IP Timeline
What is IP Timeline?
The GreyNoise IP Time Series (Timeline) shows GreyNoise's data on an IP address for up to 90 days. The information is available graphically on a tab of the IP details page in the GreyNoise Visualizer or as a JSON blob via the API.
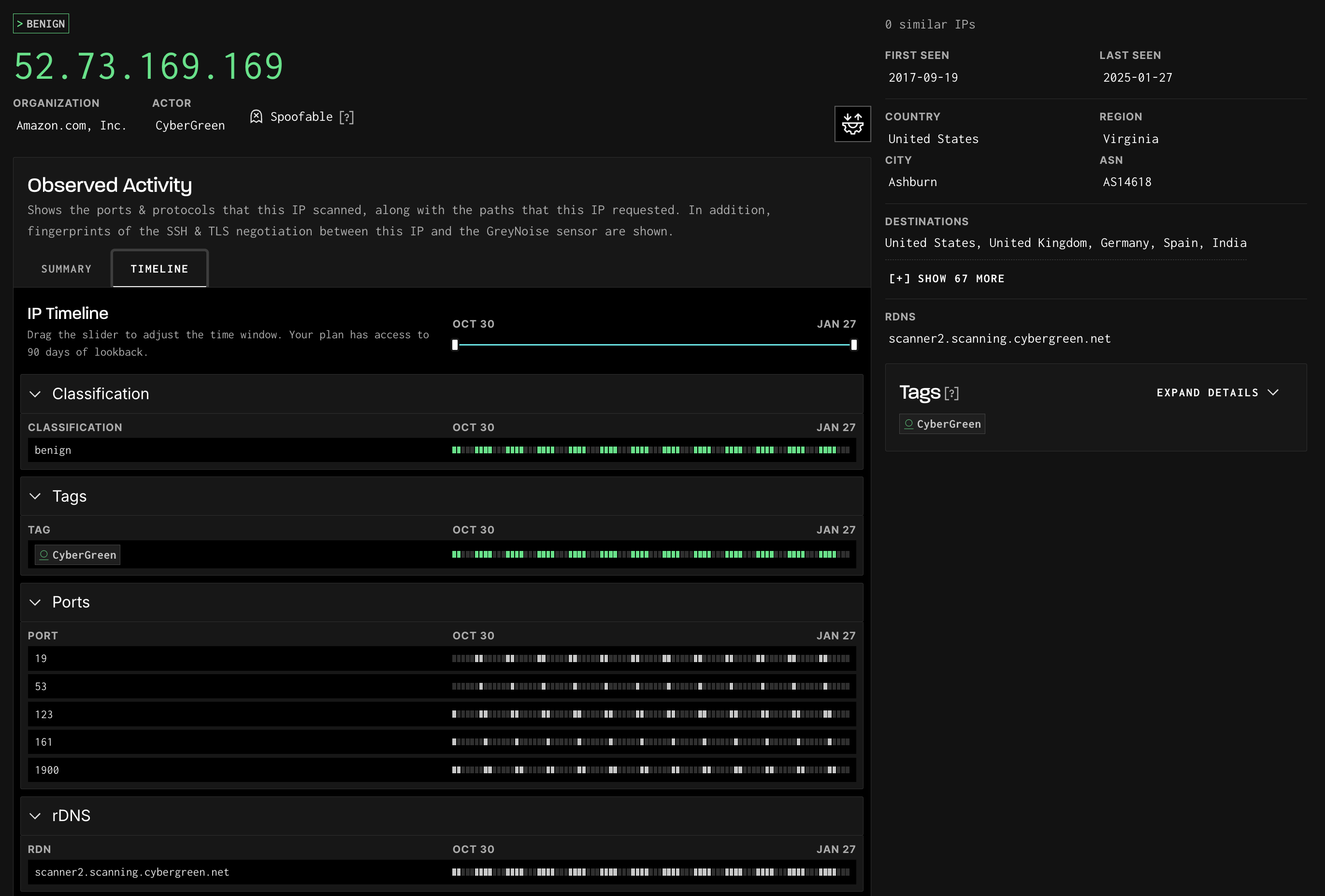
IP Timeline View
Why IP Timeline?
