Understanding GreyNoise Classifications
For each IP address in the GreyNoise Internet Scanner Intelligence data set, a classification key is included in the GreyNoise Visualizer and the GreyNoise APIs. The following explains how GreyNoise classifies IPs within the Internet Scanner Intelligence data set.
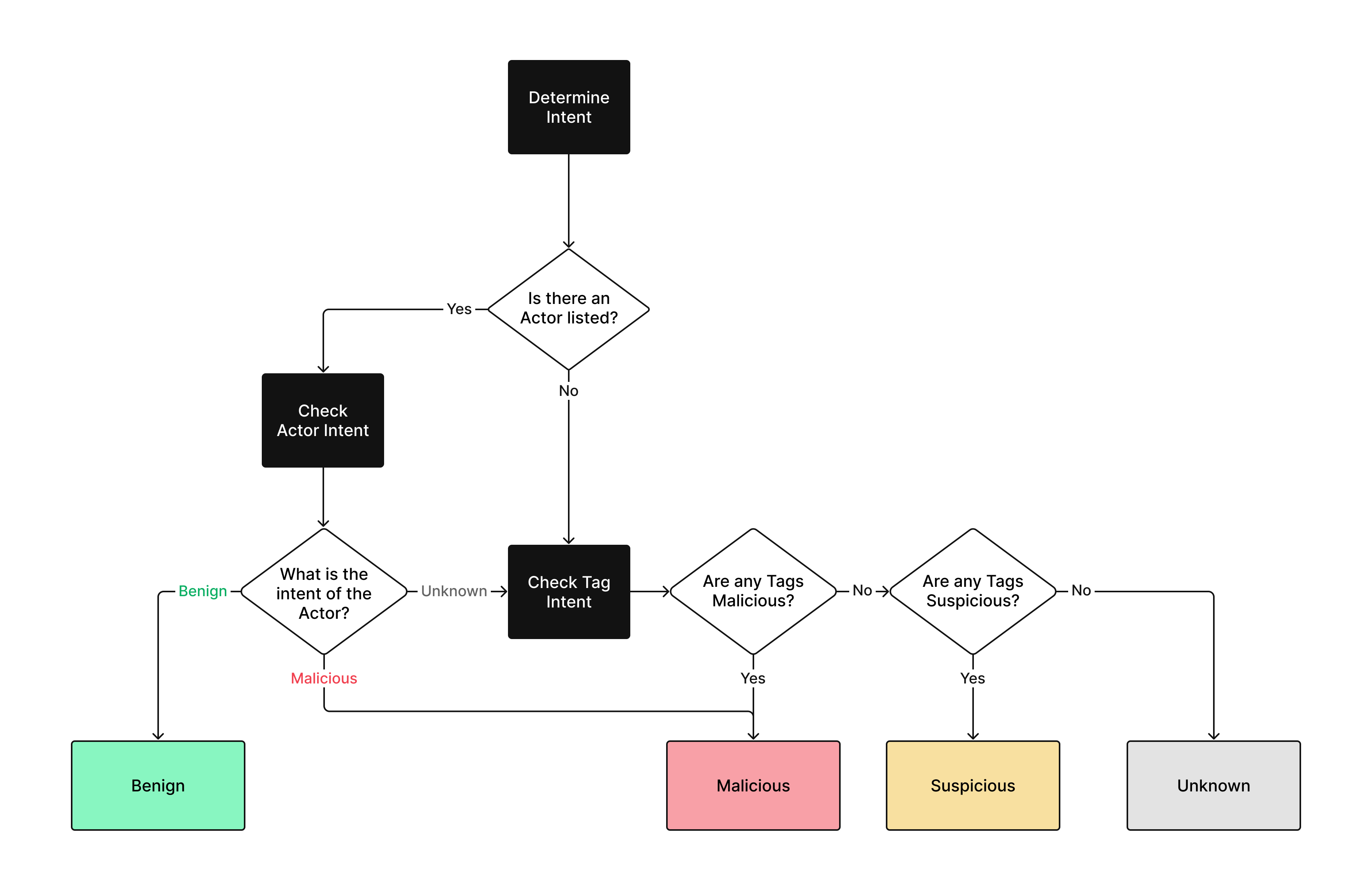
GreyNoise Classification Selection Flow Diagram
Classification Criteria
The benign classification for an IP address is applied using knowledge about the Actor associated with the IP. The Actor must meet the below criteria:
- Is a legitimate company, search engine, security research organization, university, or individual
- GreyNoise has determined that the actor is trustworthy
- The actors' website includes some kind of opt-out functionality
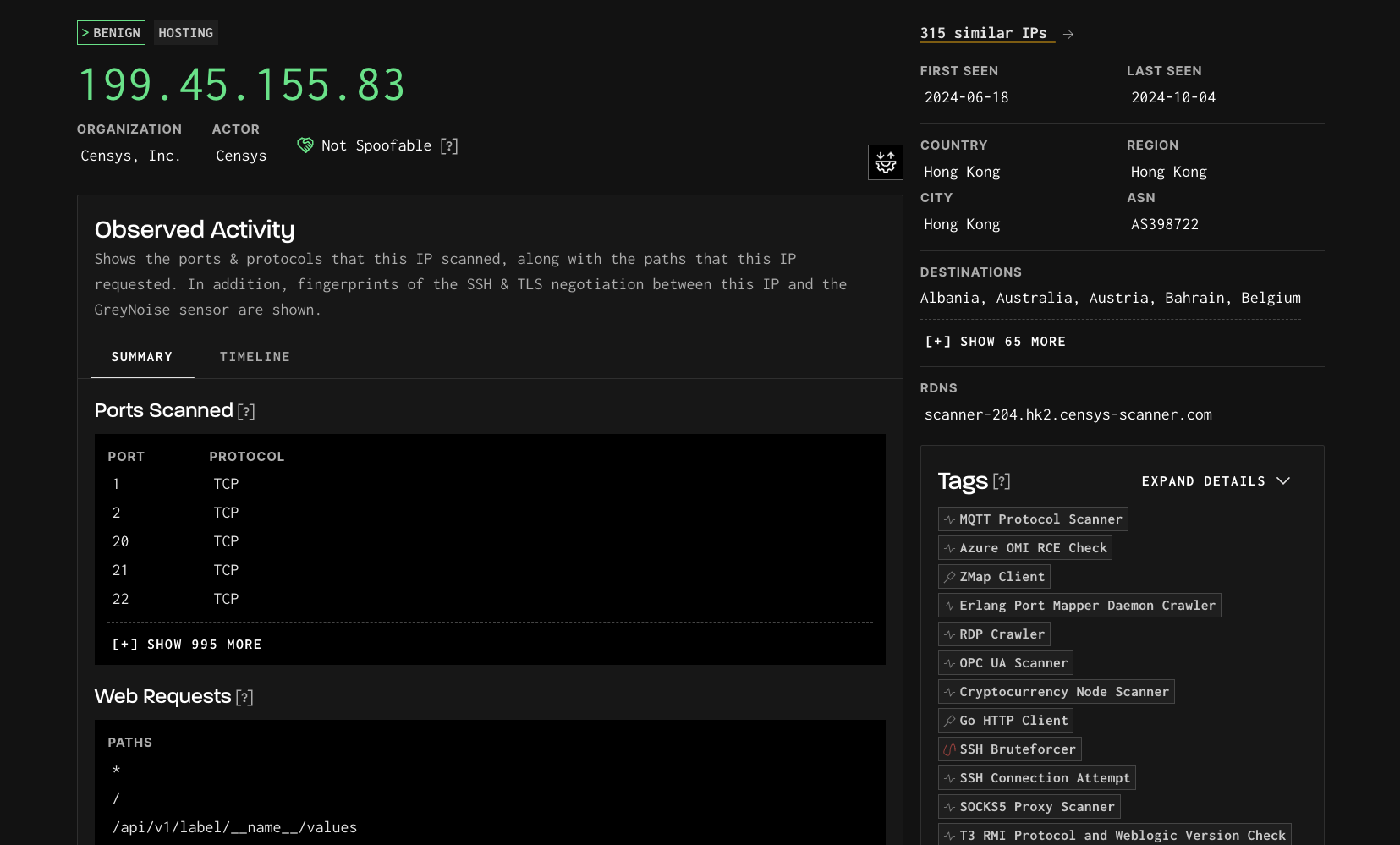
Benign IP in the GreyNoise visualizer.
Benign actors and malicious tagsThe benign classification takes precedence over malicious tags. Certain benign actors perform checks that would be malicious (e.g., checking admin:admin credentials against SSH) if they were coming from an unknown source.
GreyNoise periodically audits actors and will revoke a benign classification if their intent crosses a line into questionable activity.
Some benign examples include:
- Search engine crawlers such as GoogleBot
- Universities such as the University of California Berkeley
- Security researchers such as Alpha Strike Labs
An IP address's malicious classification is determined by its associated tags, which capture behaviors GreyNoise has directly observed an IP address engage in. Some GreyNoise tags are classified as having "malicious" intent for harmful behaviors seen. If an IP address is not classified as benign and has at least one malicious tag, it is classified as malicious.
