Discover Emerging Threats
Use Case: Discover Emerging Threats
Listening to the internet allows GreyNoise to uncover unique behaviors and TTPs. We capture vulnerability lifecycles with our tags to show when scanners are looking for opportunities to exploit recently announced vulnerabilities. For example, when the F5 vulnerability was announced, our team quickly created tags to identify IPs scanning for targets to exploit. Teams can also dynamically research our data using GNQL, the GreyNoise query language.
Another common example is when a new CVE is released, that CVE can be queried each day to see the total number of IPs that are scanning for it, so a team can assess how critical this threat is to their organization and if a "break-the-glass" protocol should be enacted.
Scenario 1: Use GreyNoise Visualizer and CLI to Query the GreyNoise dataset
An analyst uses the GreyNoise Visualizer to monitor trends being tracked within GreyNoise and can also do advances queries for the Visualizer and CLI to aid in Threat Hunting or Incident Response.
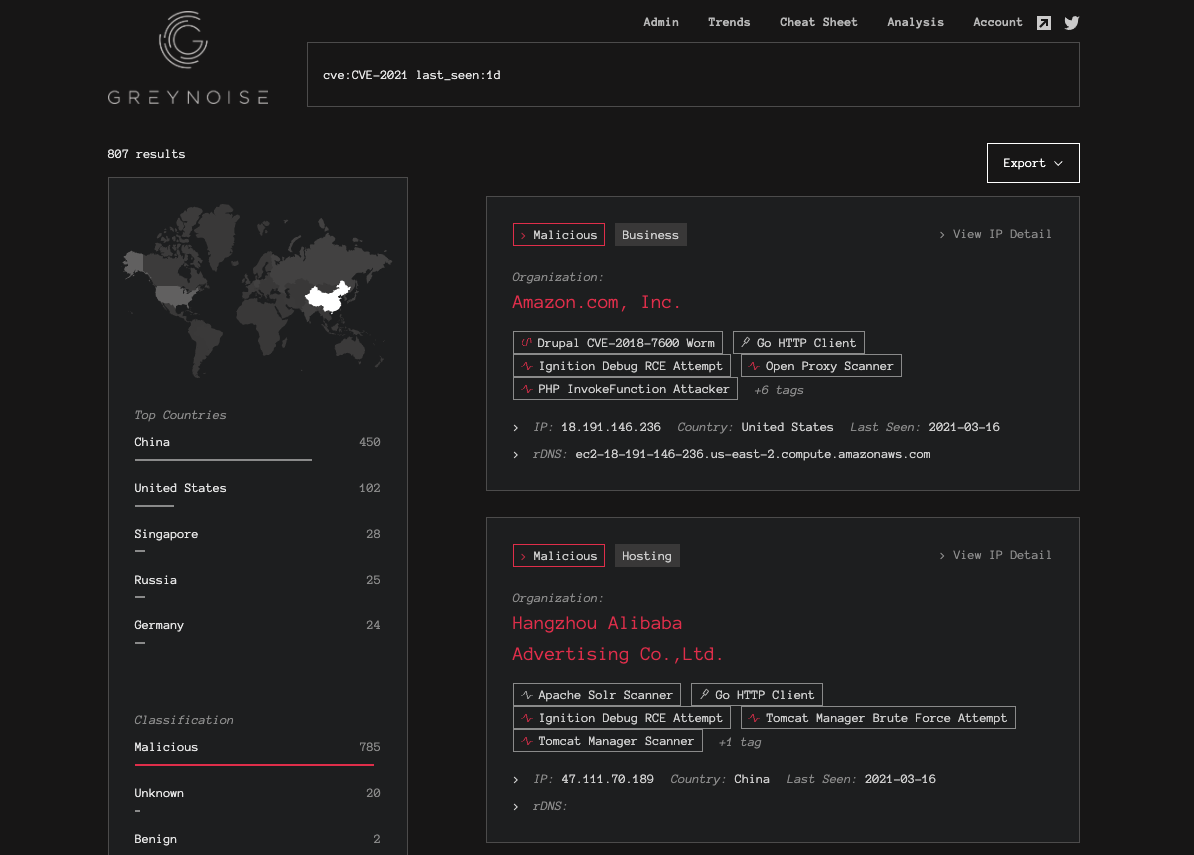
Querying the GreyNoise Visualizer daily for any new CVE tags/hits
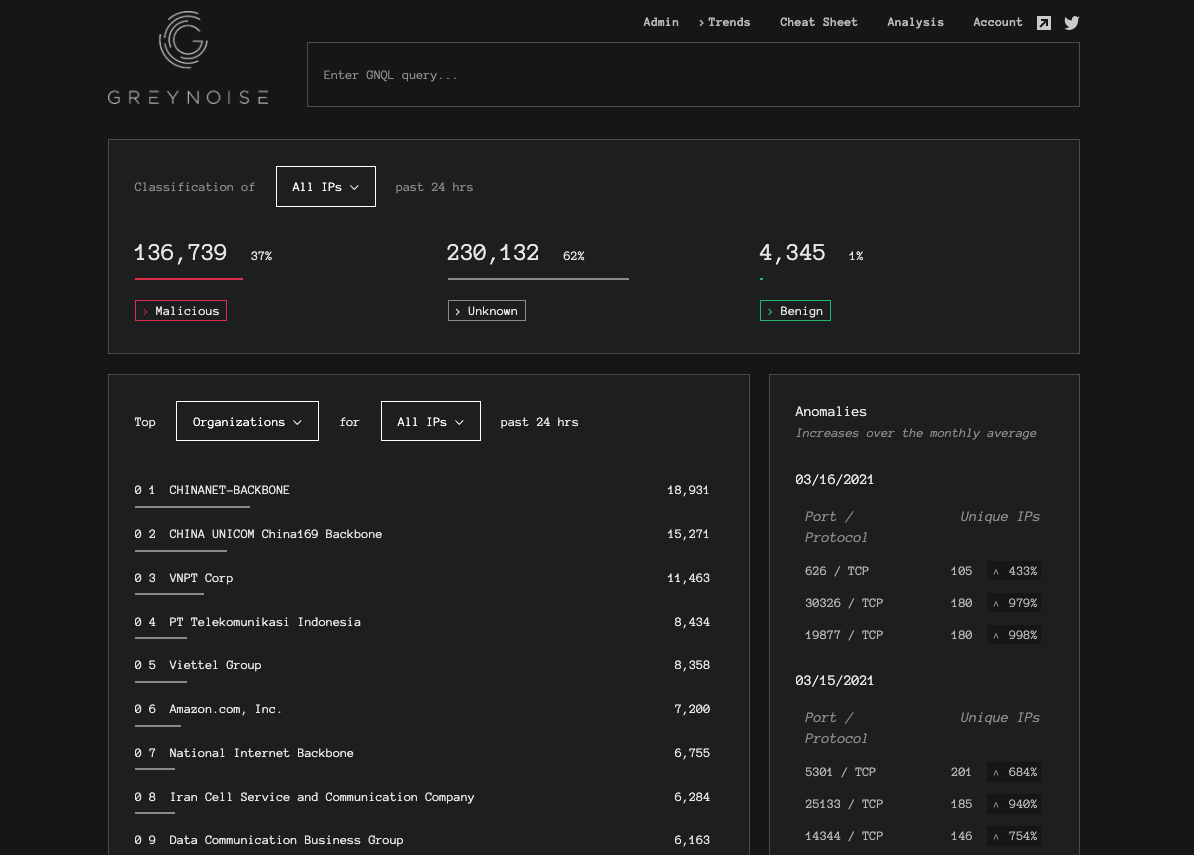
Reviewing the GreyNoise trends page for anomalies and trends.