IP Time Series (Timeline) data provides context to when an IP has displayed behavior recorded by GreyNoise sensors. The GreyNoise Visualizer currently summarizes 90 days of IP behavior, while the Timeline displays 90 days of data, specifically by day. Users can correlate the behavior of an IP they have seen in their data, learn what schedule an IP operates on, or gain a greater understanding of ownership and behavioral changes.
How did we create IP Timeline?
A change in the GreyNoise infrastructure allowed for the exposure of event times to the user. An event is when an IP performs an action, and GreyNoise has enough information to expose meaningful content to the end user. Though an event sounds like a singular log, in GreyNoise data, there may be multiple log sources and enhancements to the data used to create an event. Examples of GreyNoise events include tagged events, recorded HTTP path events, JA3 handshake events, and HASSH events. Our data processing pipeline also has enrichment events that enhance the information shown to the end user.
What is IP Timeline not?
- A complete collection of events from the IP in the GreyNoise dataset. The Timeline only encompasses the past 90 days.
- An exact timestamp of IP behavior. Data buckets are by the hour.
How do I access IP Timeline in the Visualizer?
The IP Timeline view can be accessed by navigating to the IP Details page of the IP of interest, then select the Timeline Tab in the Observed Activity section.
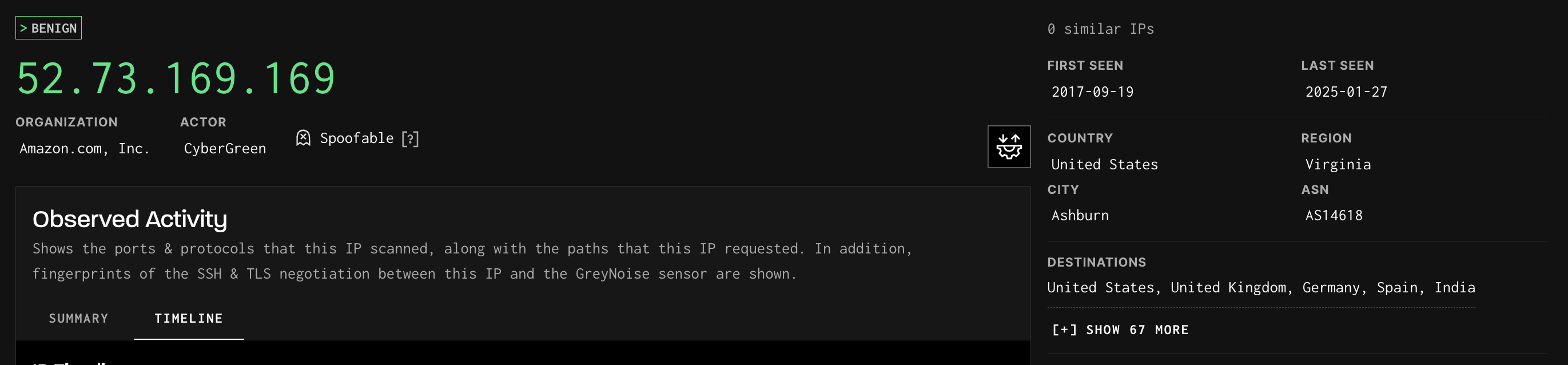
IP Timeline Tab
What's included in the IP Timeline UI?