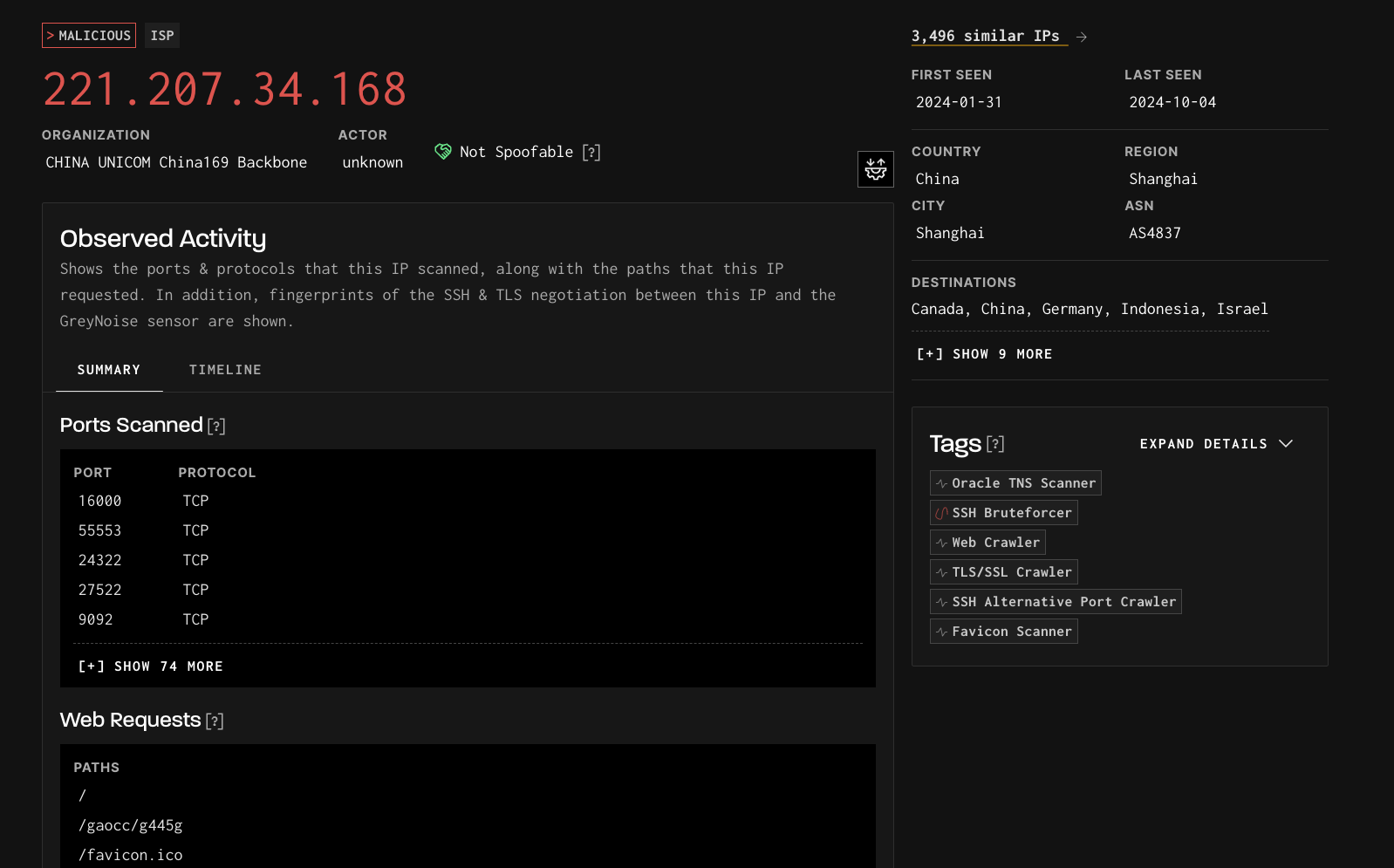
Malicious IP in the GreyNoise visualizer.
Traffic identified as suspicious by GreyNoise indicates activity that lies between clearly malicious and benign behavior. This activity involves systematic probing or enumeration, distinguishing it from random internet background noise. This classification serves as contextual intelligence rather than an immediate call to action.
Characteristics of Suspicious Traffic
- Reconnaissance activity targeting specific vulnerabilities without active exploitation
- Unsolicited connection attempts from unidentified sources
- Service enumeration with debug parameters
- Remote access point discovery attempts
- Traffic from IPs not associated with known benign scanning services
Investigation Context
When GreyNoise labels traffic as suspicious, it indicates potential reconnaissance or pre-attack behavior. While this classification alone may not warrant immediate investigation, it provides valuable context when:
- Correlating with other security events
- Analyzing patterns of behavior
- Evaluating potential targeted activities
Usage Guidelines
Security teams should:
- Use suspicious traffic data to enrich existing investigations
- Consider this classification alongside other threat intelligence
- Monitor for escalation in behavior patterns
- Cross-reference with targeted traffic analysis

Suspicious IP in the GreyNoise Visualizer.