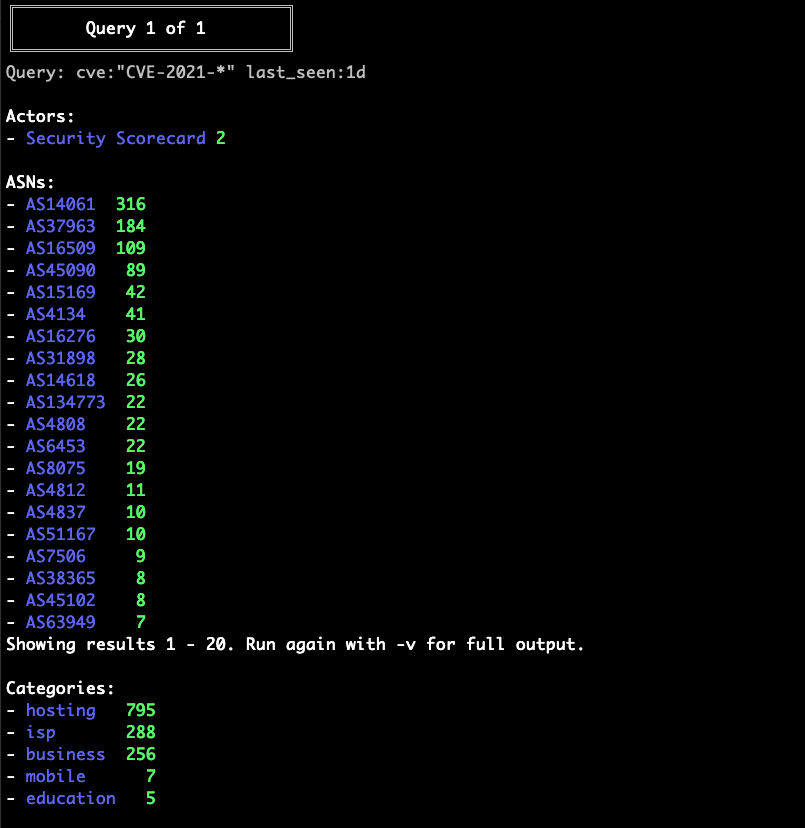
Using the GreyNoise CLI to view GNQL Stats for CVEs detected in the last day
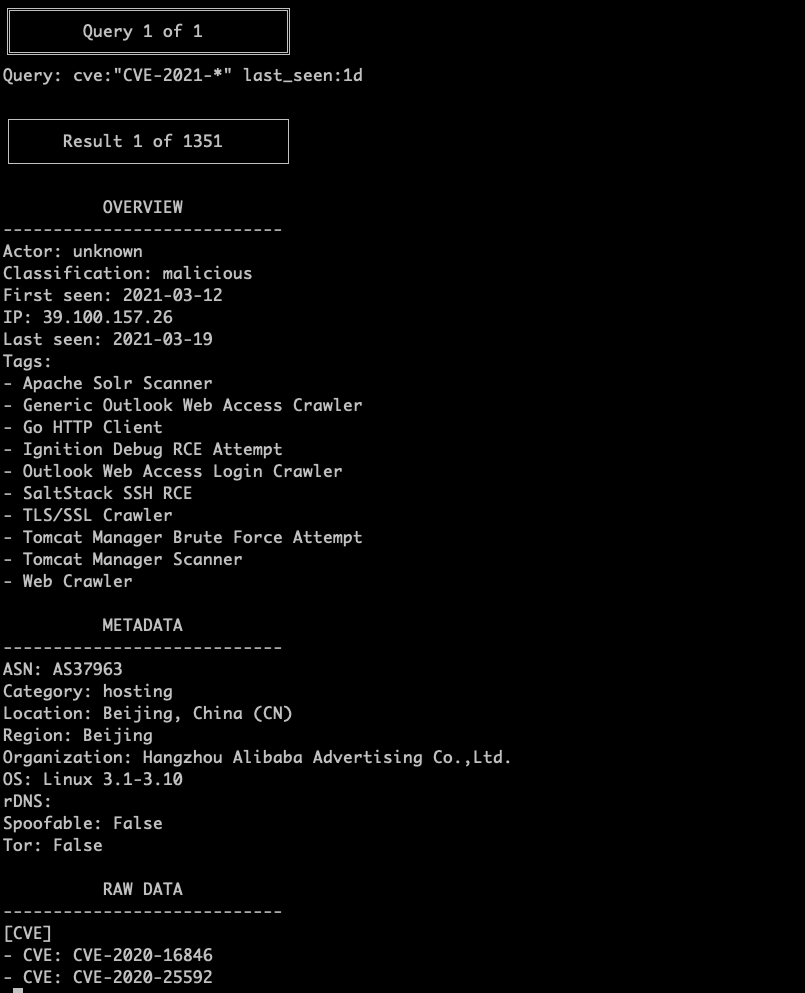
Using the GreyNoise CLI to view GNQL IP Context Data for CVEs detected in the last day
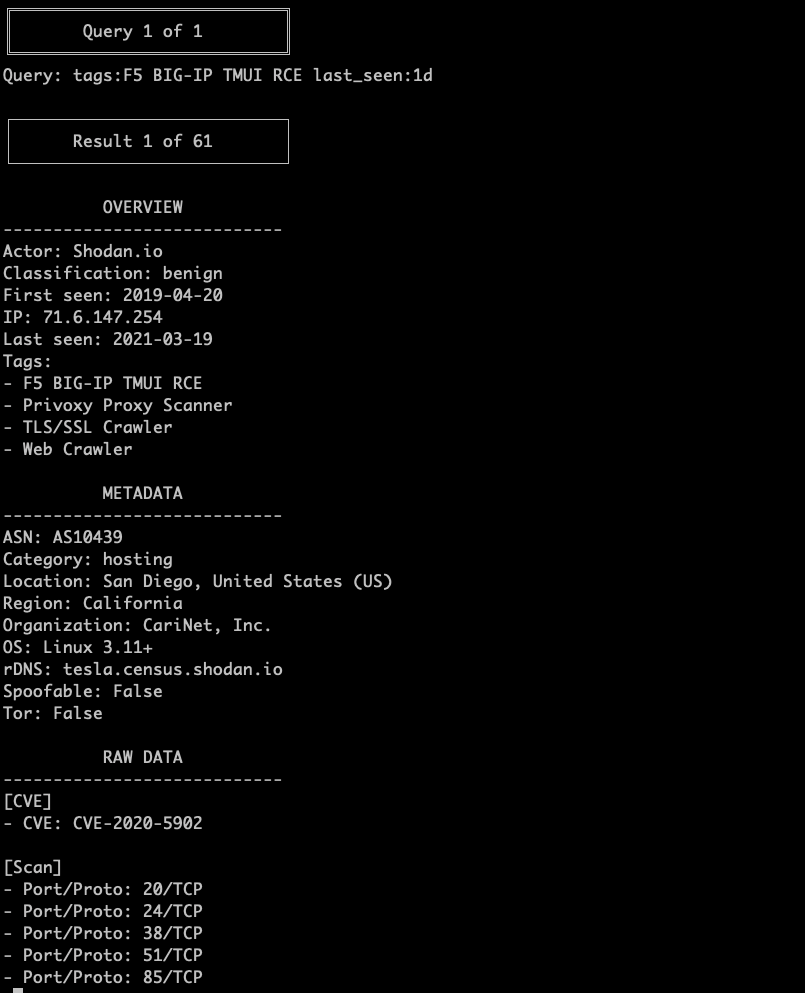
Using the GreyNoise CLI to view GNQL IP Context Data for GN Tag: F5 BIG-IP TMUI RCEs detected in the last day
Scenario 2: Create a GreyNoise Alert to notify on CVE activity
In some cases, GreyNoise may add Tags and CVE profiles before the scanning behavior is seen or is very minimal. Using GreyNoise Alerts, you can be notified via email when GreyNoise sees activity matching a CVE or Tag and prioritize threat responses in your organization.
You can enable this by configuring an alert similar to cve:CVE-2021-12345 spoofable:false.