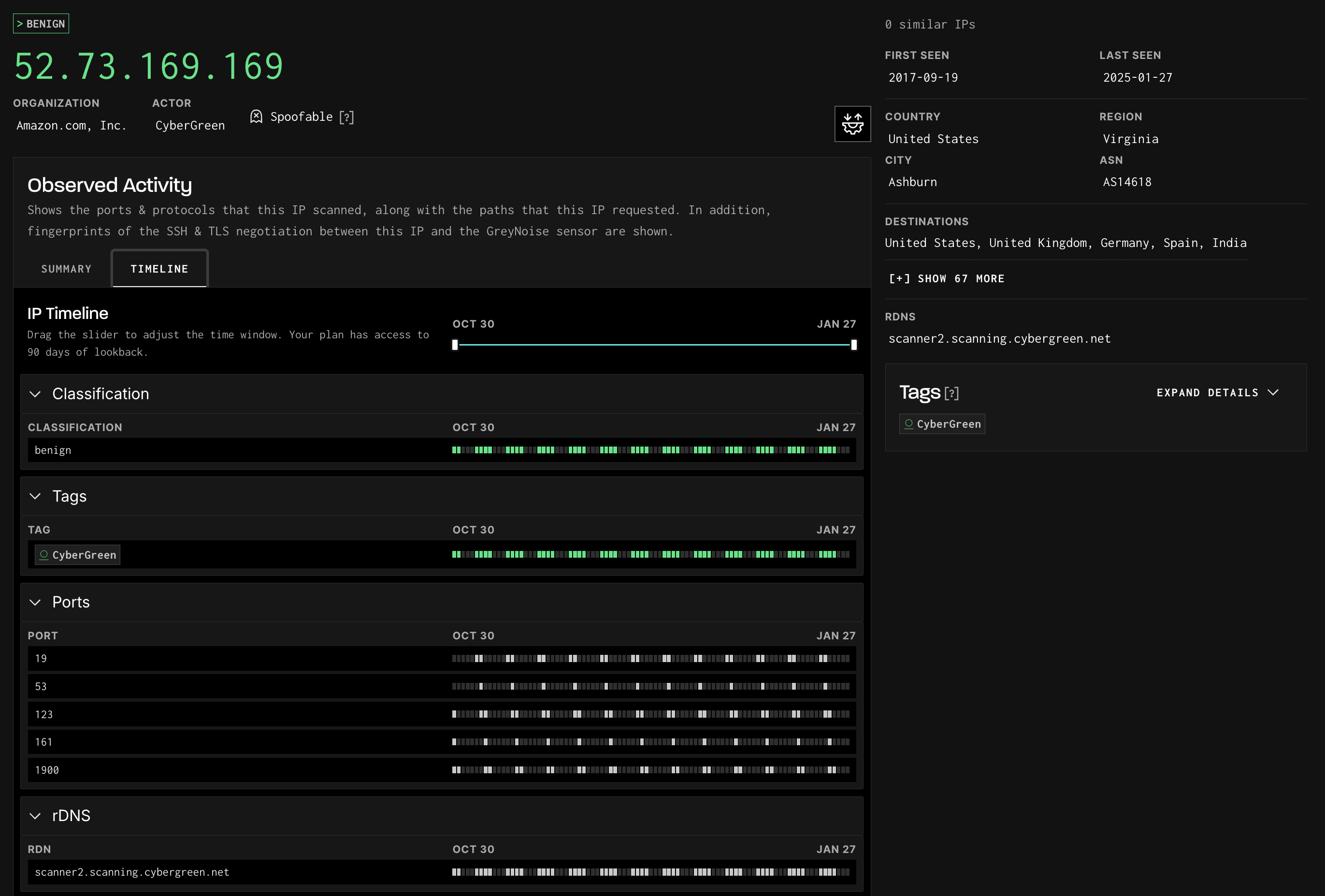
Daily Timeline
The IP Timeline view provides a daily breakdown of activity observed each day. The timeline indicates the current date range, which will include 90 days of activity history, then includes each of the days as a column in the view, with the most current date to the far right end of the table. A scrollbar on the table allows the view to be scrolled further back in time.
Date Selection Slider
At the top of the Timeline view, there is a blue slide bar that allows for the section of specific dates. This can be set to as little as one day or to a maximum of 90 days.
