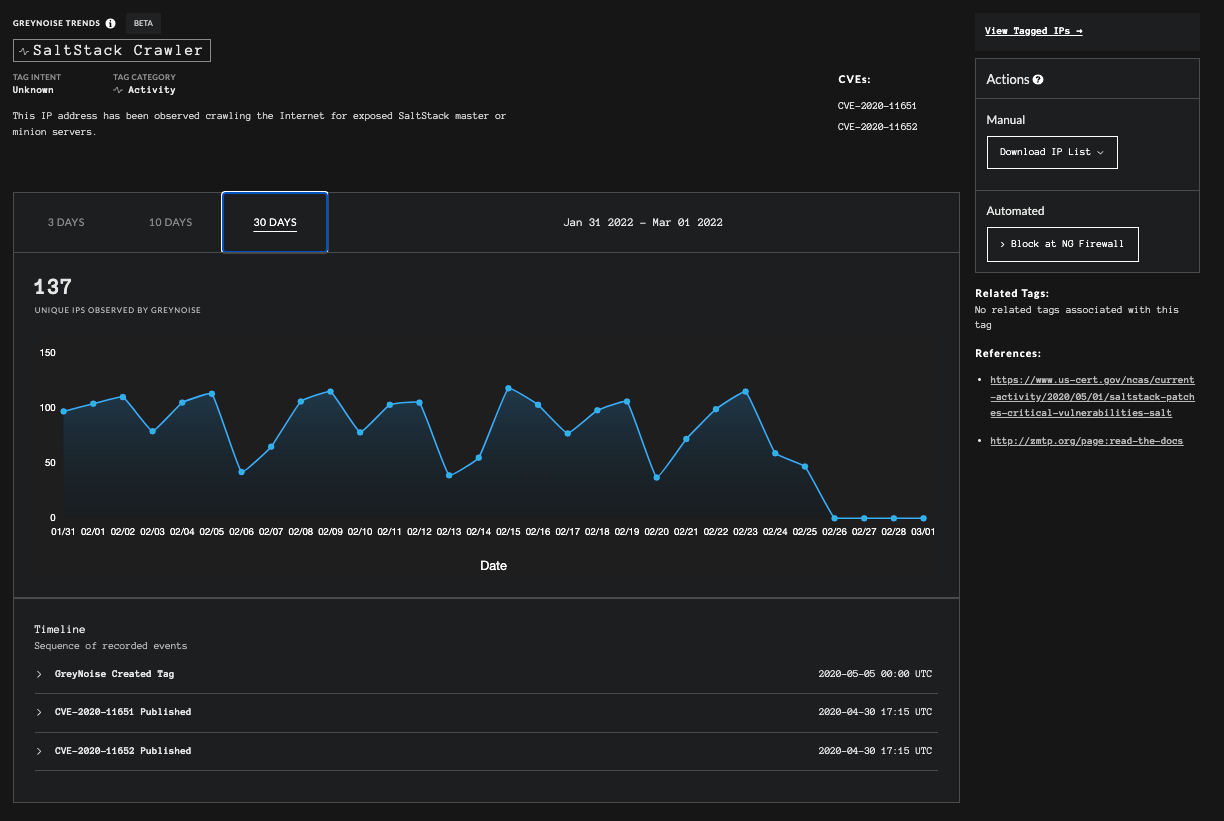
GreyNoise Trends page for Tag SaltStack Crawler
In the Actions section on the right-hand column there are two different components:
- Manual, which allows you to download a file containing the current list of IPs scanning in the last 24 hours
- Automatic, which allows you to grab an URL that can be used for Dynamic Block Lists.
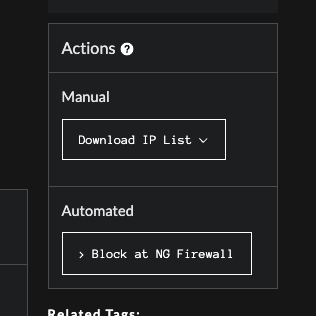
Actions Section of GreyNoise Trends
From the Automated section of the Actions box, click the Block at NG Firewall link. This will open the details on the automated blocking feature. Depending on your account type, your user experience may vary slightly:
For those with access to Unlimited Blocklist URLs, a URL will be immediately available to be copied.
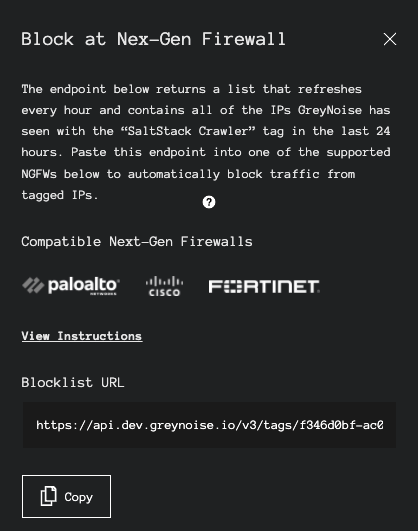
Block at Next-Gen Firewall Slide Out with no subscription
For those with access to a limited number of Blocklist URLs, a subscribe button will be presented. Once subscribed to a tag, the URL will be visible.