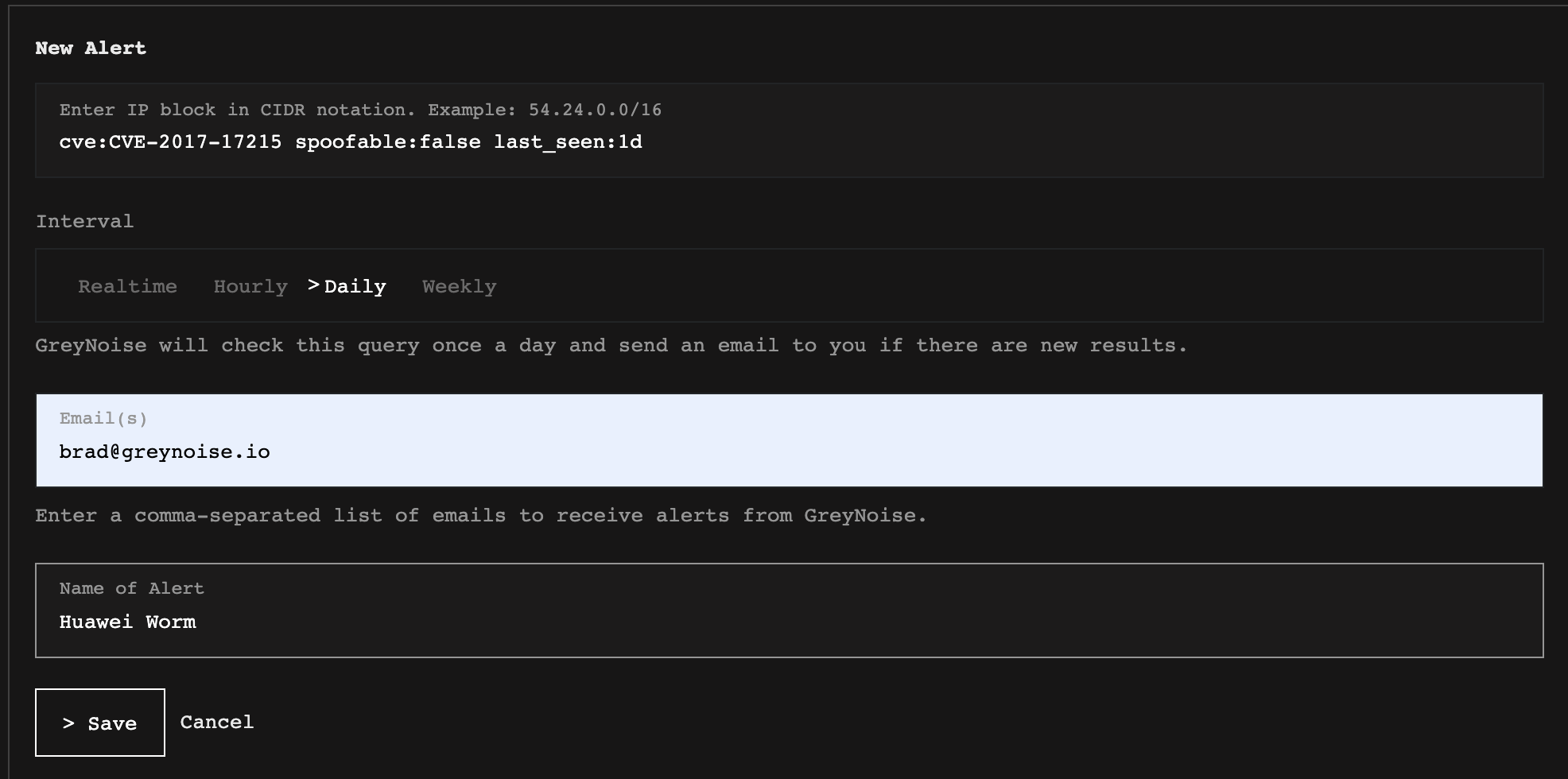
Creating a new alert in the GreyNoise Visualizer
This can also be done using tags, to inform you when scanning activity begins for a specific tag, such as