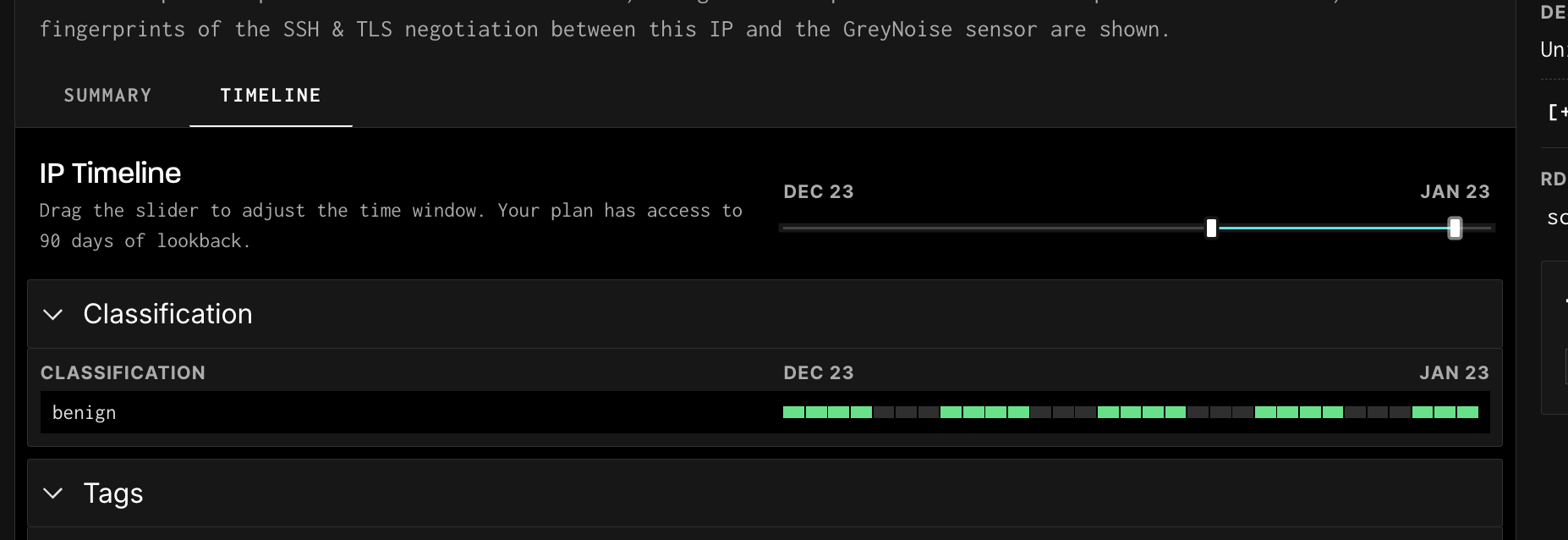
Classification Section
Shows the daily classification based on the tags present for that day.
Tags Section
Shows the tags observed and applied for each day. Currently, this display is limited to only 10 tags.
Ports
Shows the ports observed each day. Currently, this display is limited to only 10 tags.
Web Paths
Shows the web paths observed each day. Currently, this display is limited to only 10 tags.
User Agents
Shows the user-agents observed each day. Currently, this display is limited to only 10 tags.
rDNS
Shows the enriched rDNS value each day.
Organization
Shows the enriched organization value each day.
ASN
Shows the enriched ASN value each day.
Sections only Display when Data is Present
The individual sections within the Timeline view, such as rDNS, User Agent, etc. will only be present when data is available for those fields.
IP Timeline Responses in API
You can find the API spec for the IP Timeline API here: IP Timeline API Reference
{
"activity": [
{
"timestamp": "2022-11-21T01:00:00Z",
"country": "Ukraine",
"country_code": "UA",
"asn": "AS202580",
"region": "Kyiv City",
"city": "Kyiv",
"category": "hosting",
"datacenter": "",
"rdns": "",
"rdns_parent": "",
"rdns_validated": false,
"organization": "Bimeya LTD",
"vpn": false,
"vpn_service": "",
"tor": false,
"mobile": false,
"three_way_handshake": false,
"destinations": [
{
"country": "Australia",
"country_code": "AU"
},
{
"country": "Bahrain",
"country_code": "BH"
},
{
"country": "Brazil",
"country_code": "BR"
},
{
"country": "Canada",
"country_code": "CA"
},
{
"country": "India",
"country_code": "IN"
},
{
"country": "Singapore",
"country_code": "SG"
},
{
"country": "South Africa",
"country_code": "ZA"
},
{
"country": "South Korea",
"country_code": "KR"
},
{
"country": "United States",
"country_code": "US"
}
],
"protocols": [
{
"transport_protocol": "TCP",
"port": 10000,
"three_way_handshake": false
}
],
"classification": "malicious",
"tags": [
{
"id": "b183ced4-fafd-4ce5-8233-19af5f0837d3",
"slug": "webmin-rce-attempt",
"name": "Webmin RCE CVE-2019-15107",
"description": "IP addresses with this tag have been observed attempting to exploit CVE-2019-15107, a remote code execution vulnerability in some versions of Webmin.",
"category": "activity",
"intention": "malicious"
},
{
"id": "ac32bdeb-b49d-4079-9e6b-8fbca5e0addf",
"slug": "tls-ssl-scanner",
"name": "TLS/SSL Crawler",
"description": "IP addresses with this tag have been observed attempting to opportunistically crawl the Internet and establish TLS/SSL connections.",
"category": "activity",
"intention": "unknown"
},
{
"id": "79f609f0-4d07-455d-b9b1-56ff7c1a77a9",
"slug": "carries-http-referer-scanner",
"name": "Carries HTTP Referer",
"description": "IP addresses with this tag have been observed scanning the internet with an HTTP client that includes the Referer header in their requests.",