IPs not classified as Benign, Malicious, or Suspicious under the above criteria are classified as Unknown. The other three classifications are highly vetted, so any other IP seen engaging in internet scanning behavior is classified as Unknown.
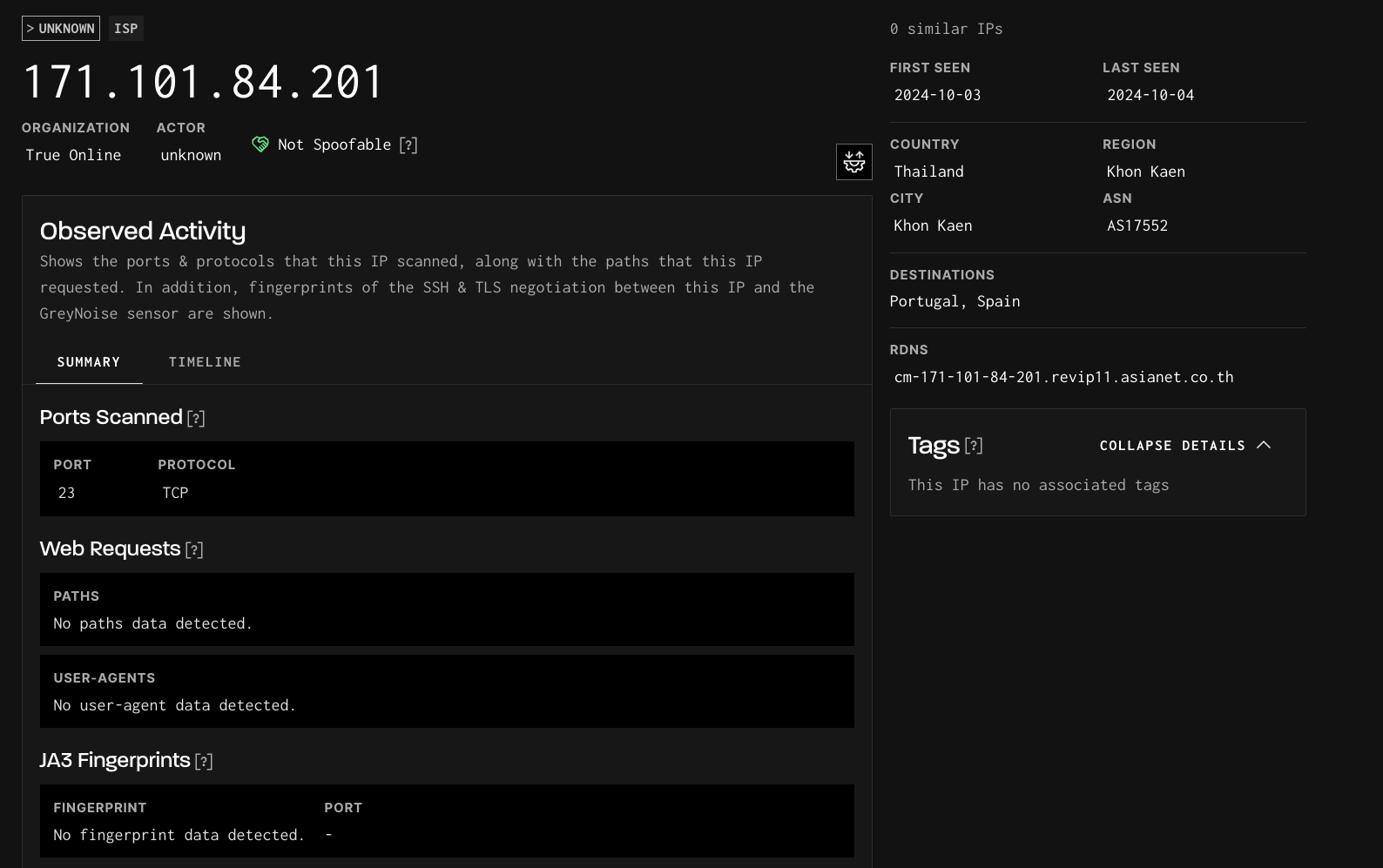
Unknown IP in the GreyNoise visualizer.
Contact UsDo you have a question about the classification of an IP? Do you see an issue with our data, tagging, or process? Please let us know: [email protected]
Updated 7 months ago