tags:"Exchange ProxyShell Vuln Attempt"
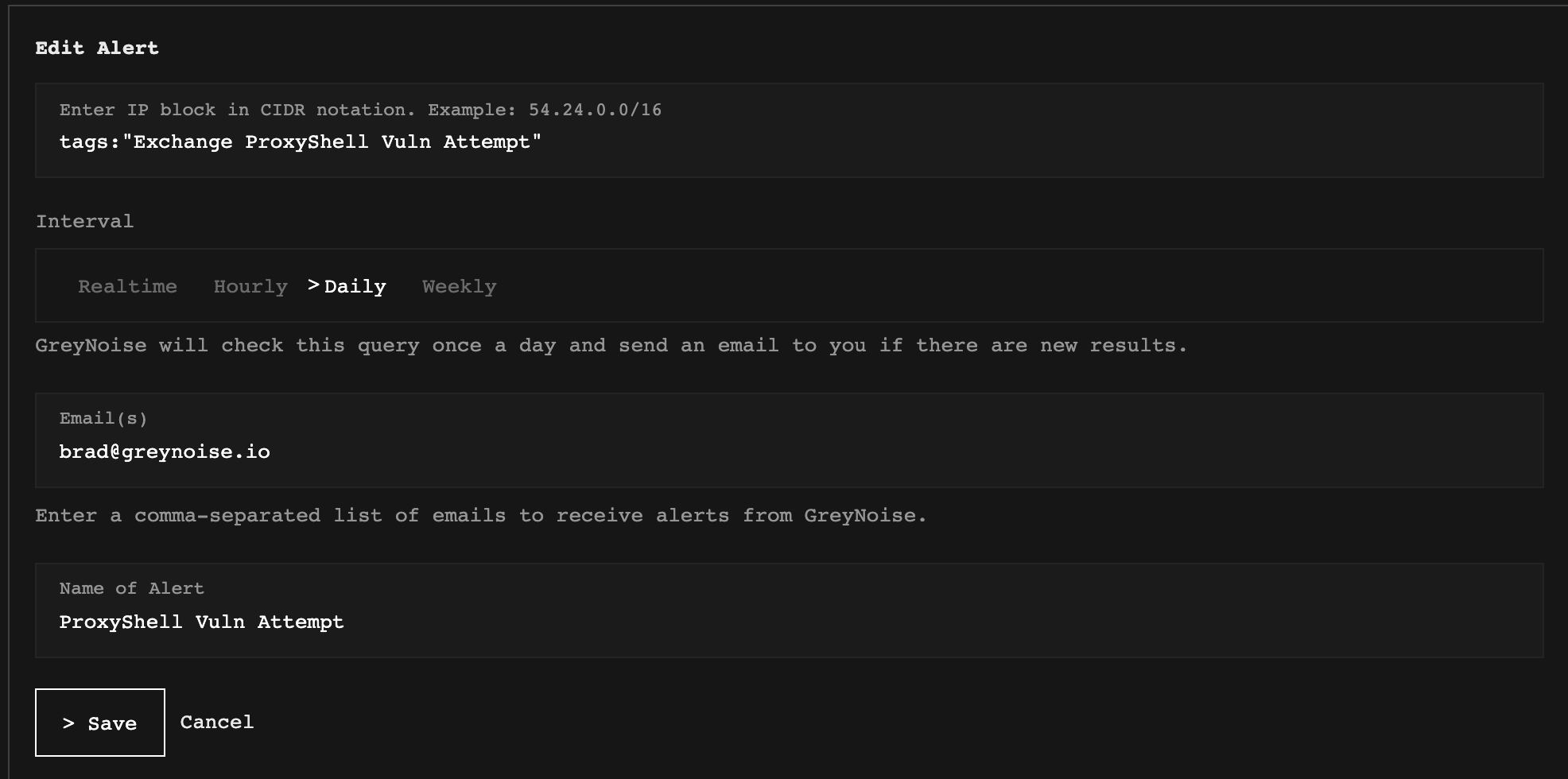
Editing an alert in the GreyNoise Visualizer

Sample alert email notification received from GreyNoise
Updated about 1 year ago