"category": "activity",
"intention": "unknown"
}
],
"ja3_fingerprints": [
"42ea9ce86effc99ac3305b3c203cccad"
],
"hassh_fingerprints": [],
"http_paths": [],
"http_user_agents": []
},
{
"timestamp": "2022-11-21T02:00:00Z",
"country": "Ukraine",
"country_code": "UA",
"asn": "AS202580",
"region": "Kyiv City",
"city": "Kyiv",
"category": "hosting",
"datacenter": "",
"rdns": "",
"rdns_parent": "",
"rdns_validated": false,
"organization": "Bimeya LTD",
"vpn": false,
"vpn_service": "",
"tor": false,
"mobile": false,
"three_way_handshake": false,
"destinations": [
{
"country": "Brazil",
"country_code": "BR"
},
{
"country": "India",
"country_code": "IN"
},
{
"country": "United States",
"country_code": "US"
}
],
"protocols": [
{
"transport_protocol": "TCP",
"port": 10000,
"three_way_handshake": false
}
],
"classification": "malicious",
"tags": [
{
"id": "79f609f0-4d07-455d-b9b1-56ff7c1a77a9",
"slug": "carries-http-referer-scanner",
"name": "Carries HTTP Referer",
"description": "IP addresses with this tag have been observed scanning the internet with an HTTP client that includes the Referer header in their requests.",
"category": "activity",
"intention": "unknown"
},
{
"id": "ac32bdeb-b49d-4079-9e6b-8fbca5e0addf",
"slug": "tls-ssl-scanner",
"name": "TLS/SSL Crawler",
"description": "IP addresses with this tag have been observed attempting to opportunistically crawl the Internet and establish TLS/SSL connections.",
"category": "activity",
"intention": "unknown"
},
{
"id": "b183ced4-fafd-4ce5-8233-19af5f0837d3",
"slug": "webmin-rce-attempt",
"name": "Webmin RCE CVE-2019-15107",
"description": "IP addresses with this tag have been observed attempting to exploit CVE-2019-15107, a remote code execution vulnerability in some versions of Webmin.",
"category": "activity",
"intention": "malicious"
}
],
"ja3_fingerprints": [
"42ea9ce86effc99ac3305b3c203cccad"
],
"hassh_fingerprints": [],
"http_paths": [],
"http_user_agents": []
},
{
"timestamp": "2022-11-21T12:00:00Z",
"country": "Ukraine",
"country_code": "UA",
"asn": "AS202580",
"region": "Kyiv City",
"city": "Kyiv",
"category": "hosting",
"datacenter": "",
"rdns": "",
"rdns_parent": "",
"rdns_validated": false,
"organization": "Bimeya LTD",
"vpn": false,
"vpn_service": "",
"tor": false,
"mobile": false,
"three_way_handshake": false,
"destinations": [
{
"country": "Poland",
"country_code": "PL"
}
],
"protocols": [
{
"transport_protocol": "TCP",
"port": 10000,
"three_way_handshake": false
}
],
"classification": "unknown",
"tags": [],
"ja3_fingerprints": [],
"hassh_fingerprints": [],
"http_paths": [],
"http_user_agents": []
}
],
"metadata": {
"start_time": "2022-11-20T00:00:00Z",
"end_time": "2022-11-21T19:18:34.743493679Z",
"ip": "45.141.156.66",
"limit": 50,
"next_cursor": "b2Zmc2V0PTUw"
}
}Updated 3 days ago