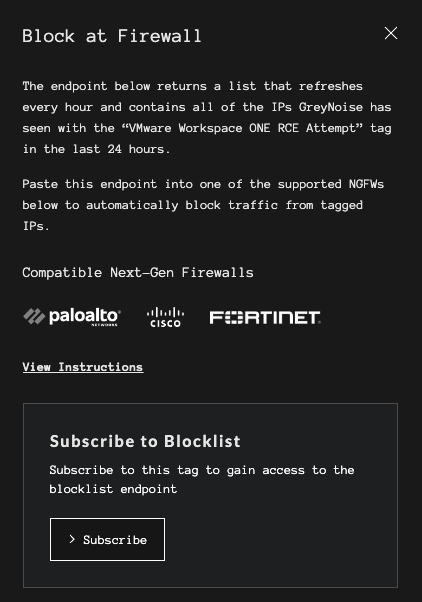
Block at Next-Gen Firewall Slide Out with subscription
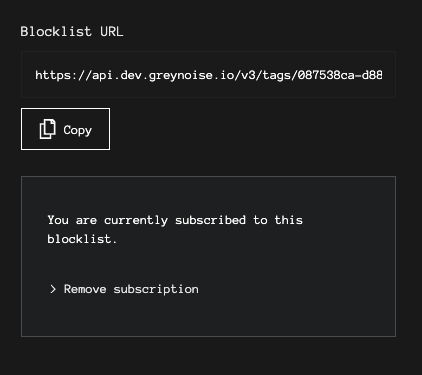
Blocklist URL visible after subscription.
Tag subscriptions for the Trends Blocklist URLs can be viewed on the Account page.
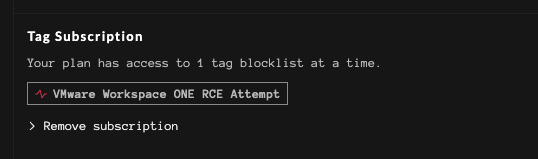
Current tag subscriptions viewable on the Accounts page.
At the bottom of the screen, select the Copy button to capture the URL to use for the Dynamic Block List.
This URL can now be used to populate Dynamic Block Lists on most major firewalls. Here are some links to additional vendor-specific documentation that shows how to apply this URL to a blocklist.
Auth Tokens in Blocklist URLsWhen copying a Blocklist URL, an authentication token will be included as part of the URL so that additional authentication steps do not need to be taken when using this feature.
Palo Alto Networks
Cisco ASA
Fortinet Fortigate
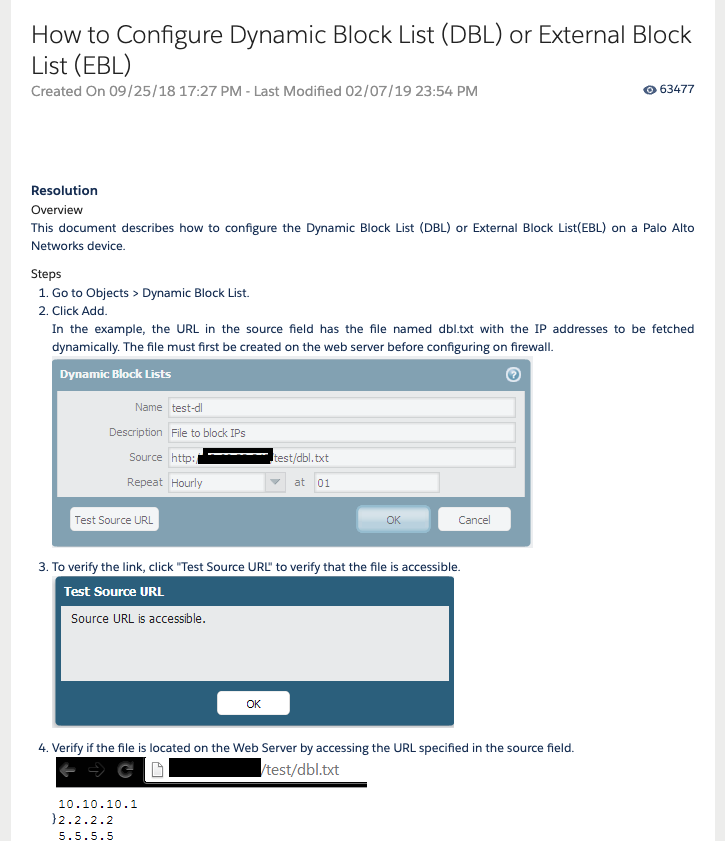
Vendor Configuration Sample
Other Products / UsageThe blocklist feature provides a dynamic list of IPs delivered via a static URL that can be used in any product that can query the URL and ingest the list of IPs. The products listed above are just samples of technology that supports this, but many other products do as well. Custom scripting can also be used to combine multiple blocklist URLs into a single list to pass to a product for blocking.
Updated 10 months ago
